Tenable Identity Exposure secures active directory and eliminates attack paths
Tenable Identity Exposure secures active directory and eliminates attack paths
-
Decrease identity risk and secure human and machine identities with best practices for preventative Active Directory Security.
-
Unified view of identities across Active Directory and Entra ID (Formerly Azure Active Directory) deployments.
-
Enhance your ITDR (Identity Threat Detection and Response) capability by auditing Active Directory directory changes in real time and establishing timelines for indicators of attack.
-
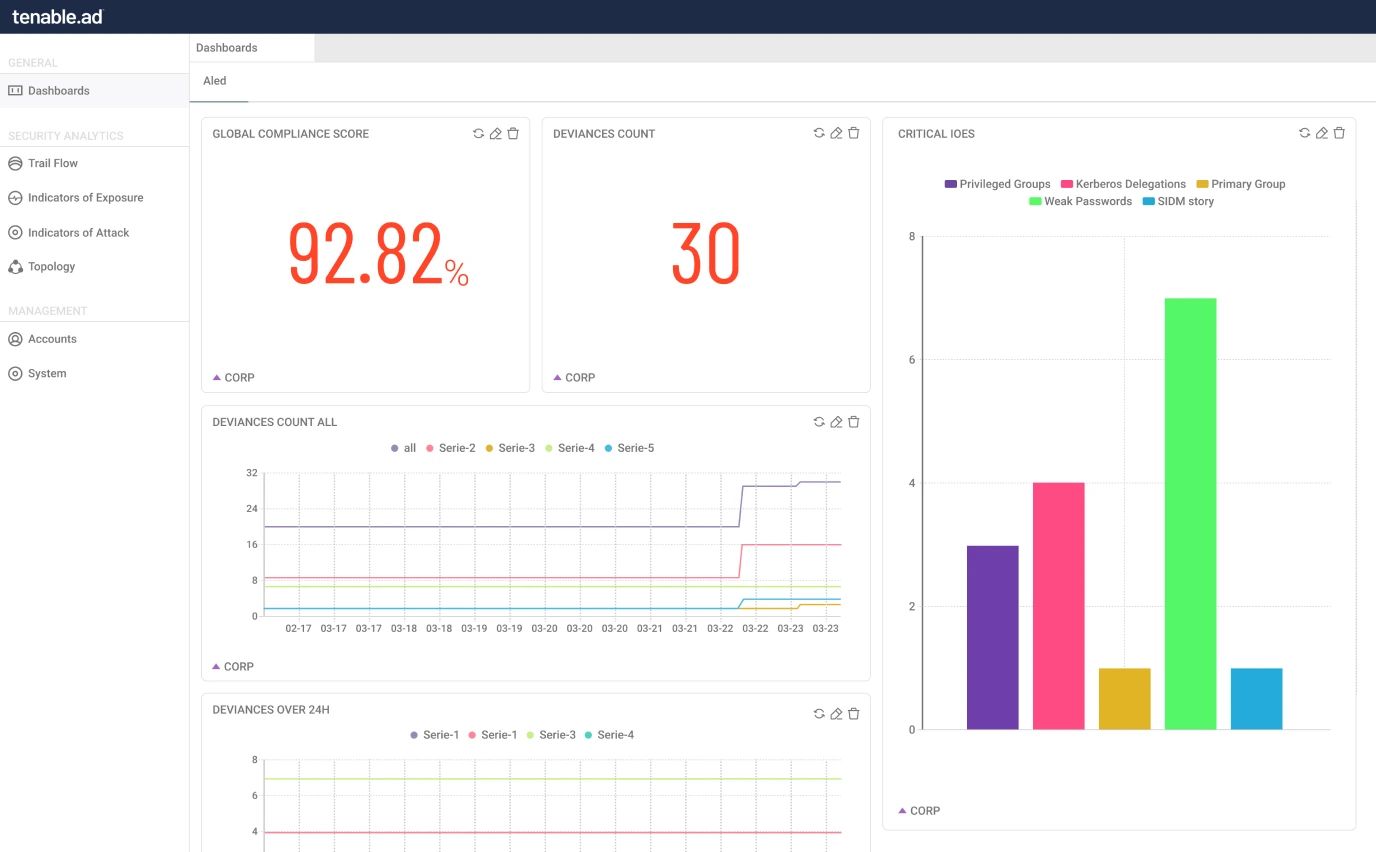
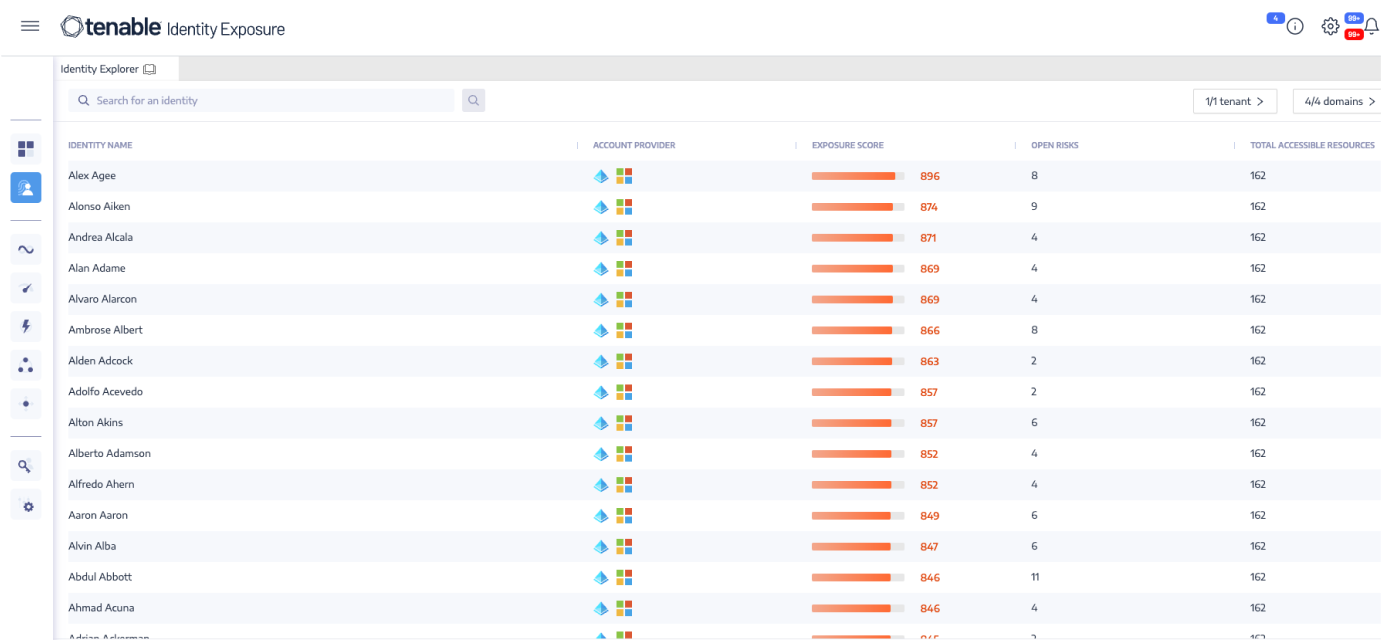
Exposure management is based on calculated identity risk scores, focusing on areas of highest risk.
-
Continuous validations and assessment of AD for attack prevention and detection.
데모 요청
Tenable customers - 65% of the Fortune 500 trust Tenable
With Tenable Identity Exposure, you'll always have:
