사이버 보안 스냅샷: Insights on Supply Chain Security, Hiring, Budgets, K8s, Ransomware

Get the latest on staffing challenges; nation-state assaults on critical infrastructure; supply chain security tips; ransomware weak links; Kubernetes security; and more!
Dive into 6 things that are top of mind for the week ending Nov. 11.
1 - Cybersecurity budgets rise, but hiring remains a challenge
Although cybersecurity teams got a budget bump and devote, by far, the largest budget slice to staff compensation, security leaders continue to struggle with recruitment and retention.
That’s one finding from the “2022 Security Budget Benchmark Report” by IANS Research and Artico Search, which is based on a survey of 502 CISOs in the U.S. and Canada.
Steve Martano, Artico Search co-founder, attributes this to “misaligned salary bands, outdated market data and the competitiveness of the market across all levels of security.”
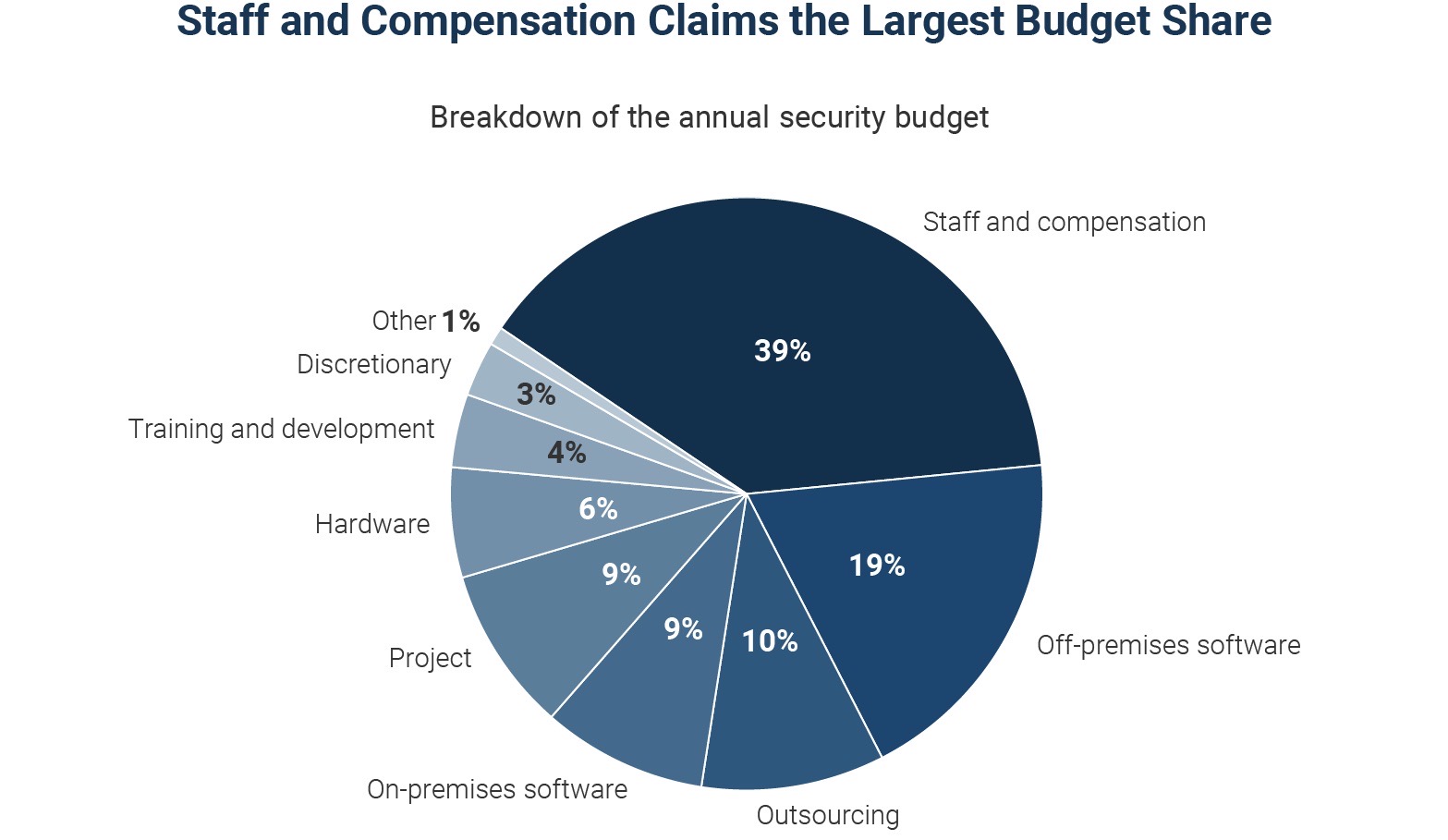
(Source: “Security Budget Benchmark Summary Report” from IANS Research and Artico Search, October 2022)
Specifically, cybersecurity budgets went up on average 17%; the vast majority of respondents (80%) reported an increase and only 3% reported a decline.
