How Tenable Identity Exposure Helps You Adopt CISA's Latest Zero Trust Guidelines

Active Directory provides an essential foundation for zero trust architectures, so protecting it is critical. With Tenable Identity Exposure, you can continually assess the hygiene and security posture of your Active Directory system, reducing the risk of breaches. Here’s how.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently released an updated version of its Zero Trust Maturity Model (ZTMM) – a roadmap that federal agencies can use as they design, implement and evolve their zero trust architecture (ZTA).
The latest version updates implementation guidance across five key pillars -- identity; devices; networks; applications and workloads; and data. Each pillar consists of multiple maturity stages for agencies to follow as they evolve their zero trust strategy. The updated maturity model also adds a maturity stage – called the “initial” stage -- to the existing “traditional”, “advanced” and “optimal” stages.
Implementing a ZTA is a lengthy process that can take years to complete and that requires leveraging multiple, integrated technology solutions that support zero trust principles. In alignment with the U.S. National Institute of Standards and Technology’s (NIST) steps for transitioning to zero trust, CISA notes that before investing in zero trust capabilities, agencies should assess their current enterprise systems; resources; infrastructure and personnel; and processes.
This graphic represents the five pillars of the ZTMM, with cross-cutting capabilities: visibility and analytics; automation and orchestration; and governance.
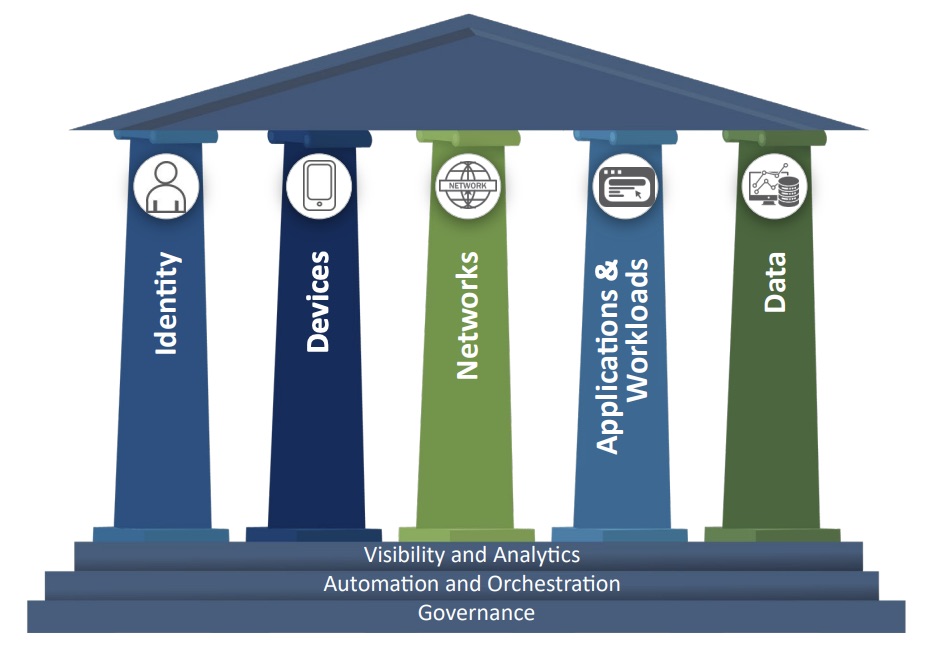
(Credit: CISA)
As outlined in NIST SP 800-207, a ZTA should adhere to seven tenets during design and deployment phases:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure, and communications and uses it to improve its security posture.
Using Tenable Identity Exposure to drive zero trust-maturity
Active Directory (AD) is the source of truth for authentication and authorization across on-premises and hybrid environments. Its use spans across all tenets and pillars of the zero trust framework. Therefore, AD security is critical in any ZTA as it is the core authentication and authorization system for network resources, devices, applications, identities and data.
To properly secure AD Security you must account for all of its areas and continually assess its hygiene and security posture. That way, you address both proactive and reactive controls and reduce the likelihood of AD compromise.
Using Tenable Identity Exposure (formerly Tenable.ad) as part of your ZTA ensures your AD system gets the comprehensive protection it requires so that you can find and fix weaknesses before attackers exploit them, and detect and respond to attacks in real time.