Tenable Identity Exposure benefits
With Tenable Identity Exposure, you'll always have:

Identity unification and
AI-driven risk scoring
Active Directory, 하이브리드 및 Entra ID 계정을 단일 보기로 모두 통합합니다.Gain control of identities dispersed between multiple directory services, domains and forests in a single view. Prioritize remediation with our data-science backed identity risk score that ranks identities by level of risk to the environment. Optimize team efficiency and focus efforts on risk mitigation and preventing attacks.
Expand
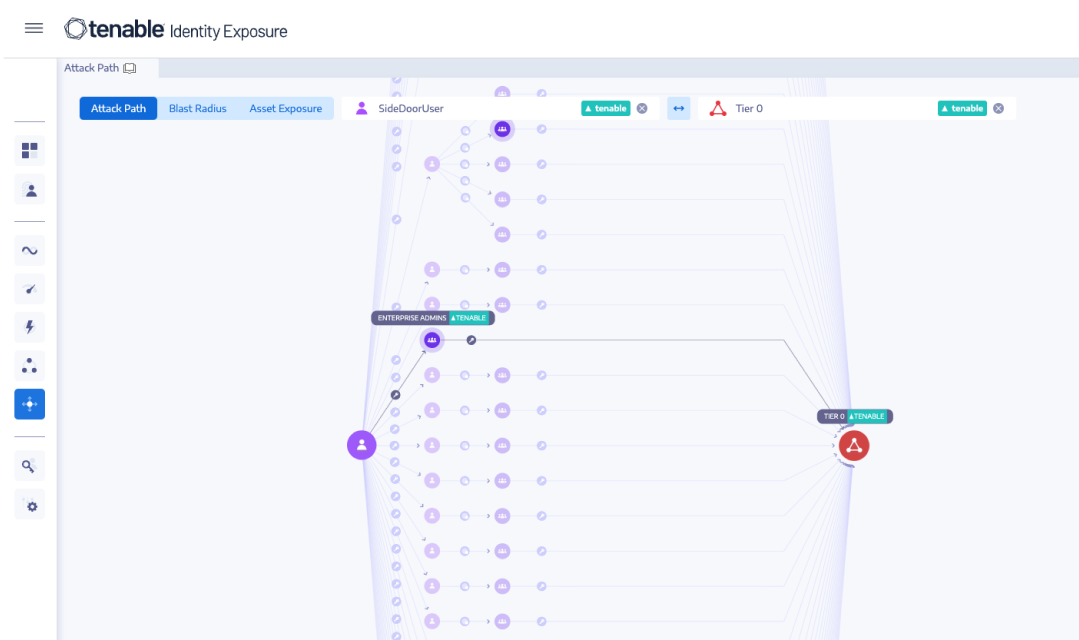
Eliminate attack paths that lead to domain domination
Make sense of the complex interrelationships between objects, principals, and permissions, and eliminate attack paths that lead to domain dominance. Attack path analysis surfaces all the possible steps that attackers could take to move laterally, escalate privileges, and gain control over your enterprise directory services.
