사이버 보안 스냅샷: 딥페이크 위협, 오픈소스 위험, AI 시스템 보안 및 랜섬웨어 갱에 대한 최신 정보 받기

Tasked with securing your org’s new AI systems? Check out a new Google paper with tips and best practices. Plus, open source security experts huddled at a conference this week – find out what they talked about. Also, Uncle Sam says it’s time to prep for deepfake attacks. And much more!
Dive into six things that are top of mind for the week ending September 15.
1 - Google: The ins and outs of securing AI systems
As businesses adopt artificial intelligence (AI) and cybersecurity teams get tasked with protecting these complex new systems, a fundamental question looms: When defending AI systems, what changes and what stays the same?
That’s the topic of the paper “Securing AI: Similar or Different?” published by Google’s Cybersecurity Action Team. It aims to parse out what’s common and what’s unique about AI security in these seven areas:
- 거버넌스
- 위협
- Application and product security
- Data security and privacy
- Network and endpoint security
- Threat detection and response
- Security assessment and validation
“By understanding the differences between securing a traditional enterprise software system and an AI system, organizations can develop a more comprehensive security strategy to protect their AI systems from a variety of security threats,” the paper reads.
In a blog about the paper titled “The Prompt: What to think about when you’re thinking about securing AI,” the authors broadly summarize the key differences and similarities in this way:
- AI systems are more complex, more data driven, more adaptive and more interconnected than non-AI systems
- Many threats and vulnerabilities are the same in both AI and non-AI systems, and their processed data and software supply chain must be secured
The paper also includes best-practice recommendations for AI system security, including:
- Adopt strong governance and security controls throughout the AI lifecycle
- Implement strong controls for securing data collection, data storage, data processing and data usage
- Inventory and understand your AI systems, including how they work, what data they use and how employees and customers use them
- Use secure software development practices, such as code review, threat modeling and penetration testing
- Educate users, developers and operators of AI systems about security risks
- Monitor deployed AI systems by filtering and logging inputs, such as generative AI prompts, as well as outputs; and check them for security threats
- Have an incident response plan in place
To get more details:
- Read the paper “Securing AI: Similar or Different?”
- Check out the blog “The Prompt: What to think about when you’re thinking about securing AI”
- Listen to a Google podcast in which Google CISO Phil Venables talks about AI security
- Read the related paper “Why Red Teams Play a Central Role in Helping Organizations Secure AI Systems”
2 - CISA: Prep for deepfake threats now
Deepfakes represent such a danger to public- and private-sector organizations alike that they must be ready to identify and respond to these threats. That’s the word from the U.S. government, which this week published an 18-page guide titled “Contextualizing Deepfake Threats to Organizations," intended to help organizations defend themselves from deepfake attacks.
Deepfakes are highly-realistic multimedia created or manipulated using AI with the intention to misinform, trick and confuse people. Attackers use these maliciously crafted videos, photos and audio to create societal unrest, carry out fraud and damage reputations of individuals and brands.
“Organizations can take a variety of steps to identify, defend against, and respond to deepfake threats,” reads the document, published by the National Security Agency (NSA), the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA).

Those steps include:
- Implement technologies that detect deepfakes and determine media origins
- Proactively plan for and rehearse responses
- Train staff, especially on recognizing deepfakes in phishing attacks
- Use authentication techniques and watermarks to protect sensitive multimedia, such as ones containing high-profile individuals
To get more details, check out the joint announcement from the NSA, FBI and CISA and the full guide “Contextualizing Deepfake Threats to Organizations”.
