by Stephanie Dunn
May 12, 2016
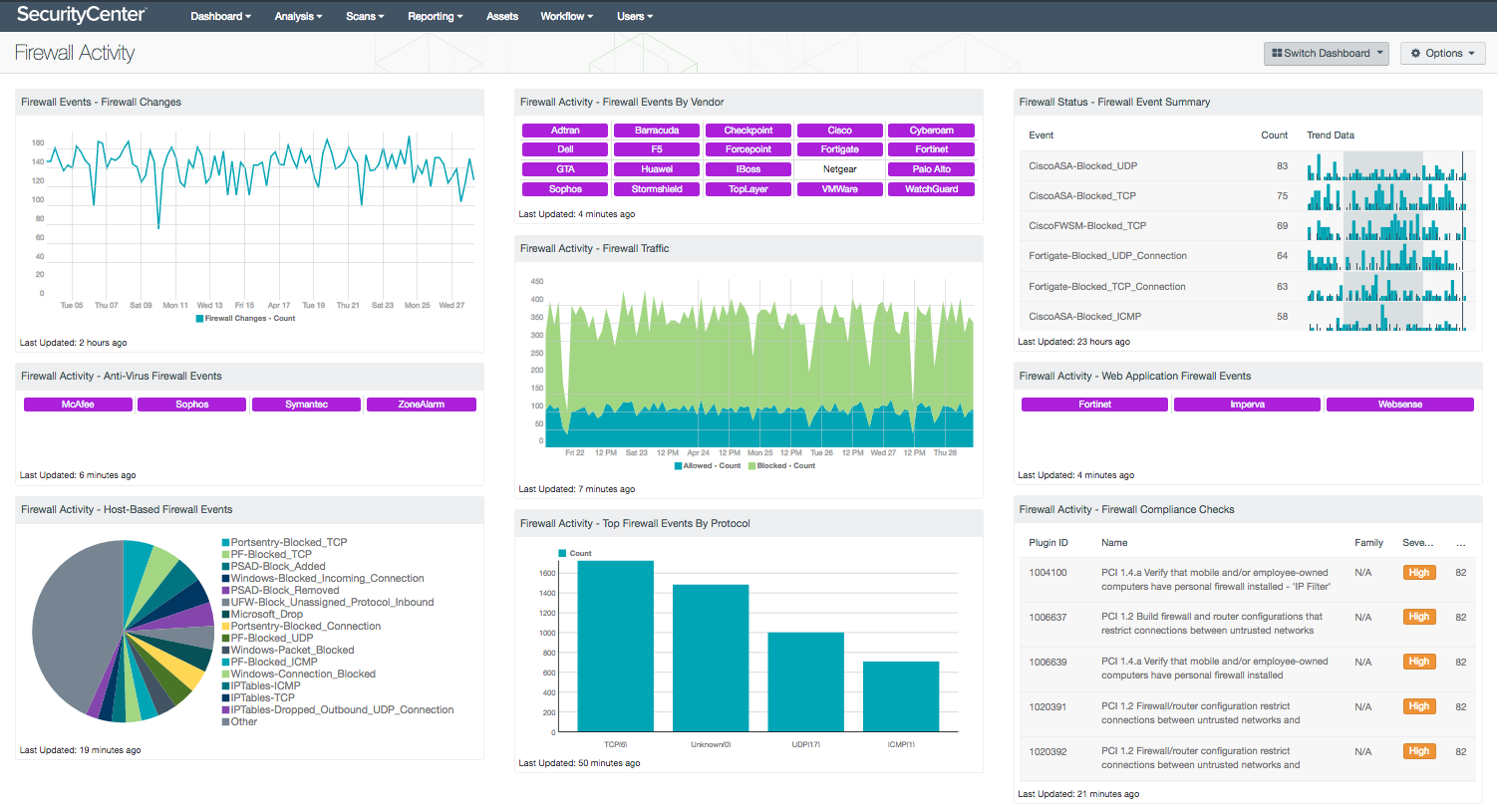
Firewalls provide one of the most critical security layers need to protect networks against targeted attacks and advanced persistent threats. Having proper security controls in place will allow an organization to detect and respond to threats before critical systems are affected. Using this dashboard, security teams will be able to effectively detect and respond to threats before critical systems are affected.
Most organizations use a combination of firewall appliances, web application firewalls (WAF), and host-based firewalls to monitor and prevent malicious traffic or attackers from gaining access to internal hosts. Many firewall solutions provide stateful inspection, which analyzes inbound and outbound packets and matches that information against firewall rules. Having proper access control rules in place will help to reduce the chance of attackers bypassing the firewall. Unknown firewall changes can also introduce additional security risks, and leave devices and systems vulnerable to attack. Along with firewalls, organizations should also have IDS/IPS and anti-virus solutions in place as apart of a comprehensive defense in depth strategy. This strategy will allow for multiple devices and services to protect the network in case one layer is breached. Continuous monitoring of network devices and systems will provide organizations with the ability to prioritize and respond to threats, as well as reduce overall security risks.
Nessus offers the most extensive library of compliance checks available that can be customized to deliver relevant, accurate information that will meet specific compliance requirements. Many audit files such as CIS, DISA STIG, PCI DSS, and more, all provide firewall compliance checks. Security teams should a complete review the audit files needed to support compliance requirements.
