by Stephanie Dunn
April 27, 2016
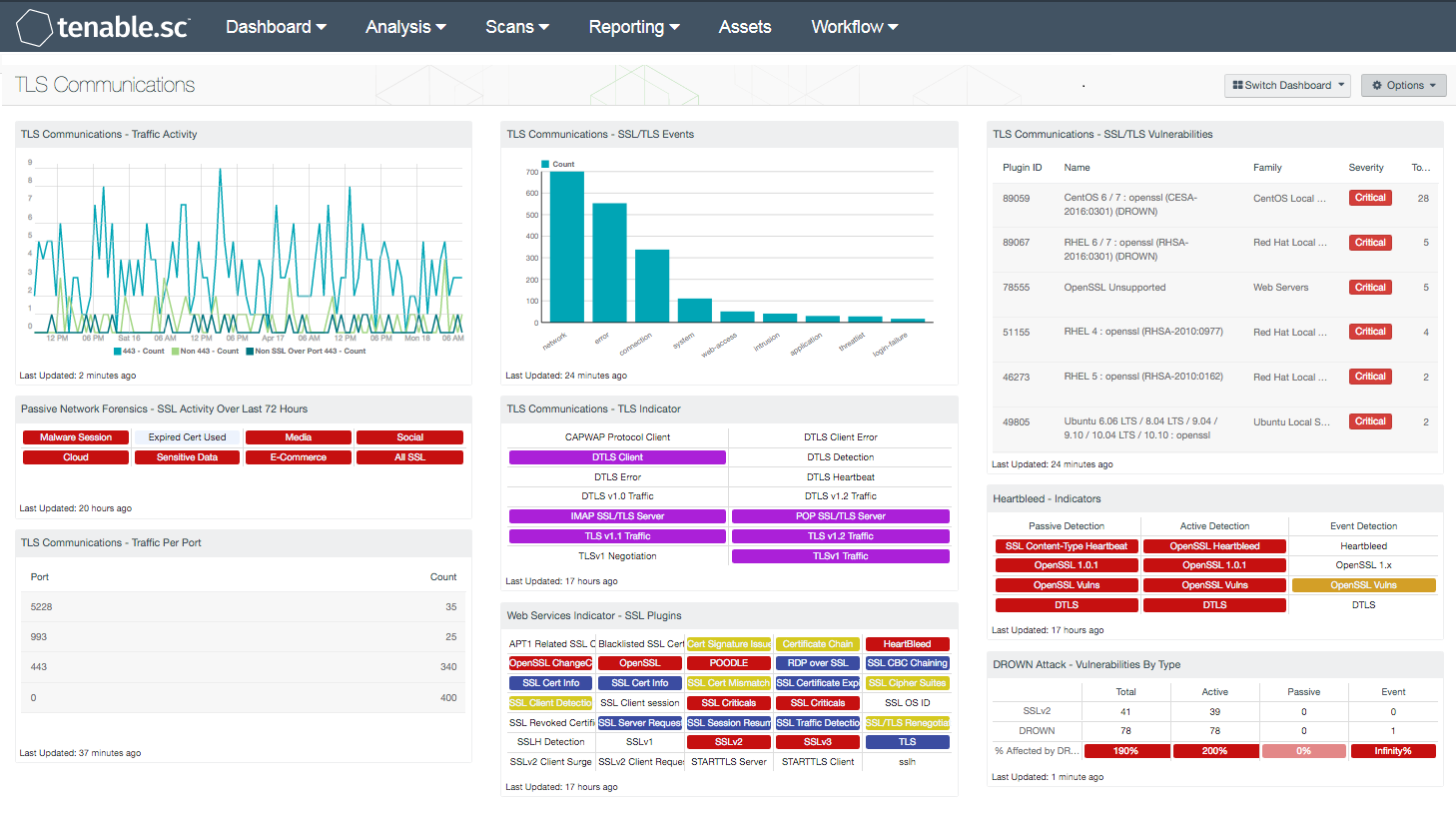
Digital certificates play an integral part in securing end user communications and website transactions. Unfortunately, some of web applications and enterprise software are often left misconfigured, or employ weak SSL certificates that could allow attackers to hijack sessions and obtain confidential information from end users. The TLS Communications dashboard provides organizations with the latest information on SSL/TLS event sessions, vulnerabilities, and network traffic.
