A Look at the Vulnerability-to-Exploit Supply Chain
Last week, Tenable Research released the report, How Lucrative Are Vulnerabilities? A Closer Look at the Economics of the Exploit Supply Chain, which takes a close look at the vulnerability-to-exploit supply chain and ecosystem.
The journey a software flaw takes – from being discovered and disclosed as a vulnerability to exploit development to ultimately being used in a cyberattack – includes many different travelers and stops. We chose to portray this journey in the form of a simplified vulnerability-to-exploit (V2E) supply chain model, which consists of only four main players:
- Producers: Discover vulnerabilities and then develop proof-of-concept exploit code.
- Suppliers: Facilitate the brokering and general availability of exploits and related knowledge to the market.
- Service providers: Integrate exploits into a variety of third-party products and services – from penetration testing frameworks to exploit kits.
- Consumers (e.g., end-user organization conducting a penetration test, criminal gang perpetrating fraud): Use the exploits.
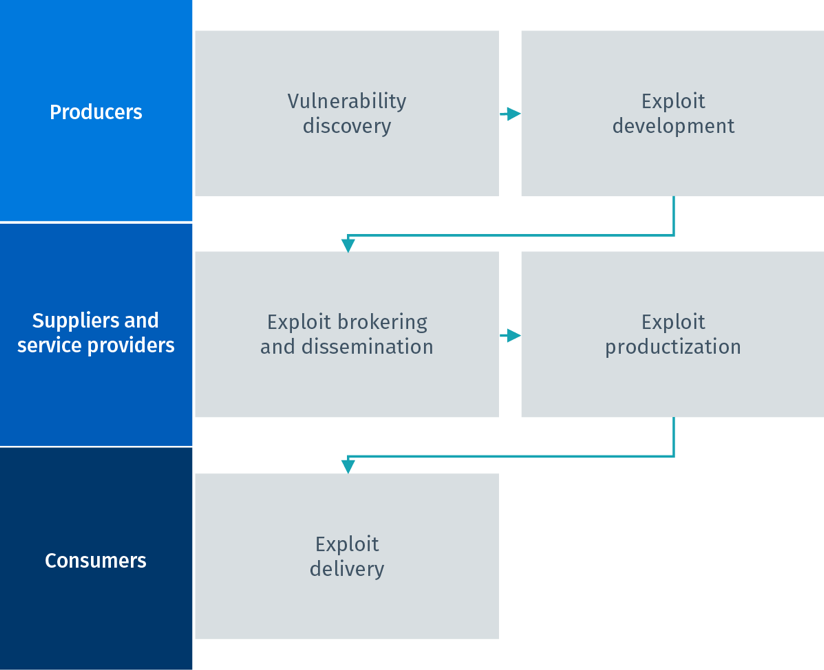
The V2E simplified supply chain
To learn more about the model and associated market actors, download the report. In this blog post, we’ll delve into one of the more interesting aspects of the V2E ecosystem.
Three markets of the vulnerability-to-exploit supply chain
While this supply chain model does a great job of breaking down the individual actors, it does hide a significant difference from most other markets. What makes the V2E supply chain so unique is it straddles three very different market segments: the white, gray and black markets.
- White market in vulnerabilities and exploits: Primarily composed of cybersecurity vendors and researchers focused on making intelligence widely available. It has driven the price of zero-day exploits into astronomic six-digit figures.
- Gray market: Composed of nation states and state-sponsored agencies/actors, motivated by national security concerns, that acquire and develop exploits for covert intelligence operations.
- Black (criminal) market: Exists mainly on the dark web. Black marketers sell capabilities required to weaponize and productize exploits in the form of cybercrime-as-a-service offerings (e.g., offensive operations such as ransomware).
Vulnerability-to-exploit supply chain: One ecosystem, conflicting goals
These markets are symbiotic and share a single ecosystem, but their objectives are diametrically opposed. The white market seeks to “defend and disclose” while the black market aims to “attack and obfuscate.” Gray market participants carefully balance national security and public security, relying on the latter, but will disclose for the greater good. By the time an exploit moves from vulnerability discovery to being used in an attack, it will have jumped across at least two and sometimes all three of these markets.