Here’s what’s pushing cybersecurity budgets higher:
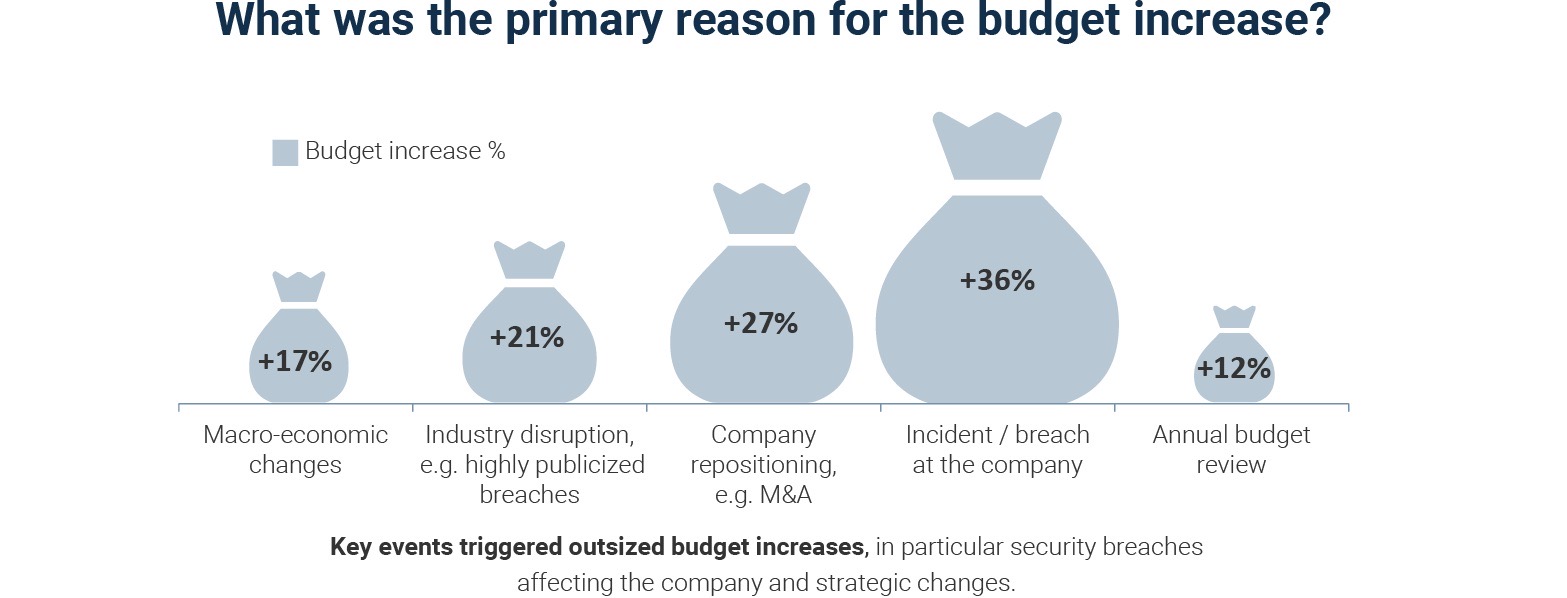
(Source: “Security Budget Benchmark Summary Report” from IANS Research and Artico Search, October 2022)
For more information about cybersecurity budgets, read:
- “5 key considerations for your 2023 cybersecurity budget planning” (CSO Online)
- “Cybersecurity budget breakdown and best practices” (TechTarget)
- “How 2023 cybersecurity budget allocations are shaping up” (CSO Online)
- “Cybersecurity Tops the CIO Agenda as Threats Continue to Escalate” (Wall Street Journal)
You can also watch this video:
2 – A quick check on Kubernetes security
As they expand their container use, many organizations adopt Kubernetes, an open-source system for orchestrating the management of containerized applications. But how do you ensure your Kubernetes environment is secure?
