What’s New with CNAPPgoat?

Read about the newest, expanded features in the Tenable Cloud Security open source vulnerable-by-design tool for enhancing your security skills.
Hold on, new? Tenable Cloud Security released CNAPPgoat barely a month ago! That’s right, and the feedback has been rather amazing - thank you!
Our team has been hard at work providing new features to make installing and using CNAPPgoat even easier and to expand its coverage of modules and support for cloud providers.
Let’s dive right in.
Recap: What is CNAPPgoat?
CNAPPgoat is Tenable Cloud Security’s open-source contribution to the multi-cloud environment landscape. It is a vulnerable-by-design deployment tool tailored for defenders and pentesters. By allowing intentional vulnerabilities to be seeded across AWS, Azure and GCP, we aim to provide a realistic setting for practitioners to enhance their skills.
GCP support
We’re proud to launch the first batch of scenarios relevant to Google Cloud Platform which is, of course, one of the main cloud service providers used in the market.
As specified in the CNAPPgoat main repository README.md, you’ll first need to authenticate to gcloud by executing the following command …
gcloud auth login… and going through the GCP authentication process.
After authentication, you will need to set the project ID for where you want to deploy your scenarios:
gcloud config set project <PROJECT_ID>Next, if you haven’t already - you should set a default region and zone for computing resources, like this:
gcloud config set compute/region <PREFERED_REGION>
gcloud config set compute/zone <PREFERED_ZONE>(You can also follow the instructions specified here or alternatively do this using environment variables as specified in the Pulumi documentation).
Once that’s done, you can start provisioning scenarios to GCP.
DSPM module
A significant category in the cloud security space is data protection – and I don’t think we need to explain why.
So we’re launching a new module, called DSPM, to hold data protection issue scenarios you can use to take your DSPM strategy for a spin.
Homebrew support
When we released CNAPPgoat (way back!) in August 2023 you still needed to download a released executable or compile the tool yourself to use it.
If you have homebrew available, you can install it with the following commands:
brew tap ermetic-research/cnappgoat
brew install cnappgoatImporting scenarios
You can now also import your own custom local scenarios, with ease.
All you need to do is have a specific directory with the scenarios’ material you created and then use the import-scenarios command; note that it’s a maintenance command. (For more information on how to create your own scenarios, please refer to the scenarios repo main README.md.)
In fact, as I write this, I have a scenario waiting to be approved in a Pull Request (PR) I made. Needing to deploy it will be a good opportunity for me to use this command to avoid adding myself manually to the ~/.cnappgoat/scenarios folder (which, to be honest, would be kind of tacky).
The way this would work is by running the following command:
cnappgoat maintenance import-scenarios -directory <PATH_TO_SCENARIOS_DIRECTORY>So in my case (and I assume yours won’t be much different) I simply point to where I have my fork of the scenarios repo and import it from there, producing the following output:

CNAPPgoat has detected my new scenario and imported it - very cool!
Note that if I were to change an existing scenario, CNAPPgoat would also detect that and overwrite the current version with my update - so pay attention to that.
Display scenario output
When you create a CNAPPgoat scenario, you can specify certain outputs that make it easier to use once provisioned.
In fact, in the above-mentioned scenario I’m working on, this is actually very important as the starting point of using it is a public IP address I want to get immediately so I don’t have to start querying the AWS CLI or console to get going.
When provisioning the scenario you may be able to see the output in the Pulumi log, which would look something like this:
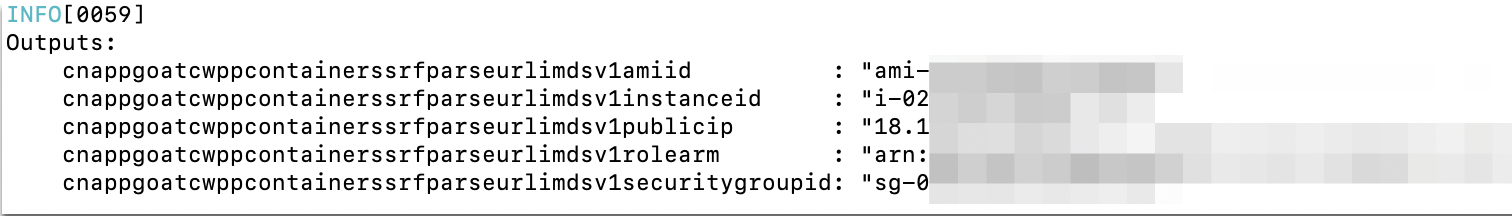
However, we’ve integrated a more elegant table display of this output, which can be very simply displayed using the command:
cnappgoat output <SCENARIO_ID>So in my case that would be:
cnappgoat output cwpp-aws-vulnerable-container-parse-url-on-ec2And the output generated looks like this:

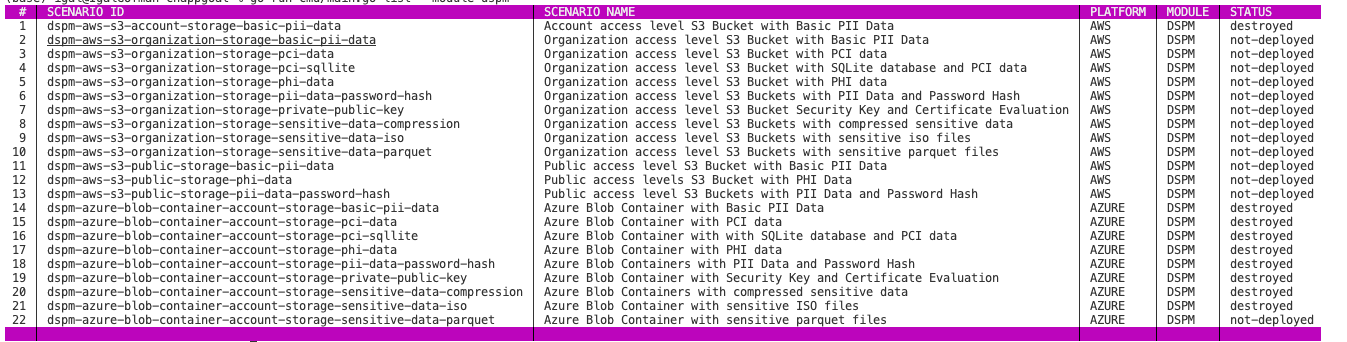
Filter scenarios by status
When you list scenarios, you can now filter the output based on their status: 'deployed' / 'destroyed' / 'error' / 'not-deployed'.
As the inventory of scenarios grows larger and larger, this feature can become very handy. For example, you can use it when running a large batch of scenarios and you want to see only those that had an error while CNAPPgoat attempted to provision them, or only those that are currently deployed (if, for example, you deployed them one at a time and can’t keep track).
Using this filter is extremely simple, as you just add the “status” option to the list command, such as:
cnappgoat list --status deployedAnd you get a filtered list:

Find something missing? Let us know!
As you can see, we are working hard at making CNAPPgoat meet its ambitious goal of codifying vulnerable infrastructure in the cloud and doing so in the most elegant and approachable way possible.
We’d love to hear what you think, and if there are any features or issues you’d be interested in, please let us know!
One more thing… If you want to learn more about how to write your own CNAPPgoat scenarios, stay tuned - we are publishing a detailed guide in a few days!
Related Articles
- Cloud
- Cloud