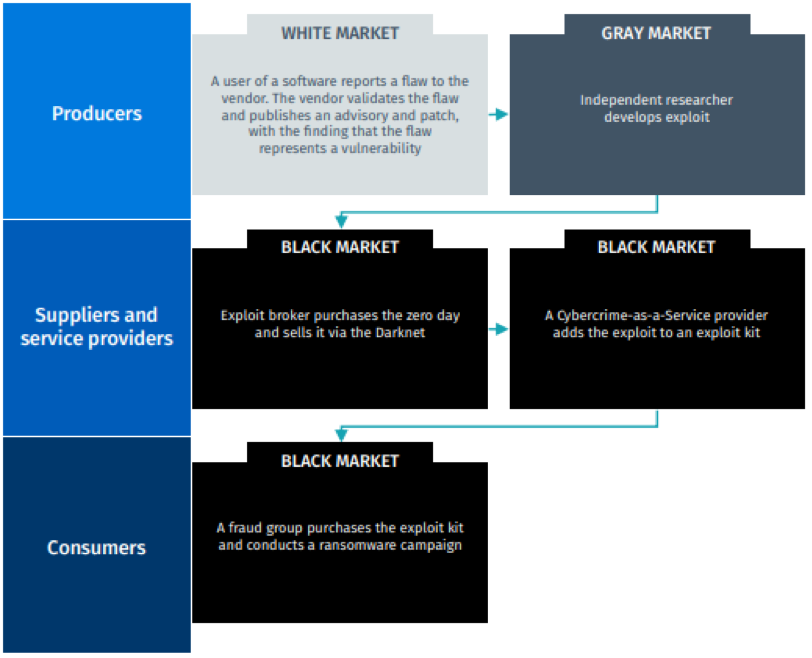
Supply Chain flow, showing the journey through the white, gray and black V2E markets
Vulnerability-to-exploit supply chain: Common start, differing or even parallel paths
Whichever of the three markets, the journey always begins with the discovery of a vulnerability, but then can take divergent and occasionally even parallel paths. The only difference is the white market uses the vulnerability and exploit intelligence to develop and deploy defensive capabilities, rather than pursue criminal objectives like the black market.
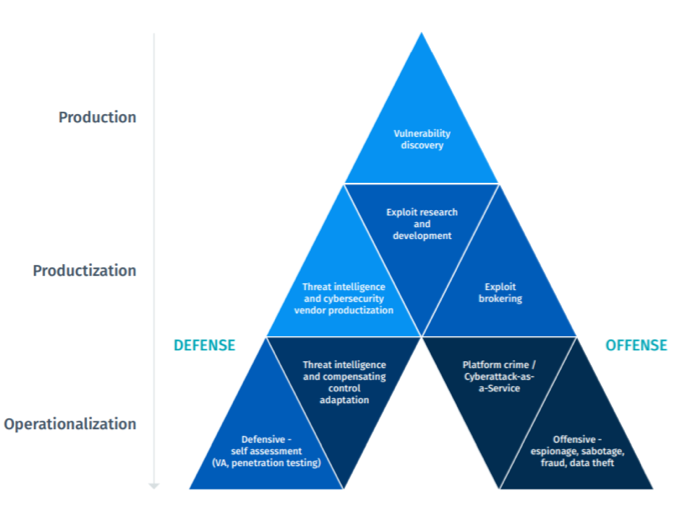
Mirrored legal and illegal V2E supply chain
Commercialization of the vulnerability-to-exploit supply chain
Both sides of the supply chain, whether defensive or offensive, diverge into commercial offerings. Research shows the black market has professionalized in recent years, with cybercrime-as-a-service offerings catering to a wide variety of criminal activities. Many of these are microservices bundled together to create purpose-designed attack architectures – from victim identification and profiling to persistence and attack obfuscation. Business-to-business services (e.g, money laundering, cryptocoin escrow services) complete an end-to-end ecosystem, making sophisticated offensive cyber capabilities available to anyone with sufficient will and capital.
While the barriers of entry to develop and weaponize exploits have risen due to this professionalization, the barriers of entry to conduct criminal and offensive cyberoperations in terms of required skill and tooling have been lowered. Criminals can buy together whatever capabilities they require and focus on committing the crime. This may well lead to growth in cybercrime, but it also represents an Achilles heel for smart defenders to target.
Less diversity in vulnerabilities being targeted in the wild
This increase in professionalism has come at the cost of diversity – less diversity in threat actors, especially less diversity in their deployed tools, tactics and procedures. That all equates to less diversity in vulnerabilities being targeted in the wild. Which for end users and the community – with the right intelligence – means more strategic remediation and less work.
Learn more about the V2E supply chain
Download How Lucrative Are Vulnerabilities? A Closer Look at the Economics of the Exploit Supply Chain- Research Reports
- Threat Intelligence