That was the topic of a recent Tenable webinar, and we took the opportunity to poll attendees on their Kubernetes usage and on their familiarity with policy as code (PaC), which helps to programmatically ensure compliance with security policies in Kubernetes environments.
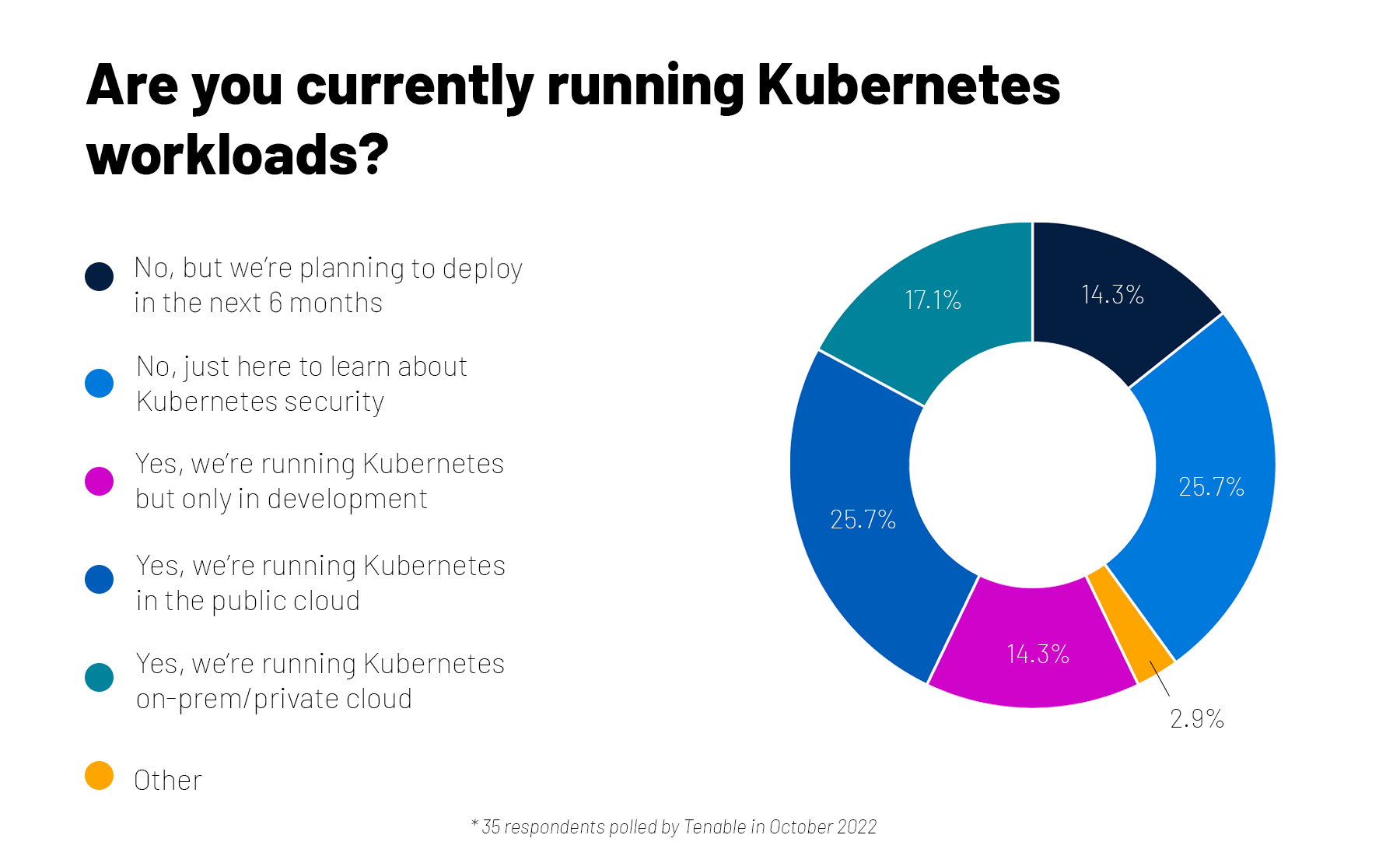
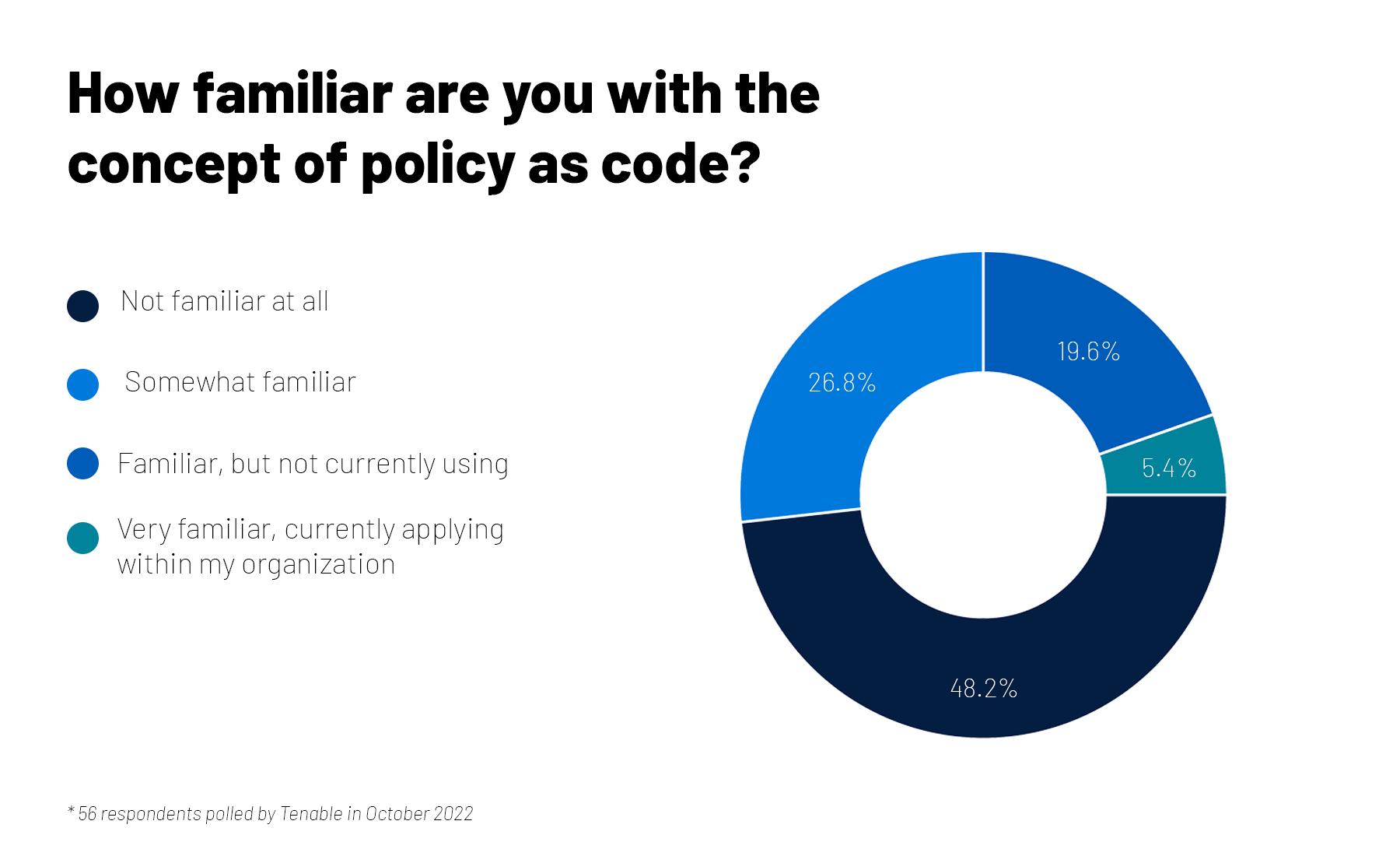
For more information about Kubernetes security and PaC, check out these Tenable resources:
- “The Four Pillars of Kubernetes Security” (webinar)
- “4 Steps To Achieving Comprehensive Kubernetes Security” (white paper)
- “Enterprise Guide To Policy As Code: Design, Build, And Runtime” (white paper)
- “How to Establish Cyber Resilience with Policy as Code” (blog)
- “Introducing Tenable Cloud Security with Agentless Assessment and Live Results” (blog)
3 – Supply chain security guide issued for software suppliers
A new guide outlines recommendations for securing software vendors’ supply chains and preventing SolarWinds-like attacks, in which hackers compromise software development and software release environments to stealthily deliver malicious code to customers.

Issued by the Office for the Director of National Intelligence, the National Security Agency and the Cybersecurity and Infrastructure Security Agency, the 45-page guide was preceded by one aimed at developers and will be followed by one for customers.
Actionable recommendations for vendors include:
