by Steve Tilson
June 6, 2014
The OpenSSL ChangeCipherSpec vulnerability is a Man-in-the-Middle attack that can allow an attacker modify the traffic between two hosts during a phase of an SSL/TLS handshake. This flaw could allow a MiTM attacker to decrypt or forge SSL messages by telling the service to begin encrypted communications before key material has been exchanged, which causes predictable keys to be used to secure future traffic. This dashboard identifies systems vulnerable to the OpenSSL ChangeCipherSpec vulnerability.
Man-in-the-Middle (MitM) vulnerabilities allow an attacker to insert themselves into a communication channel. While each of the endpoints assume they are communicating directly with each other, all the traffic is in fact flowing through the attacker. This type of hack allows the attacker to eavesdrop on or even modify the traffic being sent back and forth, resulting in a loss of data confidentiality and integrity.
MitM attacks are more common in unsecured or poorly secured Wi-Fi environments. These types of connections are generally found in public areas with free Wi-Fi hotspots. These types of attacks can be avoided in a several ways, such as using "HTTPS" in the URL in conjunction with recognized authentication certificates, staying clear of public Wi-Fi or using a Virtual Private Network (VPN) if needed. Many MitM attacks utilize malware and making sure systems are up to date and the network is secure will further reduce the risk. Additionally, email has been known for the MitM attacks. Using encryption and not clicking on suspicious emails or links in emails will further reduce risk to MitM attacks.
This vulnerability was published in 2014 and affects all versions of OpenSSL prior to 0.9.8y, OpenSSL 1.0.0 through 1.0.0l, and OpenSSL 1.0.1 through 1.0.1g. OpenSSL 1.0.1 is known to be exploitable. OpenSSL 0.9.8 and 1.0.0 are not known to be vulnerable; however, the OpenSSL team has advised that users of these older versions upgrade as a precaution. SecurityCenter CV detects and reports all versions of OpenSSL that are potentially exploitable.
The report and elements are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The report can be easily located in the SecurityCenter Feed under the category Security Industry Trends.
The report requirements are:
- SecurityCenter 5.2.0
- Nessus 6.11.2
- NNM 5.4.0
- LCE 5.0.2