Tenable Identify Exposure helps secure your AD system by:
- Finding and fixing existing weaknesses through:
- immediate discovery, mapping and scoring of them
- step-by-step remediation tactics
- Maintaining hardened security settings through:
- instant detection of new weaknesses and misconfigurations
- breaking of attack pathways
- Detecting and responding to AD attacks in real time by providing:
- real-time alerts and actionable remediation plans
- the ability to see notification and trigger responses in your SIEM, SOAR or SOC
- honeypot configurations to attract and distract threat actors
- Enhancing incident response and threat investigations by letting you:
- search and correlate AD changes at object and attribute levels
- easily visualize attack pathways for AD objects and assets
How Tenable Identity Exposure aligns with CISA’s ZTMM pillars
ID
According to CISA, an “identity refers to an attribute or set of attributes that uniquely describes an agency user or entity, including non-person entities.”
Tenable Identity Exposure also continually surfaces AD security risks associated with incorrectly configured settings and exposes attack paths caused by misconfigured entitlements for both person and non-person identities. These risks are easily exploited in attacks for credential theft and data exfiltration in zero trust environments. Examples include: Users with blank passwords, stale accounts, privileges outside of security group memberships, insecure kerberos delegations on users accounts and a myriad of incorrectly configured domain level permissions and settings.
Device
CISA defines a device as, “any asset including (hardware, software, firmware, etc.) that can connect to a network including servers, desktop and laptop machines, printers, mobile phones, IOT devices, networking equipment and more.”
Tenable Identity Exposure identifies vulnerabilities and misconfigurations with Active Directory domain joined devices; including, and not limited to, restricting where privileged users can logon, unconstrained computer delegation, and obsolete OS.
Network
According to CISA, “a network refers to an open communications medium including typical channels such as agency internal networks, wireless networks and the internet, as well as other potential channels such as cellular and application-level channels used to transport messages.”
Different types of networks often rely on services from Active Directory like group membership and certificate services. Tenable Identity Exposure ensures that these resources are properly configured and secured. Examples: Mapped Certificates on Accounts, ADCS Dangerous Misconfigurations, use of Weak Cryptography Algorithms in AD PKI as well as the ability to monitor changes associated with any groups that are used to gain access to networks.
Applications and Workload
CISA states “Applications and Workloads include agency systems, computer programs, and services that execute on-premises, on mobile devices and in cloud environments.”
Tenable Identity Exposure identifies AD misconfigurations and vulnerabilities in Active Directory. Applications and workloads are often domain joined or use service accounts from AD. Tenable.ad identifies misconfigurations with the accounts and infrastructure running these applications. Examples include Privileged Accounts Running Kerberos Services, Dangerous Delegations, misconfigured Active Directory certificates Etc.
Data
According to CISA, “Data includes all structured and unstructured files and fragments that reside or have resided in federal systems, devices, networks, applications, databases and backups (including on-prem and virtual environments, as well as the associated metadata.”
Tenable Identity Exposure identifies AD misconfigurations and vulnerabilities in Active Directory. Data is often secured by AD groups and the hosts are often domain joined or use service accounts from AD. Tenable.ad identifies misconfigurations with the accounts and infrastructure running these applications. Examples include Privileged Accounts Running Kerberos Services, Dangerous Delegations, misconfigured Active Directory certificates Etc.
Tenable Identity Exposure and Tenable One
Tenable Identity Exposure is available as a standalone solution or as part of the Tenable One Exposure Management Platform. The Tenable One platform unifies a variety of data sources into a single solution to give you a complete perspective of risk and the ability to prioritize the most critical vulnerabilities across all asset types. It combines the broadest vulnerability coverage spanning identity systems, web applications, IT assets, cloud resources and containers; builds on the speed and breadth of Tenable Research; and adds comprehensive analytics to prioritize actions and communicate risk.
With Tenable One, you are able to view identity system data, and all other asset and vulnerability information in one place. Unified dashboards and reporting allow for clear communications of security status and trends.
Tenable One을 사용하면 조직은 다음을 할 수 있습니다.
- 최신 공격 표면 전반에 걸쳐 포괄적인 가시성 확보
- 위협을 예측하고 공격을 방지하기 위해 작업의 우선 순위 지정
- 더 나은 결정을 내리도록 사이버 위험을 커뮤니케이션
For more information read our solution brief “Rethinking Your Security With a Zero Trust Approach” or visit the Tenable Identity Exposure page.
- Active Directory
- Federal



