by Michael Willison
August 8, 2014
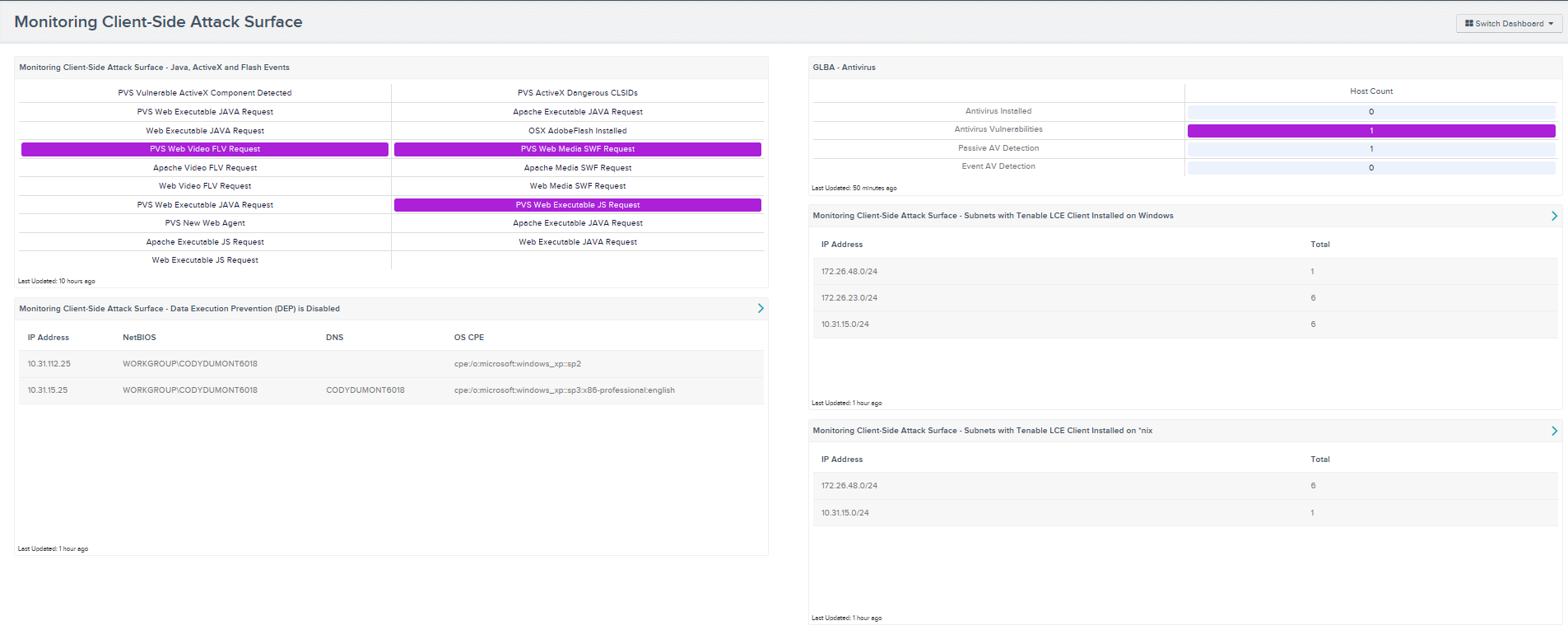
This dashboard monitors the client-side attack surface in an organization. A client-side attack surface is a combination of risk, vulnerabilities, or exploits from access points of which potential attackers can take advantage. These access points can be code that processes incoming data, email, web forms, SQL servers, and services available on the network. Applications such as Java, ActiveX, and Flash are commonly required when interacting with dynamic web pages on the internet or intranet. A couple of examples would be preventing ActiveX from trying to access a video on the internet by default, or reducing the amount of code executed that turns off features, which would lower the attack surface of applications or services. These are just a couple of examples of reducing the attack surface risk within an organization.
Using Tenable SecurityCenter Continuous View (CV) to monitor normalized events from the Log Correlation Engine (LCE), vulnerability scans from Nessus, and vulnerability monitoring with Passive Vulnerability Scanner (PVS), organizations can monitor client-side attack surfaces by focusing on the hardening of applications (Java, ActiveX, and Flash). SecurityCenter CV can monitor if applications have had their Data Execution Prevention (DEP) security features disabled, if anti-virus software is installed, or if anti-virus software has a vulnerability, a passive anti-virus event, or if an antivirus event has been detected. A security analyst would be able to monitor these events and determine which access points need to lower their client-side attack surface risk.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- SecurityCenter 4.8.1
- Nessus 5.2.7
- PVS 4.0.2
- LCE 4.2.2
Listed below are the included components:
- Monitoring Client-Side Attack Surface - Java, ActiveX and Flash Events: This matrix monitors for 19 normalized events that report on ActiveX, Java, and Flash events. The events included detect Flash Player requests, executable Java requests, and dangerous ActiveX controls. This information provides an analyst with easy access to suspected malicious events detected in syslogs.
- GLBA – Antivirus: The Antivirus dashboard component leverages the Nessus antivirus auditing plugins.
- Monitoring Client-Side Attack Surface - Data Execution Prevention (DEP) is Disabled: This component displays hosts that have Data Execution Prevention (DEP) security features disabled. By having DEP disabled, hosts may be susceptible to malicious exploits, especially attacks that store executable instructions in a data area via a buffer overflow. DEP is a security feature that prevents attackers from taking advantage of executables in memory. DEP marks memory as either "executable" or "non-executables ", and only allows data in the "executable" area to be run by applications, services, and device drivers. DEP is available in Linux, OS X, Microsoft Windows, and Android operating systems. DEP is enabled by default on all Windows operating system since Windows XP Service Pack 2.
- Monitoring Client-Side Attack Surface - Subnets with Tenable LCE Client Installed on Windows: This component displays the number of hosts that have the Log Correlation Engine (LCE) Client for Windows installed per subnet. LCE Clients are agents that are installed on Windows systems whose logs, network traffic, performance, and other types of protocols and technologies are to be monitored by forwarding the data securely to the LCE server.
- Monitoring Client-Side Attack Surface - Subnets with Tenable LCE Client Installed on *nix: This component displays the number of hosts that have the Log Correlation Engine (LCE) Client for *nix installed per subnet. LCE Clients are agents that are installed on *nix systems whose logs, network traffic, performance and other types of protocols and technologies are to be monitored by forwarding the data securely to the LCE server.