For more information about deepfake attacks:
- “Does your boss sound a little funny? It might be an audio deepfake” (Protocol)
- “Reshaping the Threat Landscape: Deepfake Cyberattacks Are Here” (Dark Reading)
- “How to prevent deepfakes in the era of generative AI” (TechTarget)
- “Why deepfake phishing is a disaster waiting to happen” (VentureBeat)
- “Prepare for deepfake phishing attacks in the enterprise” (TechTarget)
VIDEOS
Stop deepfakes - How to counter presentation attacks (ENISA)
How synthetic media, or deepfakes, could soon change our world (60 Minutes)
3 - OpenSSF lays out plans for boosting OSS security
Develop more education materials for hands-on and in-depth learning about open source software (OSS) security. Create more security guides. Improve OSS supply-chain integrity. Enhance OSS infrastructure and tooling.
Those are some of the initiatives the Linux Foundation’s Open Source Security Foundation (OpenSSF) plans to undertake in the coming year, the group announced at its “Secure Open Source Software Summit 2023” held in Washington, D.C. this week.

The event featured representatives from the U.S. federal government, including CISA, the National Science Foundation and the National Security Council, as well as from the private sector, including Amazon, Apple and Google.
“By bringing together a diverse group of stakeholders, we aim to foster a culture of collaboration and innovation in addressing the most critical security challenges facing open source software for the public good,” OpenSSF General Manager Omkhar Arasaratnam said in a statement.
Topics discussed at the summit included:
- The need for better collaboration among incident response providers
- More coordinated vulnerability disclosures
- Improved threat information exchanges
- Better understanding of the ties between OSS, security and artificial intelligence (AI)
To get more details, check out the “Secure Open Source Software Vision Brief” the organization published at the event.
For more information about OSS security:
- “Managing open source components in the software supply chain (TechTarget)
- “Are You Ready for the Next Log4Shell? Tenable’s CSO and CIO Offer Their Advice” (Tenable)
- “Enhancing open source security: Insights from the OpenSSF on addressing key challenges” (Help Net Security)
- “Insecure open source components create supply chain risks” (Tenable)
- “Software Supply Chain Best Practices” (Cloud Native Computing Foundation)
4 - CISA outlines its roadmap for open source security
And continuing with the OpenSSF’s “Secure Open Source Software Summit 2023,” CISA announced its roadmap for OSS security at the event. Saying it’s focused on securing OSS in the U.S. federal government, as well as on helping make the OSS ecosystem safer for everyone, CISA said it expects to attain four key goals between fiscal years 2024 and 2026.
- Establish its role to support OSS security by, for example, partnering with OSS communities
- Broaden visibility into OSS usage and risks, by, among other things, developing a framework for OSS risk prioritization
- Lower risks to the federal government by, for example, developing OSS best-practices guidance for federal agencies
- Harden the OSS ecosystem by, for example, coordinating OSS vulnerability disclosures and responses
“We envision a world in which every critical OSS project is not only secure but sustainable and resilient, supported by a healthy, diverse, and vibrant community,” reads the eight-page “CISA Open Source Software Security Roadmap.”

Last month, CISA, the White House and other federal agencies issued a formal request for information (RFI) about OSS security, saying that the issue is critical since the usage of OSS software globally is widespread.
To get more details, check out CISA’s announcement of its OSS security roadmap and read the full roadmap document, as well as a blog about it from the OpenSSF.
5 - Tenable poll on tool sprawl, risk prioritization
During our recent webinar “Maximizing Your Cyber Resilience: Why Now is the Right Time to Transition from Vulnerability to Exposure Management,” we polled attendees about a number of related topics. Check out what they said about the size of their cyber toolset and about their ability to prioritize cyber risk across their attack surface.
