Cybersecurity Snapshot: CISOs See Budgets Tighten, as Cyberthreats Intensify

After double-digit growth in the past two years, cybersecurity budgets expanded more modestly in 2023. Plus, a survey offers an inside look at how organizations are grappling with cyber challenges. In addition, the U.S. and Japan warn about a China-linked group that’s stealthily compromising network devices. And much more!
Dive into six things that are top of mind for the week ending September 29.
1 - Cybersecurity budgets grow, but less than in years past
Cybersecurity teams on average saw an increase in their 2023 budgets, but the bump was much smaller than in previous years, as organizations across the board reined in IT spending.
That’s the main takeaway from the “2023 Security Budget Benchmark Report” released this week by IANS Research and Artico Search, which surveyed 550 CISOs and security executives. The report is now in its fourth year.
Specifically, cybersecurity budgets grew an average of 6%, much lower than the 17% growth in 2022 and, according to an IANS Research official, not high enough for CISOs to counter the increasingly sophisticated and aggressive cyberthreats their organizations face.
"The incremental growth in cybersecurity budgets is insufficient relative to the increases in scope facing security teams," Nick Kakolowski, Senior Research Director of IANS Research, said in a statement.
However, even with smaller budget increases, cybersecurity teams are doing better than other IT teams, as evidenced by the fact that the cybersecurity slice of the overall IT budget once again grew – reaching an average of 11.6%, up from 9.9% in 2022 and 8.6% in 2020.
Overall, 63% of organizations increased their cybersecurity budgets. Among those, the ones that got the largest bumps – an average increase of 27% over 2022 – attributed it primarily to highly publicized breaches.
And what’s the biggest item on cybersecurity budgets? That goes to staff and compensation, with a 38% share of the budget.
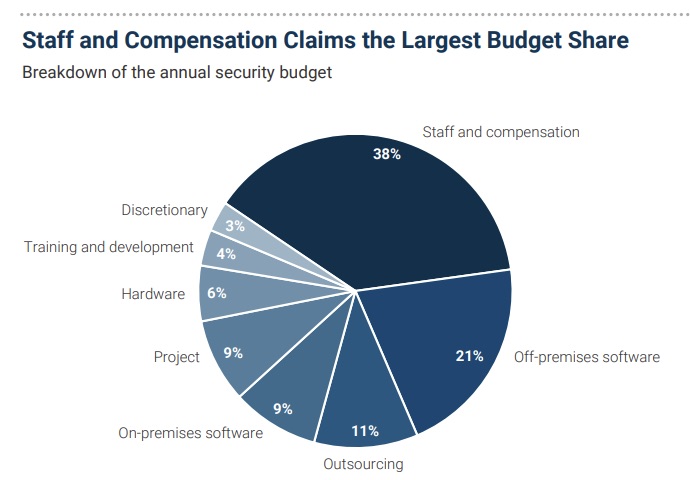
(Source: “2023 Security Budget Benchmark Report” from IANS Research and Artico Search, September 2023)
To get more details, check out the report’s announcement and a blog about the report, and download the full report.
For more information about cybersecurity budgeting:
- “Enterprise spending on cybersecurity has changed, and vendors must adapt” (TechCrunch)
- “How to best allocate IT and cybersecurity budgets in 2023” (TechTarget)
- “Where to Focus Your Company’s Limited Cybersecurity Budget” (Harvard Business Review)
- “How to Develop and Maximize an Effective Cybersecurity Budget” (InformationWeek)
- “Benchmarking your cybersecurity budget in 2023” (VentureBeat)
2 - Survey: Peek at peers’ cyber strategies, challenges
Wondering how other companies are dealing with cybersecurity issues like cyber insurance, third-party attacks, budget allocation, staffing and ransomware payments? Check out InformationWeek’s “Cyber Risk and Resiliency Report: How CIOs Are Dueling Disaster in 2023.”
Based on a survey of 180 IT executives and cybersecurity professionals, the report offers a fascinating view into how enterprises are tackling a wide variety of complex and often vexing questions about how to best manage cyber risk and attain IT resiliency.
Let’s take a look at a sampling of the report’s findings.
- Although mitigating cyber risk is a consensus high priority, 39% of organizations polled allocate less than 10% of their overall IT budget to cybersecurity.
- Cyberattacks ranked first among the causes for significant business disruptions, picked by 18% of respondents, followed by weather and natural disasters (15%); internal error or failure of internal systems (12%); and cyber incidents at a third-party provider (10%).
- However, little more than half of respondents (51%) said they suffered no significant threat or disruption during the previous 12 months.
- 46% carry cyber liability insurance, either a standalone policy or as part of a broader policy, and among these organizations, 84% feel cyber insurance cost is justified.
- Only 26% of organizations test their incident response procedures monthly or multiple times per month, while 12% have never tested them.
- Only 24% have a fully staffed cybersecurity team.
