by David Schwalenberg
January 25, 2016
Collecting and analyzing Windows events is an important step in detecting unexpected or malicious activity on Windows systems. Windows events will log application and service installations and failures, and user account activity. Events will also be generated by Windows Firewall, Windows Defender, AppLocker, EMET, Windows Update, Windows Plug and Play (PnP), and other security applications and utilities. Events from these various sources can assist an organization in maintaining awareness of the behavior and health of their Windows systems, but the vast number of events does not make it easy for administrators and analysts to identify important events.
The National Security Agency developed the “Spotting the Adversary with Windows Event Log Monitoring” guide to define a recommended set of Windows events to collect and review on a frequent basis. Examples of these recommended events include Windows Firewall rule changes, Windows Defender taking action to protect the system, AppLocker blocking an application, Windows Update failures, and more. This dashboard is based on those recommendations.
Windows events can be forwarded to the Log Correlation Engine (LCE) via syslog or the LCE Client. LCE can then serve as a central location for log storage, which is recommended for event log integrity and backup. LCE is also capable of normalization and correlation of Windows events, collection of event summaries, and event statistical analysis. These details can further assist analysts in monitoring Windows systems.
This dashboard assists in monitoring the recommended Windows events from the NSA guide, which will aid organizations in maintaining awareness of the behavior and health of their Windows systems. Suspicious or unexpected behavior can be identified, monitored, and investigated. These events may indicate systems with problems, or potential malicious activity that needs to be addressed.
This dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring. The dashboard requirements are:
- SecurityCenter 4.8.2
- LCE 4.6.1
Tenable's SecurityCenter Continuous View (CV) is the market-defining continuous network monitoring solution. SecurityCenter CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable’s Passive Vulnerability Scanner (PVS), as well as log correlation with Tenable’s Log Correlation Engine (LCE). Using SecurityCenter CV, an organization will obtain the most comprehensive and integrated view of activity on its network.
This dashboard contains the following components:
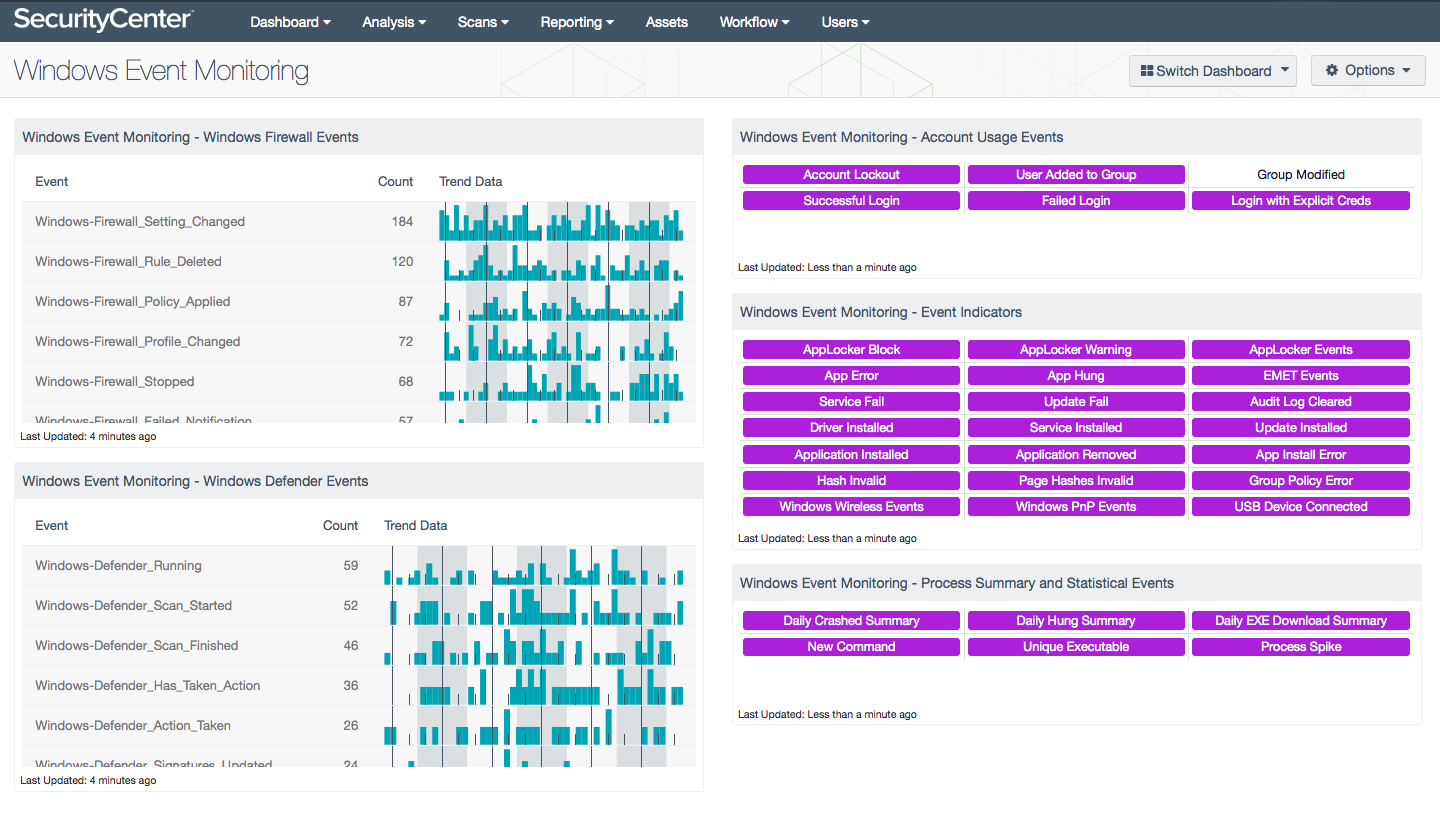
- Windows Event Monitoring - Windows Firewall Events - This table presents all Windows Firewall events collected in the last 72 hours. The table is sorted so that the most common events are at the top. For each event name, a count of events and a trend line that shows when the events occurred is given. Unexpected firewall state changes (started or stopped) and rule additions, deletions, and changes should be investigated, as these may indicate potentially unauthorized activity.