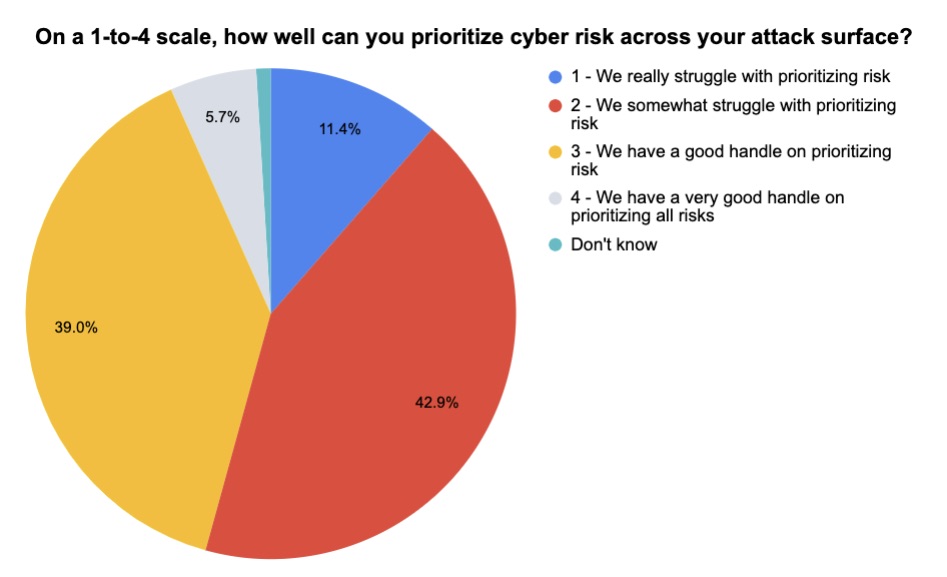
(105 respondents polled by Tenable, August 2023)
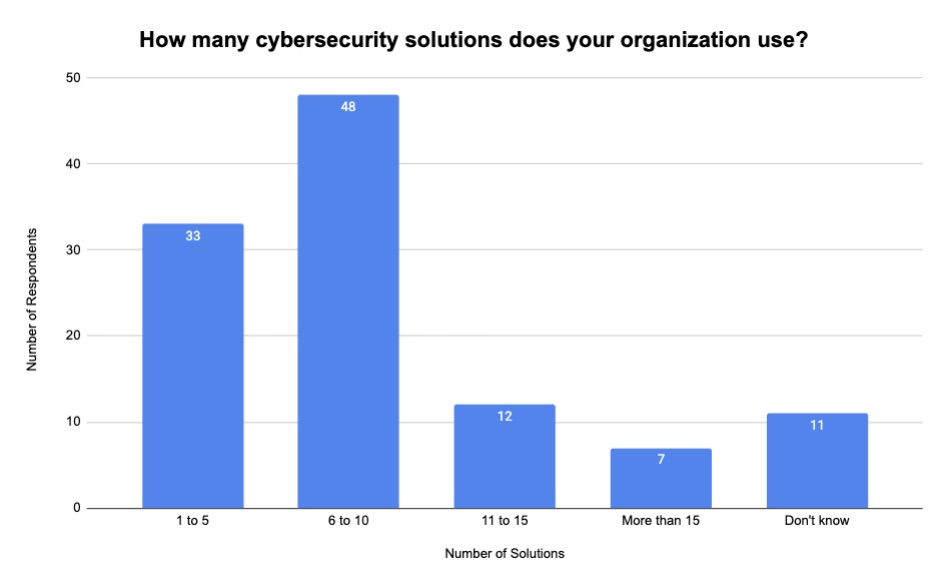
(111 respondents polled by Tenable, August 2023)
For more insights about exposure management and its benefits, check out these Tenable resources:
- “The 7 Benefits of a Unified Exposure Management Platform” (video)
- “Exposure Management: How To Get Ahead Of Cyber Risk” (resource page)
- “Exposure Management for the Modern Attack Surface” (on-demand webinar)
- “3 Real-World Challenges Facing Cybersecurity Organizations: How an Exposure Management Platform Can Help” (white paper)
- “Exposure Management: Reducing Risk in the Modern Attack Surface” (blog)
6 - U.K. cyber agency delves into ransomware’s criminal ecosystem
Noting that ransomware gangs and their partners continue to adapt, the U.K. National Cyber Security Centre this week published a white paper to update cyber teams on the evolution of the ransomware ecosystem.