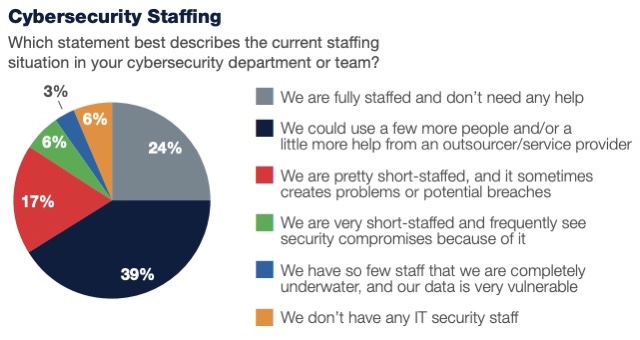
(Source: InformationWeek’s “Cyber Risk and Resiliency Report: How CIOs Are Dueling Disaster in 2023” report, August 2023)
To get more details, read the report’s announcement, download the report and check out an infographic.
3 - U.S. and Japan warn about China-linked BlackTech attackers
BlackTech, a group of hackers associated with the Chinese government, is stealing intellectual property and confidential data from U.S. and East Asia organizations by stealthily tampering with router firmware.
So said the U.S. and Japanese governments this week in the joint advisory “People’s Republic of China State-Sponsored Cyber Actors Exploit Network Providers and Devices,” in which they detail BlackTech tactics, techniques and procedures, and offer detection and mitigation recommendations.
“BlackTech activity targets a wide range of public organizations and private industries across the U.S. and East Asia. We encourage all organizations to review the advisory, take action to mitigate risk, report any evidence of anomalous activity, and continue to visit cisa.gov/china for ongoing updates,” Eric Goldstein, CISA’s Executive Assistant Director for Cybersecurity, said in a statement.
BlackTech attackers typically compromise routers and other network devices from subsidiaries by exploiting known vulnerabilities that the targeted organizations have left unpatched. Then they breach headquarters’ networks, where they use “living off the land” techniques to remain undetected.
Top network device CVEs exploited by PRC state-sponsored cyber actors
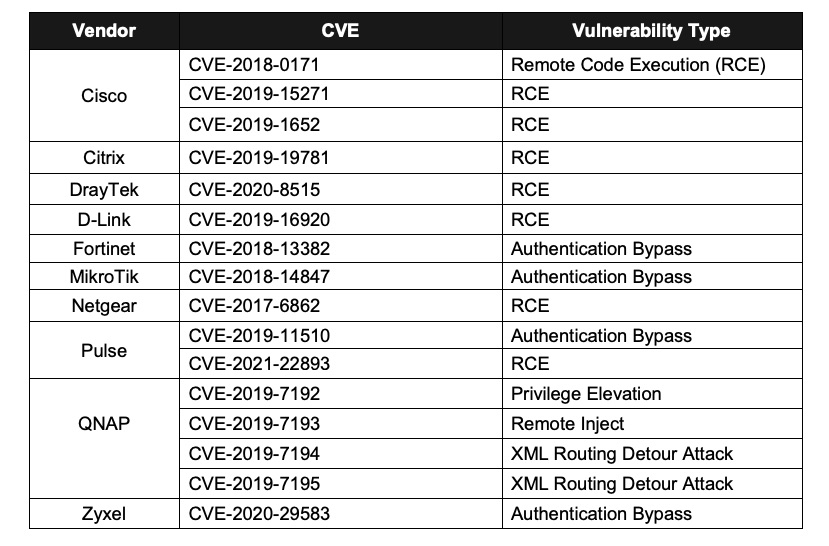
(Source: “People’s Republic of China State-Sponsored Cyber Actors Exploit Network Providers and Devices” advisory from the U.S. and Japan governments, September 2023)
The group targets Windows, Linux and FreeBSD operating systems using remote access tools (RATs) and custom malware, including BendyBear, FakeDead and FlagPro.
Recommendations include:
- Adopt a centralized patch management system to keep systems and products promptly updated
- Disable unnecessary ports and protocols
- Replace end-of-life infrastructure
- Immediately remove or isolate compromised devices from the network
- Segment networks to limit lateral movement
- Enforce multi-factor authentication for all users, and on all VPN connections
To get more details, read the joint alert, the joint announcement and the full advisory.
For more information about this advisory:
- “China APT Cracks Cisco Firmware in Attacks Against the US and Japan” (DarkReading)
- “US, Japan say ‘BlackTech’ Chinese gov’t hackers exploiting routers during attacks” (The Record)
- “Chinese Gov Hackers Caught Hiding in Cisco Router Firmware” (SecurityWeek)
- “US and Japan warn of Chinese hackers backdooring Cisco routers” (BleepingComputer)
4 - OpenSSF drafts software supply chain threat model, seeks input
The Open Source Security Foundation (OpenSSF) has produced an initial version of a threat model aimed for users of open source software (OSS) interested in preventing supply chain attacks.
The threat model is intended to help organizations assess and prioritize OSS supply-chain risks, as well as identify security weaknesses and gaps. It starts with “a very high-level depiction of a typical enterprise open source software consumer with common software assets,” wrote Jonathan Meadows, chair of the OpenSSF End Users Working Group, in a blog announcing the threat model.
“This model then details high-level threats against each component. Many of these threats should resonate as they have been actively attacked and reported in the media,” added Meadows, who is also a Citi Tech Fellow and the Head of Cloud, Application and Software Supply Chain Security at Citi.