- Prepare your organization by establishing policies for secure software delivery.
- Protect software by:
- Safeguarding all code from unauthorized access, and applying the concept of least privilege throughout the software development lifecycle
- Having a mechanism to vet the integrity of software releases by digitally signing code
- Archiving and protecting all software releases for use cases like disaster recovery and incident investigations
- Produce “well-secured” software by:
- Designing software that complies with security requirements
- Verifying third-party software meets security requirements
- Configuring the compilation and build processes
- Reviewing human-readable code and testing executable code for vulnerabilities and policy compliance
- Identify, analyze and remediate known vulnerabilities continuously
For more information about software supply-chain security, read:
- “What is supply chain security” (TechTarget)
- “3 post-SolarWinds supply chain security best practices” (TechTarget)
- “Best practices for boosting supply chain security” (ComputerWeekly)
- “When Securing Your Software Supply Chain, Don't Forget the Cloud” (ITPro Today)
You can also watch this video:
4 – Russia-Ukraine war reshapes EU’s cyberthreat landscape
The European Union Agency for Cybersecurity (ENISA) just published its annual report on the EU’s top cyberthreats, major trends, malicious players and attack techniques. It highlights Russia’s invasion of Ukraine and the ongoing war, saying it has altered the EU’s threat landscape through an increase in hacktivism, cybercrime, disinformation and military-focused cyberattacks.
(Source: “ENISA Threat Landscape 2022” report from the European Union Agency for Cybersecurity, October 2022)
Other major trends identified by the report, which covers the period between July 2021 and July 2022, include:
- An emphasis by cybercriminals on exploiting zero day vulnerabilities, as businesses do a better job of patching known bugs
- A strategy among ransomware groups to disband and rebrand themselves to dodge law enforcement agencies, while collectively stealing 10 terabytes of data monthly
- Increased traction for “hacker-as-a-service” providers
- An escalation of software supply chain attacks, which accounted for 17% of intrusions in 2021, up from 1% in 2020
- A boom in distributed denial of service (DDoS) attacks, which have gotten more complex and larger, and increasingly focus on mobile networks and IoT systems
- An increasing sophistication in phishing methods
- An evolution in extortion techniques
- Greater interest in stealing data
- Growing interest in adversarial machine learning attacks
- The use of artificial intelligence for spreading misinformation and creating “deepfakes”
Looking at specific sectors, the government and digital service providers were the most targeted, as this chart shows.
