Fortify your security posture with Tenable OT Security
Vulnerability Management. Scan your IT, OT, and IoT assets for 79,000+ vulnerabilities. Detect cyber threats, malicious insiders, and more.
OT Scanning. Maximize your operational environment’s visibility, security, and control for SCADA systems, PLCs, DCS, IED, HMIs, and other assets across IT, OT, and IoT.
Reporting and Risk Intelligence. Access proven security tools and reporting capabilities for IT and OT teams, providing unmatched visibility into converged IT/OT segments and industrial networks in a single pane of glass.
데모 요청
필요한 운영 기술 보안을 갖추십시오.
불필요한 위험을 줄이십시오.
Vulnerability Management. Scan your IT, OT, and IoT assets for 79,000+ vulnerabilities. Detect cyber threats, malicious insiders, and more.
OT Scanning. Maximize your operational environment’s visibility, security, and control for SCADA systems, PLCs, DCS, IED, HMIs, and other assets across IT, OT, and IoT.
Reporting and Risk Intelligence. Access proven security tools and reporting capabilities for IT and OT teams, providing unmatched visibility into converged IT/OT segments and industrial networks in a single pane of glass.
Tenable은 44,000곳 이상의 고객과 Fortune 500의 60%를 보호

$1천만+
공장 중단과 관련하여 단 하루의 가동 중지로 인해 발생하는 비용입니다.
<5%
IIoT 장치와 시스템의 보안을 유지하는 회사의 능력에 자신 있다고 말한 OT 전문가의 비율입니다.
Why choose Tenable OT Security?
Access market-leading OT vulnerability management capabilities,
purpose-built to help
secure your operations

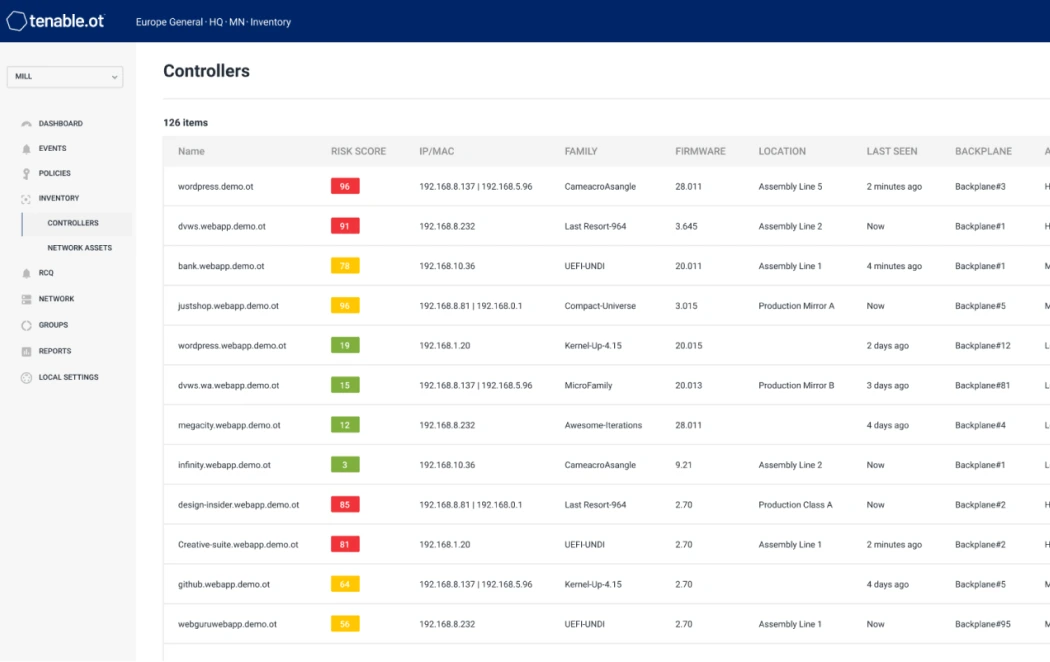
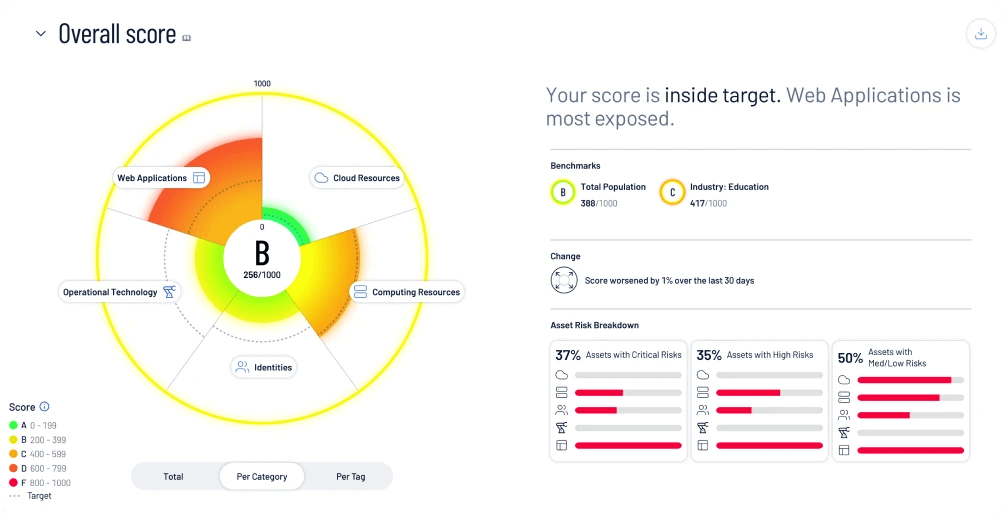
Get complete visibility across your entire attack surface

Automation
Ecosystem integration
Tenable OT Security integrates with leading Access Control Systems, SIEM, SOAR, next generation firewalls and diode based firewalls in order to provide insights to personnel outside of OT specific titles. Tenable OT Security also works in cooperation with the larger Tenable product portfolio including Tenable Security Center, Tenable Vulnerability Management and Tenable Identity Exposure.


Tenable OT Security also works in cooperation with the broader Tenable One portfolio, including Tenable Security Center, Tenable Vulnerability Management, and Tenable Identity Exposure.
Key features