The Transport Layer Security (TLS) protocol is the current standard that replaced the Secure Sockets Layer (SSL) protocol for secure communications over the Internet. Both protocols are in use within a wide variety of applications and services such as web browsing (HTTPS) and email (SMTP). In addition, both protocols provide secure application support for VPN connections, instant messaging, and Voice over IP (VoIP). In order to minimize the threat of data leakage, organizations should obtain trusted certificates from a reliable Certification Authority (CA), and use TLSv1.2 where possible. Using TLSv1.2, organizations will be able to ensure data confidentially and integrity, while adhering to industry best practices.
The information presented within this dashboard can be useful in identifying vulnerabilities and strengthening SSL/TLS security within the enterprise. Most web applications and enterprise software utilize standard ports such as 443 or another application specific port for SSL traffic. Some organizations may be alerted to systems utilizing custom ports, which may indicate unauthorized services or websites running on the network. Organizations should review detected ports continuously to ensure that malware or any unauthorized activity is using secure ports for communication outside the network. The Log Correlation Engine (LCE) will report on SSL-based events from detected devices and services. Assets are scanned using Nessus and the Nessus Network Monitor (NNM), detecting systems that are vulnerable to DROWN, POODLE, Logjam, and Heartbleed attacks, which exploit weaknesses in older SSL versions such as SSL 2.0, SSL 3.0, and TLS 1.0. Organizations can suffer major attacks if websites or applications are utilizing outdated versions of SSL or TLS. Continuous monitoring will provide complete visibility on existing vulnerabilities, and allow analysts to mitigate issues before critical systems are affected.
Several regulatory and compliance standards are addressing the need for organizations to adopt TLS 1.1 or higher. The National Institute of Standards and Technology (NIST) released NIST SP 800-52 Rev. 1, which prohibits the use of TLS 1.0, SSL 2.0, and SSL 3.0. In addition, the publication also recommended that federal agencies implement a minimum of TLS 1.1 or higher in order to adequately protect sensitive data. In April 2015, The Payment Card Industry Security Standards Council published the Payment Card Industry Data Security Standard (PCI DSS) Version 3.1, which addresses the end of SSL usage. Tenable Security Strategist and Evangelist, Jeff Man, posted a blog highlighting the new PCI DSSv3.1 changes, and how Tenable.sc Continuous View (CV) can help to identify existing SSL deployments and vulnerabilities.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection. The report requirements are:
- Tenable.sc 5.3.1
- Nessus 8.6.0
- LCE 6.0.0
- NNM 5.9.0
Tenable.sc CV provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. NNM provides deep packet inspection to continuously discover vulnerabilities traveling the wire. LCE correlates real-time events, and has the capability to discover users, operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and other critical infrastructure. By integrating with Nessus, NNM, and LCE, Tenable.sc CV’s continuous network monitoring is able to detect events and vulnerabilities across the enterprise.
The following components are included in this dashboard:
- TLS Communications – Traffic Activity: The Traffic Activity line chart presents a trend of SSL session events over secure ports within the last 72 hours. The chart is comprised of port 443, non-443, and non-SSL traffic over 443. The first two trend line events are dependent on a NNM plugin that detects SSL/TLS traffic based on unique byte patterns. Non-443 traffic events can indicate web applications or enterprise software utilizing application specific ports. Non-SSL traffic over 443 events may indicate unauthorized services or malicious activity on the network. Information presented within this chart triggers on SSL session events, such as web conferencing, social networking, e-commerce, cloud services, and more. Additionally, this chart can also alert analysts to malware activity and potential data leakage on the network. This chart can be modified to include additional information per organizational requirements.
- Passive Network Forensics – SSL Activity Over Last 72 Hours: This matrix presents indicators of SSL events that have occurred in the last 72 hours, including use of SSL certificates known to be associated with malware, use of expired SSL certificates, media access (such as Netflix or Skype), social media access (such as Facebook or Twitter), cloud file storage access, access to services commonly used for sensitive data, and access to services used for processing credit card transactions. The last indicator notes all passively detected SSL activity; this includes the above, plus other activity that might be of interest. Note that this component relies on NNM detections being forwarded to the LCE. Make sure that the NNM is configured to send syslog messages to the LCE: in Configuration > NNM Settings > Syslog, include the LCE host (with port 514) in the Realtime Syslog Server List. The LCE listens for syslog messages by default.