- Windows Event Monitoring - Windows Defender Events - This table presents all Windows Defender events collected in the last 72 hours. Windows Defender is an antispyware and antivirus application developed by Microsoft. The table is sorted so that the most common events are at the top. For each event name, a count of events and a trend line that shows when the events occurred is given. Any notifications of Windows Defender taking action to protect the machine should be investigated. Any events that indicate that Windows Defender is not operating as expected should also be investigated. If a third-party anti-malware product is in use, that product should be monitored instead.
- Windows Event Monitoring - Account Usage Events - This matrix presents indicators of Windows account usage in the last 72 hours. Account lockouts may indicate brute force attacks. Users being added to groups and groups being modified should be watched closely, as unauthorized membership in privileged groups is a strong indicator of malicious activity. Successful and failed logins can be further investigated for Pass the Hash activity and other unauthorized account usage. Clicking on a highlighted indicator will bring up the event analysis screen to display details on the events and allow further investigation.
- Windows Event Monitoring - Event Indicators - This matrix presents indicators of various Windows events collected in the last 72 hours that can be critical to identify behavior and health of systems. This includes events from AppLocker, an application whitelisting feature included in Windows, and EMET, the Enhanced Mitigation Experience Toolkit, a utility that helps prevent vulnerabilities in software from being successfully exploited. Also included are application error and installation events, driver and service installation events, service failures, Windows Update status events, audit log clear events, invalid hash events, and Group Policy errors. Windows wireless, Windows Plug and Play (PnP), and USB device connection events are also included. These events should be investigated for unexpected behavior that may indicate systems with problems or that are exhibiting suspicious behavior. Clicking on a highlighted indicator will bring up the event analysis screen to display details on the events and allow further investigation.
- Windows Event Monitoring - Process Summary and Statistical Events - This matrix presents indicators of various Windows process summary and statistical events generated by the Log Correlation Engine (LCE) in the last 72 hours. These events focus on the processes running on Windows systems, and can assist in maintaining awareness of the behavior and health of these systems. Daily summaries of crashed and hung processes can be investigated to find machines with problems or that are exhibiting suspicious behavior. The daily summary of EXE downloads can be investigated for any unauthorized executables. New commands (processes) that have never been previously observed and unique executables that have not been previously detected on any other systems may indicate new software or potential malicious activity. A statistical spike in process activity may indicate a new program, a new error, a user running a program in a new way, or malicious activity. Clicking on a highlighted indicator will bring up the event analysis screen to display details on the events and allow further investigation.