Expand
Continually assess directory services security in real-time
디렉터리 서비스의 보안 포스처를 평가하고 취약성, 위험한 구성 및 권한 크리프를 파악합니다.Tenable Identity Exposure provides a step-by-step tactical guide that identifies affected objects, eliminating the need for time-consuming manual reports or scripts, hardening AD and Entra ID.
Expand
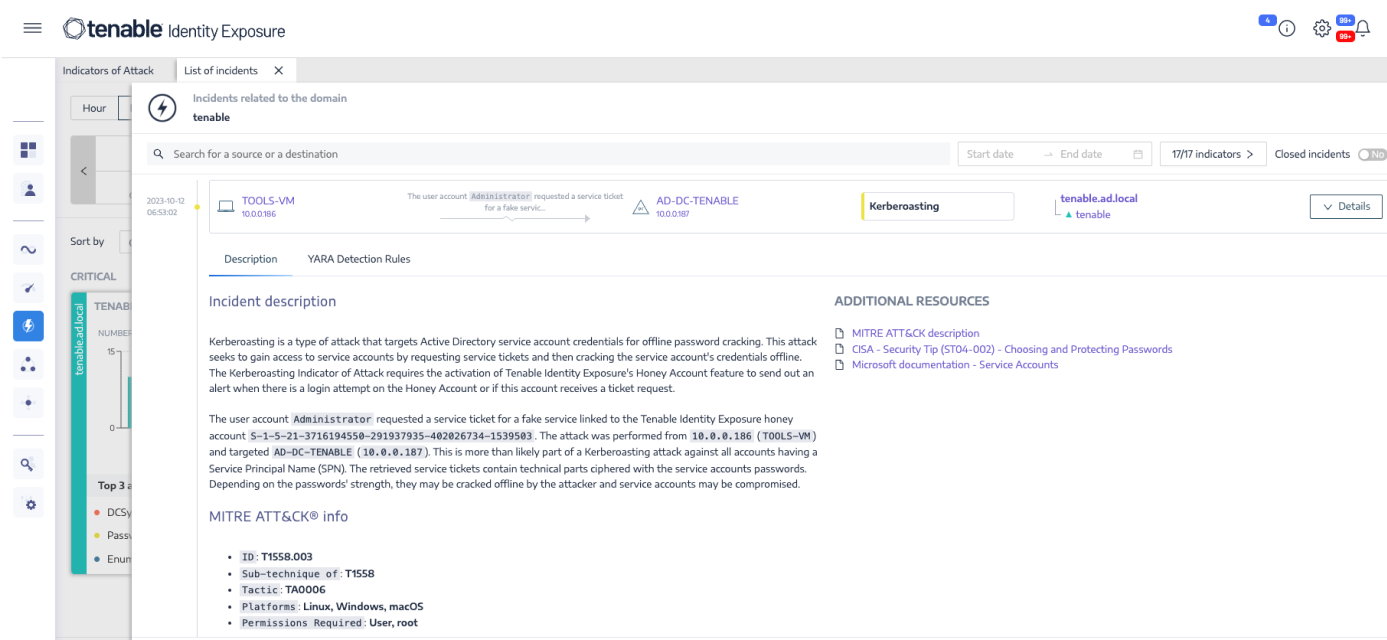
Real-time attack detection
Receive instant alerting against indicators of attack, including credential dumping, Kerberoasting, DCSync, ZeroLogon, and many more. Respond to attacks in real time by integrating Tenable Identity Exposure with your SIEM and SOAR. Tenable’s research team regularly updates indicators of attack as new identity-based exploits are discovered.
