by Josef Weiss
November 5, 2015
A common implementation of firewalls is to protect network devices by analyzing data moving in and out of the organization, restricting unauthorized access and malicious traffic. The firewall barrier is a critical control in effectively monitoring traffic both in and out of an organization.
A task common to many security programs is to monitor and analyze logs and events from security devices such as firewalls. Reviewing the organization’s firewall solution ensures the implementation is running smoothly. Monitoring firewall logs is a critical task in security operations, and facilities the identification of security concerns and related issues. The Palo Alto Firewall dashboard allows security administrators to view a summary status of firewall information, and includes indicators for events, configuration audits, and NetFlow statistical graphs in a single location within Tenable.sc. The continuous monitoring of firewalls allows the analyst to quickly identify important event data, without having to log into multiple devices. Problems can be rapidly identified, and a workflow can be easily created to escalate potential concerns.
Using the correlation features of LCE and Nessus audit checks, the Palo Alto Firewall dashboard highlights the native ability of Tenable.sc to monitor the status of other security products. By collecting this information, a security analyst can review the configuration and traffic status of the firewall without requiring firewall management privileges.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Monitoring.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.6.0
- LCE 6.0.0
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new types of regulatory compliance configuration audits. LCE correlates real-time events, such as DNS queries, then performs analysis to discover vulnerabilities and Indicators of Compromise (IOC). LCE also has the capability to discover users, operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and other critical infrastructure. Tenable.sc CV allows for the most comprehensive and integrated view of network health.
The collection contains the following components:
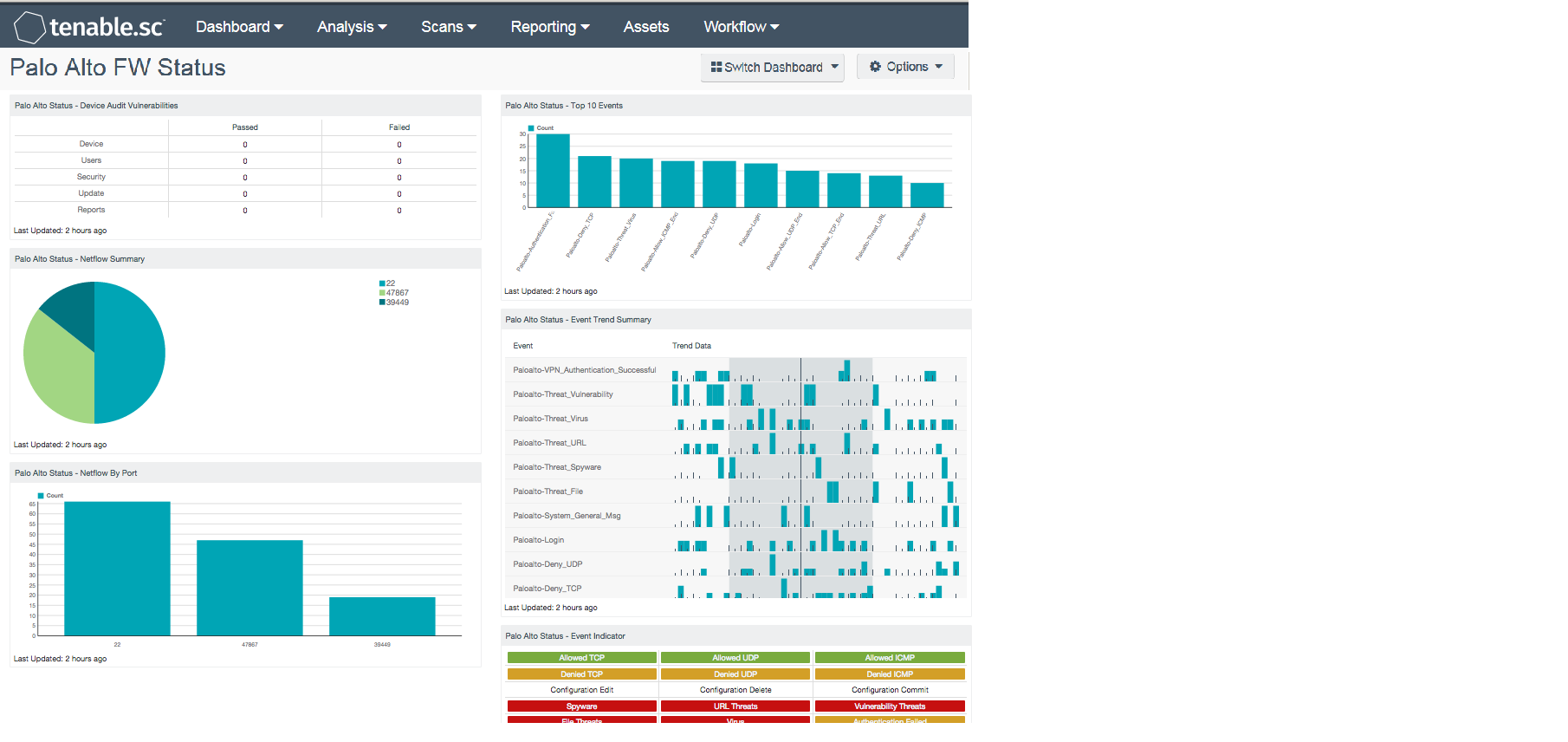
- Palo Alto Status - NetFlow By Port - This component displays the session count of the top 10 TCP ports identified by Palo Alto native network collector.
- Palo Alto Status - Top 10 Events - This component displays count of the top 10 Palo Alto syslog events.
- Palo Alto Status - Event Trend Summary - This component displays trend line for the top 10 Palo Alto syslog events.
- Palo Alto Status - Event Indicator - This indicator component displays series on Palo Alto syslog event indicators.
- Palo Alto Status - NetFlow Summary - This component displays a summary of the top 10 TCP ports identified by Palo Alto native network collector.
- Palo Alto Status - Device Audit Vulnerabilities - This component displays a pass/fail indicator by check type. The Tenable_Palo_Alto_PAN-OS_Best_Practices.audit file has 5 check types, each focusing on a separate part of the configuration audit.