WP Statistics WordPress Plugin Vulnerable to Unauthenticated Blind SQL Injection

Popular WordPress Plugin with over half a million installations is potentially vulnerable to unauthenticated blind SQL injection attacks.
Background
On July 1, maintainers of WP Statistics, a popular WordPress plugin for gathering website statistics about visitor data that boasts over 500,000 active installations, released an update to address a serious vulnerability.
분석
Researcher Thomas Chauchefoin discovered and reported an unauthenticated blind SQL injection (SQLi) in the WP Statistics plugin versions 12.6.6.1 and lower. The vulnerability exists in a non-default configuration of the plugin. By default, the Cache Plugin setting in WP Statistics is disabled.
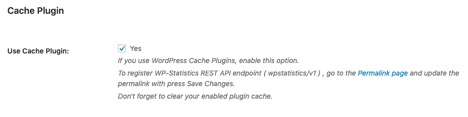
However, enabling this setting could allow an unauthenticated remote attacker to pass a blind SQLi command via the WP Statistics API endpoint. Since the SQLi vulnerability affects both SELECT and UPDATE queries, this could potentially be abused to perform a variety of actions, including changing the administrator credentials, adding another administrator account to the vulnerable WordPress site, exfiltrating user data and more.
This isn’t the first SQLi discovered in the WP Statistics plugin. Researchers at Sucuri blogged about their discovery of an SQLi in 2017, and researcher Marcin Probola discovered a blind SQLi in the plugin back in 2015.
Proof of concept
A proof-of-concept (PoC) was shared by the researcher in the WP Vulnerability database posting.
솔루션
This vulnerability is addressed in WP Statistics version 12.6.7 or greater. While the vulnerable configuration is not enabled by default, with over a half a million active installations it is likely that a large number of WP Statistics users are vulnerable. All users should upgrade to the latest version of the plugin as soon as possible.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 60-day trial of Tenable.io Vulnerability Management.
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning


