by Josef Weiss
August 19, 2015
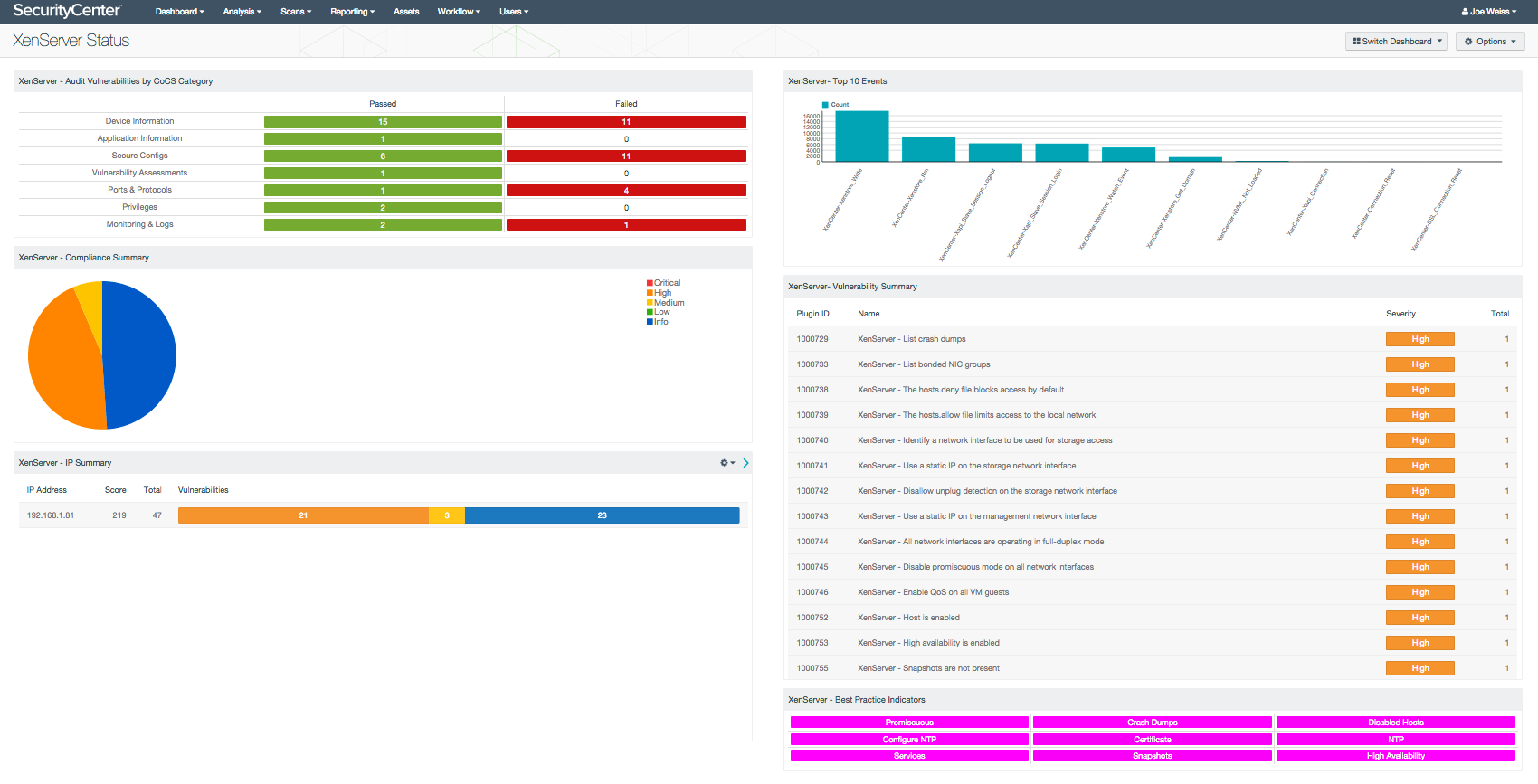
The XenServer dashboard displays the summary status of audited Citrix XenServers, and includes indicators, charts and tables for event, compliance results. Using the correlation features of LCE and Nessus compliance audit checks, the XenServer dashboard highlights the native ability of SecurityCenter to monitor the status and compliance statistics of XenServer devices. By collecting this information, a security analyst can review the configuration and compliance without requiring device management privileges.
Tenable’s Citrix XenServer Best Practices audit file is used to test XenServer hosts for vulnerabilities. Best practice tests within the audit are based on Common Criteria guidelines and include checks to inventory the contents and overall configuration of the XenServer host. The Common Criteria represent efforts to develop criteria for evaluating secure configurations, and is aligned with sources from the United States, Europe and Canada (TCSEC, ITSEC and CTCPEC respectively).
Utilizing best practices as a configuration guideline is a good operating practice and assists in establishing a starting point or benchmark for self-assessing systems and devices. Organizational policies and standards should always be consulted when establishing benchmarks.
While best practice violations may not always have serious implications, they may result in poor performance, reliability, and hidden or unexpected security risks. The XenServer dashboard and the associated components, assists the analyst in monitoring potential configuration concerns to increase XenServer’s effectiveness and reliability.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessment.
The dashboard requirements are:
- SecurityCenter 5.0.1
- Nessus 6.4.2
- LCE 4.4.1
- Compliance Data
SecurityCenter Continuous View (CV) is the market-defining continuous network monitoring platform. SecurityCenter CV includes active vulnerability detection with Nessus and passive vulnerability detection with the Passive Vulnerability Scanner (PVS), as well as log correlation with the Log Correlation Engine (LCE). Using SecurityCenter CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best protect its network from network compromise and data breaches.
The dashboard contains the following components:
- XenServer - Audit Vulnerabilities by CoCS Category - The Audit Vulnerabilities by CoCS Category component displays a pass/fail indicator by check type. The Citrix XenServer audit file has multiple checks focusing on configuration best practices. This matrix assists in establishing a starting point or benchmark for self-assessing systems and devices, focusing on several key categories. The vulnerability results have been filtered into 7 categories matching 7 of the 20 Council on Cyber Security (CoCS) 20 Critical Security Controls. The CoCS 20 Security Controls are a set of actions that provide specific and actionable methods to thwart attacks.
- XenServer - Compliance Summary - The Compliance Summary pie chart presents a graphical representation of compliance audit results. Compliance results are pass, fail, and further action required. This pie chart assists in quickly determining overall compliance standings from a pass/fail perspective. Three colors are associated with compliance results. Orange, which are high severity vulnerability results, are those compliance results which result in a failed audit result. Yellow are medium severity vulnerability results, which indicate additional action is required. Blue, or informational results, are those compliance results which indicate a pass.
- XenServer - IP Summary - The IP Summary table presents a more detailed compliance summary. The IP summary tool is used to distribute compliance results by IP address, providing details on specific device status. Compliance results are pass, fail, and further action required. This table assists in determining specifically which devices require the most attention. Three colors are associated with compliance results. Orange, which are high severity vulnerability results, are those compliance results which result in a failed audit result. Yellow are medium severity vulnerability results, which indicate additional action is required. Blue, or informational results, are those compliance results which indicate a pass.
- XenServer - Top 10 Events - The Top 10 Events bar chart displays normalized events from log data collected by Tenable’s Log Correlation Engine (LCE). Presented are the top 10 normalized events, sorted in descending fashion. This bar chart assists in determining which events, and at what level of occurrence, are being triggered specifically within the Xen environment. Large event counts may require additional investigation.
- XenServer - Vulnerability Summary - The Vulnerability Summary table component provides an overview of vulnerabilities found during the Nessus compliance audit. This table provides a more detailed understanding of the actual vulnerabilities by providing a readable text and severity level of existing vulnerabilities. The analyst may drill down into each vulnerability for detailed information. Displayed is the plugin ID, Name, Severity, and vulnerability count, sorted by severity, high to low. Compliance results that are listed as High are items that fail compliance checks.
- XenServer - Best Practices Indicator - The Best Practices Indicator uses results from the compliance audit to trigger indications for items that have failed best practice configuration guidelines. Best practice tests within the audit are based on Common Criteria guidelines and include checks to inventory the contents and overall configuration of the XenServer host. This matrix provides a quick indication of vulnerabilities that are present within the XenServer environment. Indications are present when the indicator is illuminated purple, and absent when the indicator is white. It is recommended that this be customized to meet existing organization standards and policies.