Targeted sectors per number of incidents
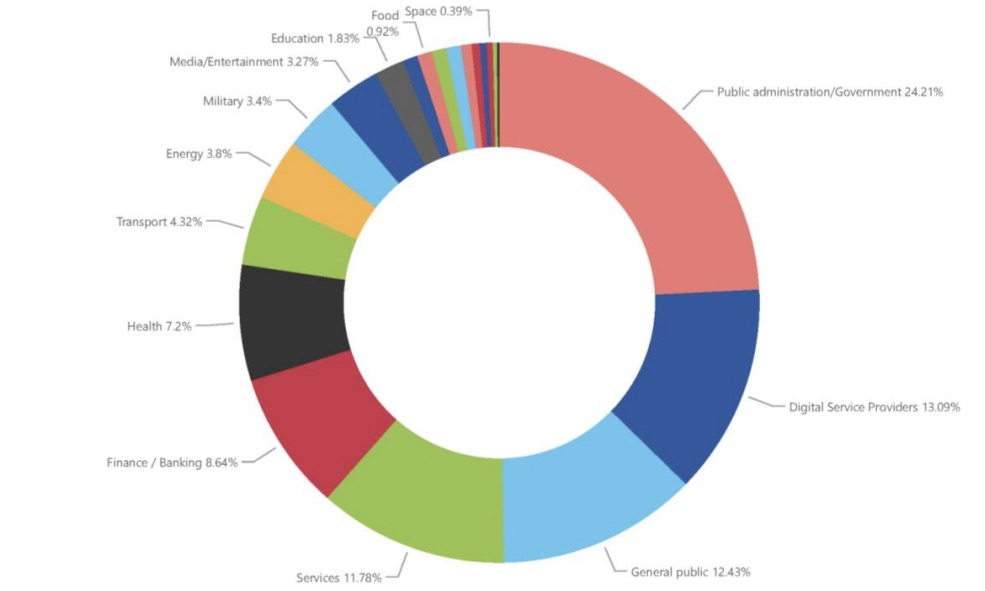
(Source: “ENISA Threat Landscape 2022” report from the European Union Agency for Cybersecurity, October 2022)
The 150-page report also offers prevention and mitigation recommendations, and maps them to the ISO/IEC 27001 framework and to the NIST Cybersecurity Framework.
For more information, view an ENISA infographic and read analysis and coverage from Infosecurity Magazine, CSO Online, Help Net Security and Reuters.
5 - Nation-state actors intensify critical infrastructure cyberattacks
Microsoft has released its “Digital Defense Report 2022,” which touches on multiple cybersecurity areas, including the state of cybercrime; nation-state threats; infrastructure and device security; and malicious cyber propaganda campaigns.
Here are some highlights from the 114-page report.
- Nation-state actors dialed up their cyber assaults against critical infrastructure targets, which now account for 40% of nation-state attacks, up from 20% last year. Microsoft highlights threats from China, Iran, North Korea and Russia – in particular the latter’s use of cyberweapons in its war against Ukraine.
- Ransomware attack victims generally have weak identity controls, security operations and data protection – with 88% lacking multi-factor authentication for privileged accounts; 68% having ineffective vulnerability and patch management; and 92% lacking effective data loss prevention controls.
- With the growth in internet-connected devices, there’s been an expansion of the attack surface, whose weak links currently include internet of things (IoT) devices and operational technology (OT) devices, both of which are being targeted using malware-as-a-service tools.
The report includes recommendations for improving cyber resiliency, including adopting basic cyber hygiene; proactively detecting threats and vulnerabilities; and using isolation and segmentation.