Tenable SecurityCenter Continuous View® (SecurityCenter CV™) provides continuous network monitoring, vulnerability identification and security monitoring. SecurityCenter CV™ is continuously updated with information about advanced threats, zero-day vulnerabilities and new types of regulatory compliance configuration audit files. Tenable constantly analyzes information from unique sensors, delivering continuous visibility and critical context, and enabling decisive action that transforms a security program from reactive to proactive. Active scanning periodically examines the applications on the systems, the running processes and services, web applications and configuration settings. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. SecurityCenter CV™ provides an organization with the most comprehensive view of the network and actionable information to support mitigation efforts and reduce cyber risk. Managers can better monitor and asses Microsoft patch management happening across the network with SecurityCenter CV™. Tenable enables powerful, yet non-disruptive, continuous monitoring that will provide organizations with the information needed to reduce risk within the enterprise.
This dashboard provides SecurityCenter customers with a summary of the vulnerabilities recently discovered within OpenSSL. There are six CVEs related to this new vulnerability. They are:
CVE-2014-0224 - SSL/TLS MITM Vulnerability
CVE-2014-0221 - DTLS recursion flaw
CVE-2014-0195 - DTLS invalid fragment vulnerability
CVE-2014-0198 - SSL_MODE_RELEASE_BUFFERS NULL pointer dereference
CVE-2010-5298 - SSL_MODE_RELEASE_BUFFERS session injection
CVE-2014-3470 - Anonymous ECDH Denial of Service
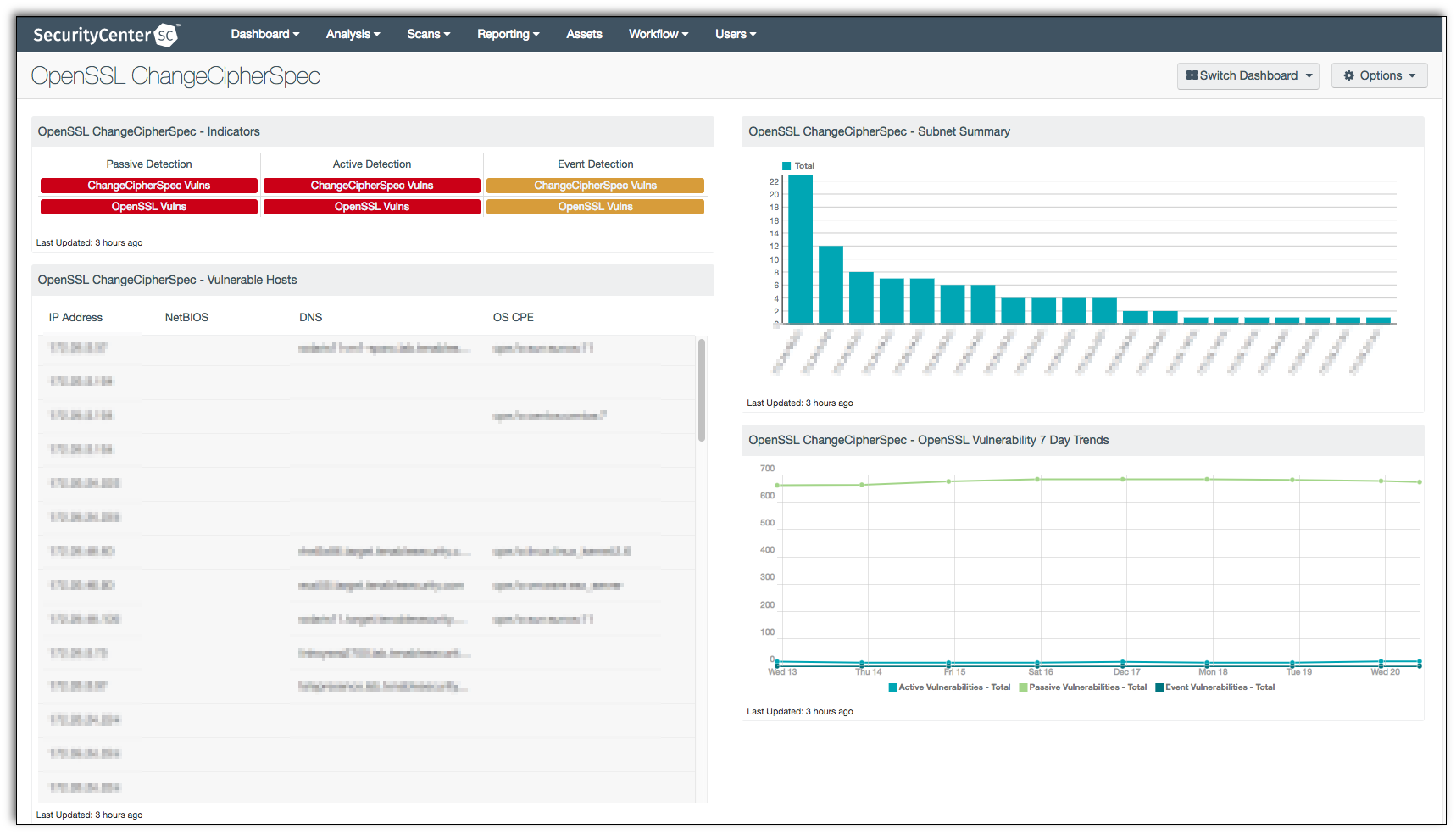
This dashboard contains four components, three of which focus on the six CVEs related to the OpenSSL ChangeCipherSpec vulnerability. The remaining component focuses on OpenSSL vulnerabilities.
OpenSSL ChangeCipherSpec - Indicators: This component provides an overview of OpenSSL vulnerabilities and the related ChangeCipherSpec vulnerabilities. There are three columns, one for each vulnerability type (active, passive, event). Each column has an indicator for the six CVEs related to OpenSSL ChangeCipherSpec vulnerability, and one indicator for all OpenSSL related vulnerabilities. The active and passive indicators will turn red, signifying immediate action should be taken, while the event vulnerabilities are orange and signify that administrators should investigate the true severity of the event.
OpenSSL ChangeCipherSpec - Vulnerable Hosts: This component provides a table of all the systems vulnerable to the six CVEs related to OpenSSL ChangeCipherSpec.
OpenSSL ChangeCipherSpec - Subnet Summary: This component provides a chart showing the count per subnet of all the systems vulnerable to the six CVEs related to OpenSSL ChangeCipherSpec.
OpenSSL ChangeCipherSpec - OpenSSL Vulnerability 7 Day Trends: This component provides a chart showing a 7 day trend analysis of systems with OpenSSL vulnerabilities, with a separate trend line for each plugin type.