Ploutus-D ATM Malware Reported in U.S.

Ploutus-D is malware used for ATM jackpotting. It was discovered in Mexico in 2013, and is now getting reported as reaching the U.S. by Krebs on Security. This attack has been analysed by FireEye in 2017, showing some of the technical details behind the ATM attack and how the offenders might take advantage of physical access to dump money from an ATM.
Based on the reports, the attackers must first gain physical access to the ATM to install the malware. The first line of defense against this attack is a good physical security program to prevent unauthorized users from gaining physical access to the machine. Krebs on Security has published the Diebold Nixdorf security alert with mitigations recommended by Diebold Nixdorf.
Tenable can help with detecting the malware on infected ATMs, including both currently infected ATMs and ATMs that have malware infections which were not sufficiently cleaned.
Malicious Process Detection
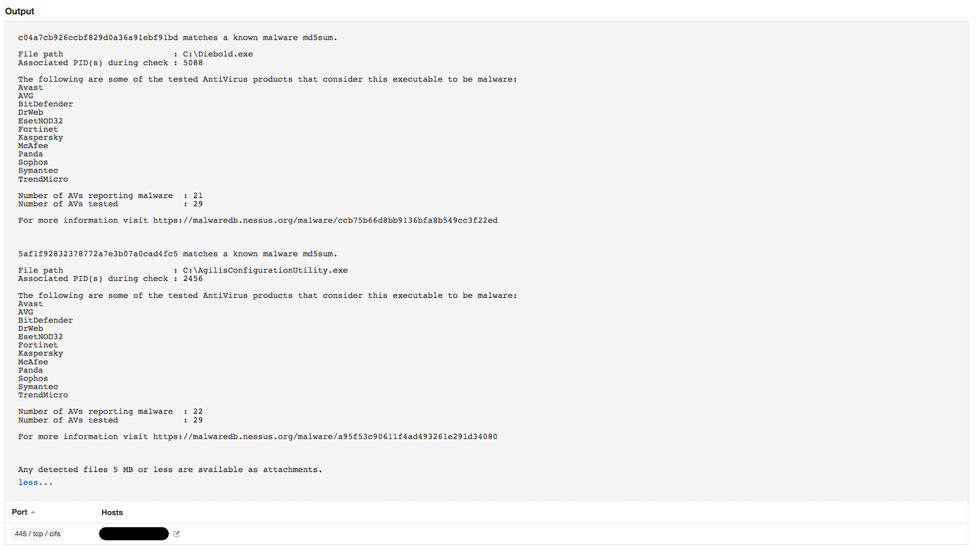
Running Plugin 59275, Malicious Process Detection detects if the malware is currently running on the system.
Running Plugin 88961, Malicious File Detection against the file system detects the infection on disk.
Indicators of Compromise Detection
Using Indicators Of Compromise (IOCs), you can detect if you’re currently infected. Additionally, left-behind remnants of a previous infection may also be reported.
Detect the registry entry “\\HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit=”Diebold.exe,%system32%/userinit.exe”:
- Plugin 70629, Microsoft Windows AutoRuns Winlogon
Detect the service “DIEBOLDP”:
- Plugin 70626, Microsoft Windows AutoRuns Services and Drivers
Detecting process “Diebold.exe”:
- Plugin 70329, Microsoft Windows Process Information
- Plugin 77668, Windows Prefetch Folder
- Plugin 92423, Windows Explorer Recently Executed Programs
- Plugin 92424, MUICache Program Execution History
Look at processes showing up as unsigned:
- Plugin 104856, Malicious Process Detection: Authenticode Not Signed
결론
Jackpotting attacks such as Ploutus have been observed in the U.S. These attacks can be better mitigated with appropriate physical and software security controls. It’s yet another reminder to be aware of your Cyber Exposure. The time has long passed where servers in a data center and computers on employee’s desks are the only infrastructure an organization needs to include in its security program.
관련 기사
- Malware
- Plugins