For more information, read a blog about the report, and check out coverage and analysis from TechTarget, SC Magazine, The Register and ZDnet.
6 - Small businesses boost cybersecurity spending, breaches drop
More U.S. small businesses increased spending this year in security tools and training, and are experiencing fewer cyber breaches – except in one category: social media account takeover.
The findings come from Identity Theft Resource Center’s (ITRC) “2022 Business Impact Report,” which surveyed 447 IT professionals and business leaders from companies with 500 or fewer employees.
Asked what steps they’ve taken to prevent breaches, 56% said they acquired new security tools, up from 47% in 2021. Meanwhile, 48% are offering new IT staff training, up from 44%. More than a quarter (29%) grew their security budgets, up from 27%.
Overall, small businesses are doing better, with 45% reporting a security and/or data breach, down from 58% in 2021.
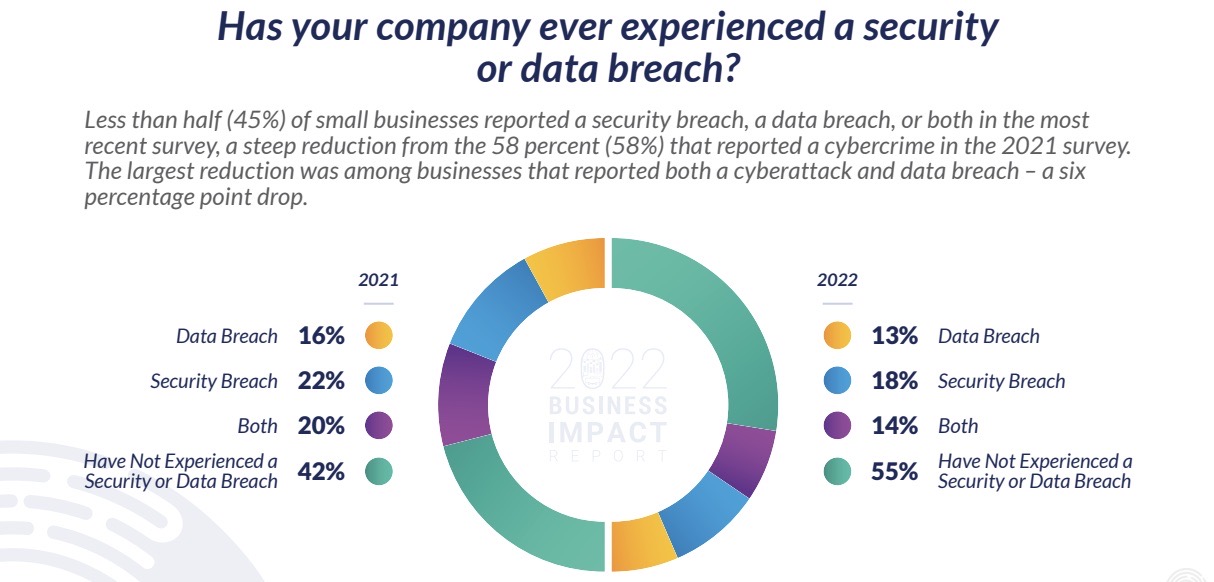
However, small businesses struggled to secure their social media accounts, with 50% reporting an account takeover in the past 12 months. Among those, 87% lost revenue as a result – including 39% who lost over $2,500.
The account takeovers happened because staffers clicked on phishing links, responded to a direct message, and/or inadvertently shared account credentials with scammers.
For more information, read the report and watch this webinar about it:
To learn about cybersecurity best practices for small businesses, check out these resources:
- “Cybersecurity for Small Businesses” (U.S. Federal Communications Commission)
- “Cybersecurity Toolkit for Small Business” (Global Cyber Alliance)
- “Protect Your Small Business” (U.S. Federal Trade Commission)
- “CyberSecure My Business” (National Cybersecurity Alliance)
- “Strengthen your cybersecurity” (U.S. Small Business Association)
- Cybersecurity Snapshot
- Exposure Management