- TLS Communications – Traffic Per Port: The Traffic Per Port table displays a port summary of SSL/TLS-based traffic on the network. Most web applications and enterprise software utilize standard ports such as 443 or another application specific port for SSL traffic. Events are dependent on a NNM plugin that detects SSL/TLS traffic based on unique byte patterns. Organizations can use this information to identify web applications utilizing custom or application specific ports. This information may also alert organizations to possible unauthorized services or web applications running on the network. Organizations should review detected ports continuously to ensure that malware or any unauthorized activity is using secure ports for communication outside the network. Event data can be filtered to include specific or additional SSL session events.
- TLS Communications – SSL/TLS Events: This chart presents a trend of SSL/TLS events that have been detected over the last 72 hours. The component presents the top 10 SSL-based events, and sorted by event type. Organizations can obtain the latest SSL-based event activity being reported by various devices and services across the network. Analysts can modify the event data to include specific or additional normalized events.
- TLS Communications – TLS Indicator: This indicators provides information on the different types of vulnerability (informational to critical) associated with TLS v1 (Traffic, Negotiation), TLS v1.1 (Traffic, Negotiation), TLS v1.2 (Traffic, Negotiation), DTLS v1 (Traffic), DTLS v1.2 (Traffic), DTLS (Detection, Heartbeat, Client, Client Error, and Error), and CAPWAP Protocol Client. By using this indicator an IT security team can determine what type of secure communication are being used within the network, what risk are associated with these secure communication protocols, and what action can be implemented to reduce these security risk. If the vulnerability is detected, the indicator will change color to purple.
- Web Services Indicator – SSL Plugins: All the plugins that refer to SSL or certificates have been grouped into these indicators. An indicator will not be highlighted if no matches are found; however, if a match is found, the color will change. If all the plugins applied to the indicator have a severity of info or low, then the indicator will turn blue. If any of the selected plugins are medium, high, or critical, the color of the indicator will change to yellow, orange, or red accordingly. However, if there is a mix of info, low, medium, and high, the indicator will be purple. Indicators with a critical severity plugin will always be red.
- TLS Communications – SSL/TLS Vulnerabilities: The SSL/TLS Vulnerabilities component displays a list of SSL and TLS-based vulnerabilities on the network. The table is filtered by SSL and TLS-based plugin names, and is sorted by severity. Both Nessus and NNM will scan systems that are vulnerable to DROWN, POODLE, Logjam, and Heartbleed attacks that exploit weaknesses in older SSL versions. This will allow for both analysts and security teams to identify web applications and enterprise software with SSL/TLS vulnerabilities, expired certificates, self-signed certificates, and more.
- Heartbleed - Indicators: This component provides a series of indicators of systems that may be at risk to the HeartBleed vulnerability. The matrix is organized by column to provide indication of the identification method. Each row then displays indicators of vulnerabilities discovered. The first row will turn red for systems that have been identified to have the HeartBleed vulnerability. The second row reports on the OpenSSL version 1.0.1 vulnerabilities, and will turn red if a system is discovered. The third row provides a listing for all OpenSSl vulnerabilities, while the fourth row provides the DTLS vulnerabilities. The indicators for the OpenSSL and DTLS will turn red for the active and passive detection, and will turn orange for the event detections. With event detections, the severity can not always be discovered, therefore many of the logs have a severity level of info. Thus, the indicators will be orange to indicate a warning and manual review and verification is required.
- DROWN Attack - Vulnerabilities By Type: The Vulnerabilities by Type matrix displays the counts of SSLv2 and DROWN vulnerabilities detected by plugin type. Each column displays the count of vulnerabilities for a different plugin type. The first row filters for vulnerabilities related to SSLv2, and the second filters for DROWN vulnerabilities by CVE. The last row provides a ratio bar showing the percentage of SSLv2 vulnerabilities that have been confirmed to be vulnerable to a DROWN attack. Security teams can use this component to monitor the presence of SSLv2 and DROWN vulnerabilities in their environment.