Titled “Ransomware, extortion and the cyber crime ecosystem,” the 26-page paper shifts the focus away from granular analysis of individual ransomware strains and attacks and puts it on the broader, interconnected supply chain of services, platforms, distributors and affiliates that all play a part.
Simplified Ransomware Workflow
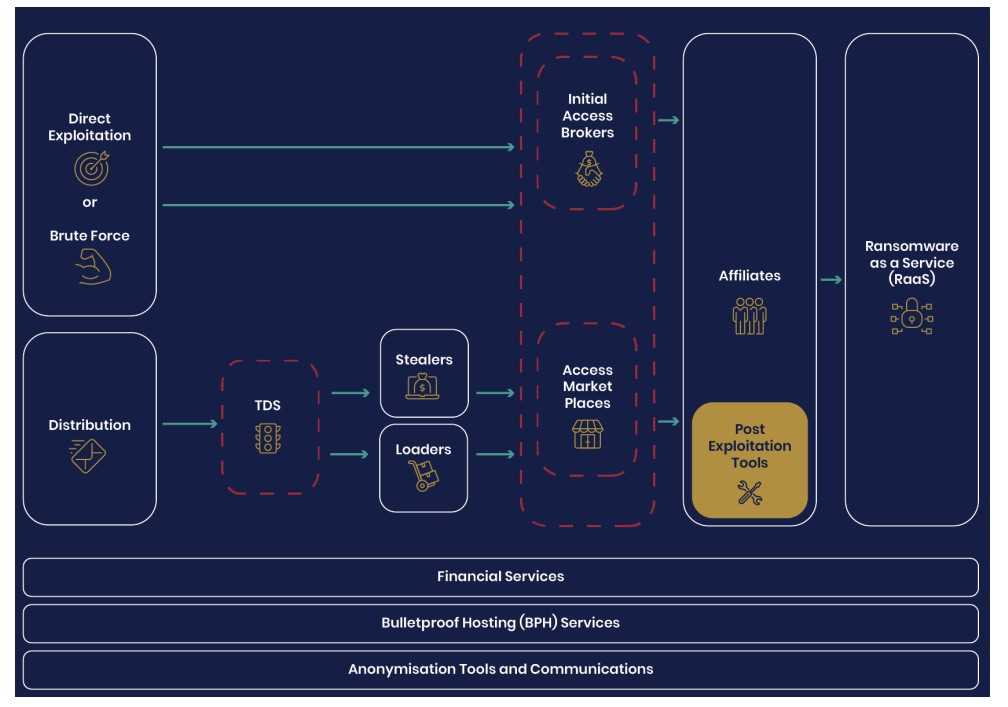
(Source: “Ransomware, extortion and the cyber crime ecosystem” paper from the U.K. NCSC, September 2023)
The U.K. government’s strategy to disrupt ransomware activities “is based on understanding and undermining the increasingly sophisticated criminal ecosystem behind these threats, especially focusing on common enablers and vulnerabilities,” wrote James Babbage, Director of General Threats at the U.K. National Crime Agency (NCA), which contributed to the paper.
Topics covered include:
- The cybercrime ecosystem
- Common initial access vectors, like stealers and loaders, direct exploitation and brute force access
- Initial access brokers
- Ransomware business models, such as ransomware as a service and ransomware affiliates
- Financial services
“The deployment of ransomware relies on a complex supply chain, so focussing on specific ransomware strains can be confusing at best, and unhelpful at worst. We hope that the publication of this white paper shines a light on the motivations of the threat actors further upstream,” reads the NCSC blog “Ransomware and the cyber crime ecosystem” about the paper.
For more information about ransomware:
- “Ransomware Protection: How to Prevent Ransomware Attacks” (eSecurity Planet)
- “The complete guide to ransomware” (TechTarget)
- “Stop Ransomware Guide” (CISA)
- “Ransomware Preparedness: Why Organizations Should Plan for Ransomware Attacks Like Disasters” (Tenable)
VIDEO
Anatomy of a Threat: MOVEIt (Tenable)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Vulnerability Management


