by David Schwalenberg
May 18, 2016
The Verizon Data Breach Investigation Report (DBIR), first published in 2008, is an annual publication that analyzes information security incidents from public and private organizations, with a focus on data breaches. Data breaches continue to have a major financial impact on organizations, as well as an impact on their reputations. Tenable Network Security offers dashboards that can assist organizations in meeting many of the recommendations and best practices in the DBIR.
The 2015 DBIR notes that as in previous years, a vast majority of all attacks fall into a few basic patterns. Looking back to the 2014 DBIR for each of these patterns, best practices are noted that can assist in thwarting the attacks. Some of the best practices can assist in thwarting multiple attack patterns. The Point-of-Sale Intrusions, Web App Attacks, and Insider Misuse patterns all mention aspects of the general best practice of eliminating account weaknesses and vulnerabilities.
This dashboard presents vulnerabilities related to accounts and credentials. These vulnerabilities include default accounts, blank passwords, vulnerabilities that allow bypassing authentication, insecure and non-compliant account and password settings, and more. Potentially suspicious login activity is also noted to bring attention to accounts that are more threatened and require greater protection. This information can help an organization reduce its chance of a data breach by eliminating weak passwords, default accounts, and lax policies.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.1
- NNM 5.9.0
- LCE 6.0.0
- Compliance data
Tenable.sc Continuous View (Tenable.sc CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with the Nessus Network Monitor (NNM), as well as log correlation with the Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best protect its network from data breaches.
Listed below are the included components:
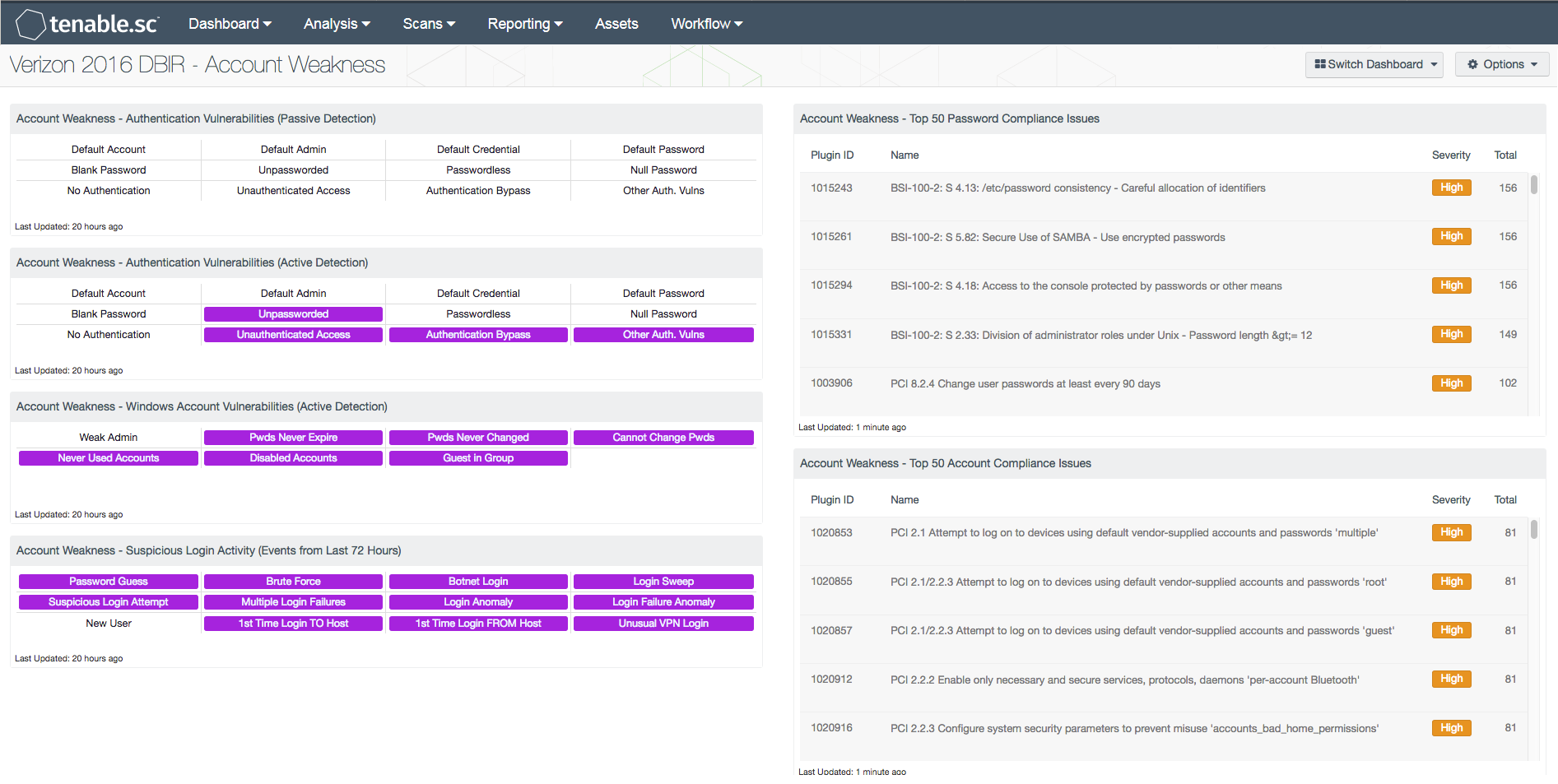
- Account Weakness – Authentication Vulnerabilities (Passive Detection) - This matrix shows passive detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name.
- Account Weakness – Authentication Vulnerabilities (Active Detection) - This matrix shows active detections of authentication vulnerabilities. Each indicator highlights those vulnerabilities with the given keyword(s) in their name.
- Account Weakness – Windows Account Vulnerabilities (Active Detection) - This matrix shows active detections of Windows account vulnerabilities.
- Account Weakness – Suspicious Login Activity (Events from Last 72 Hours) - This matrix shows potentially suspicious login activity. This activity can bring attention to accounts that are more threatened and require greater protection.
- Account Weakness – Top 50 Password Compliance Issues - This table displays the top 50 compliance issues with “password” in their name. Note that in order for data to appear in this table, appropriate audit/compliance scans must first be run on the network.
- Account Weakness – Top 50 Account Compliance Issues - This table displays the top 50 compliance issues with “account” in their name. Note that in order for data to appear in this table, appropriate audit/compliance scans must first be run on the network.