Tenable versus CrowdStrike Falcon Exposure Management
Proactively secure your attack surface — not just your endpoints
Tenable has defined proactive security with best-in-class vulnerability management for more than two decades. And now, we are leading the way to exposure management. While CrowdStrike specializes in reactive incident response with endpoint detection and response (EDR), we enable security leaders to identify, prioritize and mitigate cyber risks effectively before attackers can exploit them.
Tenable 실제 작동 보기
Tenable이 어떻게 팀에서 비즈니스를 위험에 빠뜨릴 수 있는 사이버 위험을 식별하고 해결하도록 지원하는지 보시겠습니까?
사용자 지정 견적 또는 데모를 받으려면 이 양식을 작성하십시오.
Why customers choose Tenable over CrowdStrike
Compare Tenable Exposure Management
to CrowdStrike Falcon Exposure Management
Core focus
Unified exposure across IT, cloud, identity, and OT
Exposure from endpoint and identity telemetry
위험 노출 관리 분석
Combines integrated metrics across risk-based vulnerability management, web app scanning (WAS), cloud security, identity exposure, OT security, EASM and third-party data
Lacks comprehensive network scanning, web app security (WAS), identity data and holistic context beyond endpoints
자산 인벤토리
Unified asset graph across IT, cloud, OT, and identities
Based on discovered external and managed endpoint assets
Exposure Response
Exposure Response to track risk remediation with SLAs — instead of cumulative risk scores — and a single end-to-end workflow and a risk-based approach, regardless of patch availability
제공하지 않음
컴플라이언스
Covers a wide variety of compliance frameworks across various OSs
Limited support for CIS benchmarks
Peer benchmarking
Comparison of cyber risk to industry peers and to quickly identify shortcomings and strengths
제공하지 않음
Coverage scope
Coverage for a wide variety of asset types — endpoints, network devices, OT, cloud workloads, web apps
Primarily focused on endpoints with a Falcon agent and network devices visible to a Falcon agent
Scanning technology
Agent-based, agentless and network scanning
Agent-based and network scanning for devices visible to a Falcon agent
Tool consolidation potential
High—replaces scanners, CSPM, IAM risk tools, attack graphing, custom dashboards
Low—adds exposure context to Falcon but doesn’t replace core security tools
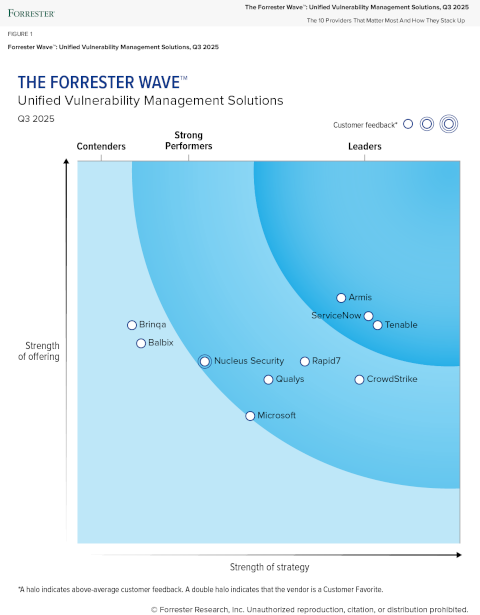
See why Tenable is a leader in vulnerability management
Tenable이 Forrester 보고서 "Forrester Wave™: Unified Vulnerability Management, Q3 2025"
Tenable continues to extend its established vulnerability assessment offerings into exposure management with its Tenable One platform
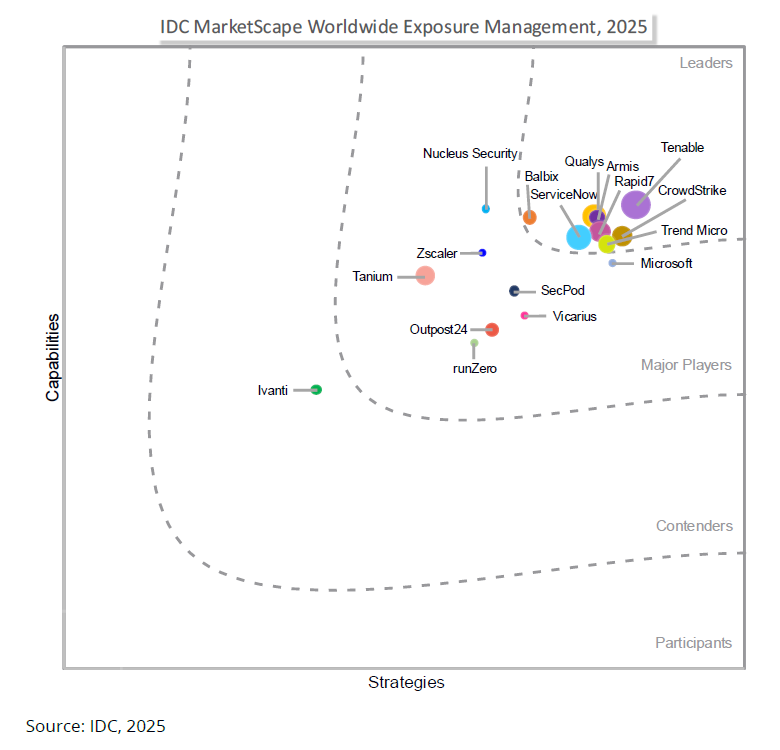
Tenable이 IDC MarketScape Worldwide Exposure Management 2025 Vendor Assessment에서 리더로 선정
"Organizations should consider Tenable One when seeking a unified exposure management platform that delivers broad asset coverage across IT, cloud, OT/IoT, identity, and application environments."
보고서 읽기Tenable One 시작하기
Tenable One은 엔지니어들이 수작업에 사용하는 시간의 75%를 줄여서 이들이 실질적 엔지니어링 작업에 집중할 수 있게 만들었습니다.