This dashboard provides organizations with a centralized view of firewall related events on the network. Firewall devices and applications can generate millions of events per day, and provide evidence of malicious activity that may be a result of malware or other suspicious activity. Components within this dashboard will indicate to analysts to firewall-based events from vendor specific firewall appliances, WAFs, and host-based firewalls within the network. Event data can help analysts identify ports being used within applications or services, as well as any unknown ports being used for malicious purposes. Compliance checks are also performed on systems, and will provide best practices for securing existing firewall devices and applications on the network. Security teams can use the information presented within this dashboard to quickly eliminate blind spots, strengthen existing firewall solutions, and maintain overall compliance.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 5.3.1
- Nessus 6.6.2
- LCE 4.8.0
- Compliance Data
- Local Checks
SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. SecurityCenter CV is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance audits. Tenable’s Log Correlation Engine (LCE) correlates real-time events, such as port scanning, and then performs analysis to discover vulnerabilities and Indicators of Compromise (IOC). SecurityCenter CV allows for the most comprehensive and integrated view of network health.
The following components are included in this dashboard:
- Firewall Events – Firewall Changes: The Firewall Changes component displays a 25-day trend of firewall change events. When the LCE normalizes logs from various firewalls, if the log indicates a change to the configuration, ACLs or user accounts, a 'Firewall_Change' event is generated. Event spikes may indicate configuration changes, rule modifications, policy changes on firewall devices and applications.
- Firewall Activity – Anti-Virus Firewall Events: This component presents a matrix of detected firewall events from commonly used anti-virus suites. Many anti-virus suites have firewalls applications build into anti-virus client packages. Firewalls can allow organizations to block traffic to websites, prevent devices from connecting to the network, and provide the ability to whitelist or blacklist certain applications or programs from running. For each indicator, when an event has been detected, the indicator will turn purple. Triggered events can alert analysts to blocked incoming or outgoing connections, blocked IP addresses, blocked ports, and more.
- Firewall Activity – Host-Based Firewall Events: This chart presents a list of the top host-based firewall events that have been detected within the last 72 hours. Host-based firewall applications consist of either built-in or free applications that can be downloaded and installed on the host. Firewall applications on Windows, Mac OS X, and Linux/Unix operating systems are covered within this chart. Information presented within this component will indicate to analysts dropped connections, blocked connections, and more. Event data can be modified per organizational requirements.
- Firewall Activity – Firewall Events By Vendor: The Firewall Events By Vendor matrix presents indicators of detected firewall events by vendor. Events detected within this component originate from logs generated by firewall appliances/devices. Each indicator includes vendor-specific normalized events, and is filtered by the “firewall” event type. When an event has been detected, the indicator will turn purple. These events may include activity such as blocked incoming or outgoing connections, discarded packets, blocked malicious IP addresses, and blocked ports. LCE provides a large selection of vendor-specific firewall normalized events. Indicators within this component can be modified per organizational requirements.
- Firewall Activity – Firewall Traffic: The Firewall Traffic chart presents a trend of allowed and blocked firewall events over the last seven days. The Allowed trend line events report on the “connection” event type and are filtered by “Allowed” and “Accepted” normalized events. The Blocked trend line events report on the “firewall” event type and include “Blocked”, “Deny”, “Rejected”, and “Drop” normalized events. Detected events include activity from IDS/IPS, web application firewalls, host-based firewalls, and firewall appliances whose logs are being forwarded to the LCE.
- Firewall Activity – Top Firewall Events By Protocol: The Top Firewall Events By Protocol chart displays total counts of firewall events from TCP, UDP and ICMP connections. Event data help analysts identify ports being used within applications or services, as well as any unknown ports being used for malicious purposes. This information can also indicate that systems are being “pinged” by internal applications or malicious outsiders for reconnaissance purposes. Analysts can drill down and set the tool to Port Summary or Raw Syslog Events to obtain additional information on the specific event.
- Firewall Status – Firewall Event Summary: This component displays the top 50 normalized firewall events by event count for firewalls from vendors such as Cisco, Juniper, Palo Alto, Fortinet, and many more. Each event will display the normalized event name, total event count, and trending data of this specific normalized event name. Using SecurityCenter CV for monitoring the different types of firewall events, a security analyst can determine if any malicious or suspicious firewall activity is occurring on the network.
- Firewall Activity – Web Application Firewall Events: The Web Application Firewall Events matrix presents indicators of detected web application firewall (WAF) events. Events detected within this component originate from logs generated by web application or software-based firewalls on the network. Each indicator includes vendor-specific normalized events, and is filtered by the “firewall” event type. When an event has been detected, the indicator will turn purple. These events may include activity such as blocked incoming or outgoing connections, discarded packets, blocked malicious IP addresses, and blocked ports. Indicators within this component can be modified per organizational requirements.
- Firewall Activity – Firewall Compliance Checks: The Firewall Compliance Checks component provides a summary of firewall compliance checks. Nessus uses a variety of audit files to check systems for firewall configuration controls. High severity denotes checks that have failed to meet the compliance threshold. Medium severity shows checks that need to be manually reviewed to assess their compliance state. Organizations should review current security policies and compliance requirements that are relevant to the organization. Each compliance check includes detailed information on the respective vulnerability that the analyst can immediately drill down into. This table can be modified to include additional or specific compliance checks based on organizational requirements.