Architecture diagram of a large in-house development organization
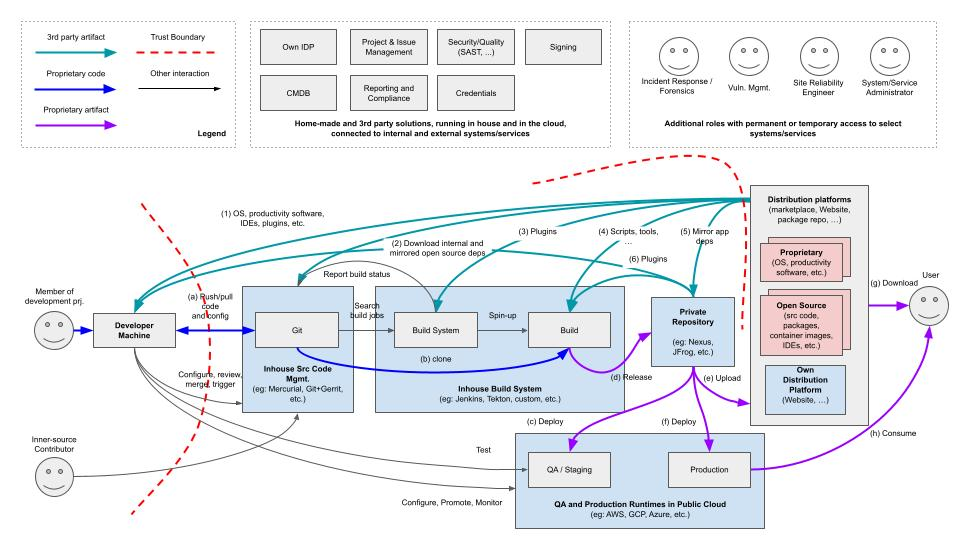
(Credit: OpenSSF)
Anyone interested in helping to further develop this threat model is invited to participate in the OpenSSF’s End Users Working Group, which gets together weekly at 9:30 am PT on Monday and bi-weekly on Thursday at 7:00 am PT. No threat modeling experience is required.
For more information about software supply chain security:
- “Securing the Software Supply Chain: Recommended Practices Guide for Customers” (CISA)
- “The new CIO security priority: Your software supply chain” (CIO)
- “Supply chain security guidance” (U.K. National Cyber Security Centre)
- “Software Supply Chain Best Practices” (Cloud Native Computing Foundation)
- “Are You Ready for the Next Log4Shell? Tenable’s CSO and CIO Offer Their Advice” (Tenable)
VIDEO
Top 5 Things to Know About Supply Chain Attacks (TechRepublic)
5 - CISA tackles hardware supply chain risk with new framework
While much attention has been placed on the risks of software supply chains, security teams shouldn’t overlook the dangers of insecure hardware components in their IT environments. If this is an area your organization would like to beef up, check out the "Hardware Bill of Materials Framework (HBOM) for Supply Chain Risk Management" document that CISA published this week.
The document aims to give buyers more clarity into hardware supply chains so they can better assess the safety and regulatory compliance of components they own or plan to buy. To that end, the framework offers the following:
- A consistent naming methodology for component attributes
- A format for identifying and documenting components’ different types
- Guidance for using HBOM information

The 33-page document has three main sections:
- Use cases for HBOMs
- HBOM formats
- Data taxonomy
“The framework’s objective is to set forth a reliable and predictable structure for HBOMs and a set of clearly defined data fields of HBOM components and their attributes, promoting efficiencies across the ICT (information and communications technology) sectors for a variety of use cases,” reads the document.
For more information about HBOMs and hardware security:
- “Hardware Bill of Materials: Essential in Electronics as Ingredients are to Food” (EE Times)
- “What is hardware security?” (TechTarget)
- “The urgency of cybersecurity for hardware devices” (Security InfoWatch)
- “Newly discovered side-channel attack side steps current defense mechanisms” (Carnegie Mellon University)
- “How hardware impacts cyber security” (CyberTalk)
VIDEO
CISA Releases Hardware Bill of Materials Framework (HBOM) for Supply Chain Risk Management (SCRM) (CISA)
6 - CISA updates reference architecture for identity security
Are you involved with securing identity systems? If so, you might be interested in perusing a newly updated CISA reference architecture.
The “Continuous Diagnostics and Mitigation Program: Identity, Credential, and Access Management (ICAM) Reference Architecture” explains how to integrate identity and access management (IAM) systems into ICAM architectures.
The intended audiences for the reference architecture are U.S. federal civilian departments and agencies, but the document probably has value for anyone tasked with protecting IAM systems, if only to learn how CISA is thinking about the matter.
The latest rev – version 1.3 – was released this month, featuring new information about zero trust. “Prior to this release, there was no singular, authoritative, and recognized reference for architecting an ICAM capability across an enterprise,” reads CISA’s announcement.
Topics include:
- Credential management
- Access management
- Federation
- Privileged user management
- Identity management
To get more details, read CISA’s announcement and the full 68-page document.
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Vulnerability Management