Expand
Investigate and inform
Reduce MTTR (mean time to respond) and audit active directory by capturing all changes to Active Directory using Trail Flow. Inform your incident response teams and enrich your security operations processes with real-time prioritization and detailed remediation steps.
Expand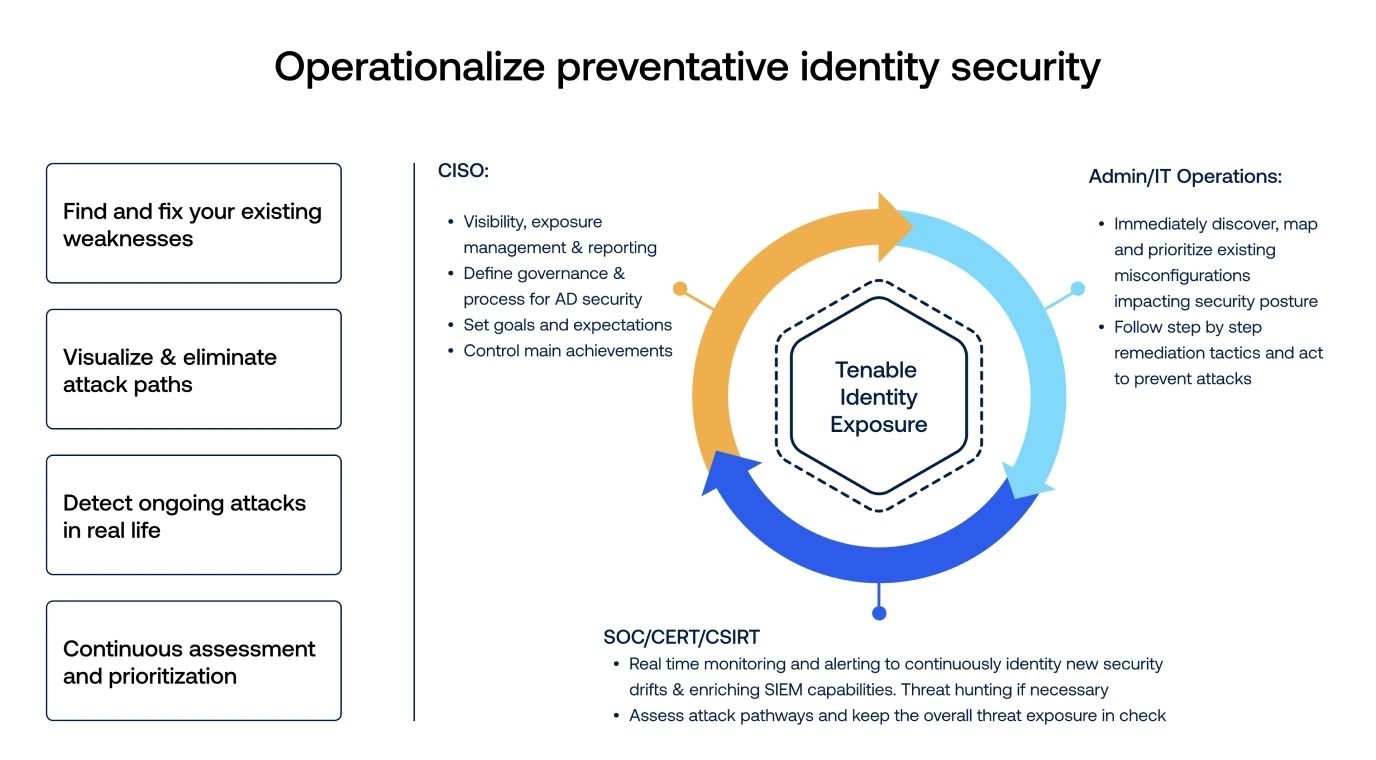
Introduction to Tenable Identity Exposure and Identity Aware Exposure Management
A quick walkthrough of Tenable Identity Exposure highlighting why Identity aware exposure management provides critical context to prioritize cyber security remediation efforts.
Continuously detect
and prevent active directory attacks
-
에이전트 필요 없음.No privileges.
지연 없음에이전트와 권한 없이 정교한 Active Directory 공격을 방지하고 탐지합니다.
-
Clouds covered
Extended support for protecting public and hybrid cloud Azure Active Directory deployments and managing cloud identity risk with Indicators of Exposure specific to Azure AD.
-
어디든지 배포
Tenable Identity Exposure는 두 가지 아키텍처 설계의 유연성을 제공합니다. 온프레미스는 데이터를 사이트에 유지하고 데이터를 제어할 수 있습니다. SaaS로 클라우드를 활용할 수 있습니다.