Microsoft’s October 2020 Patch Tuesday Addresses 87 CVEs including “Bad Neighbor” Windows TCP/IP Vulnerability (CVE-2020-16898)

For the first time in seven months, Microsoft patches less than 100 CVEs, addressing 87 CVEs in its October release.
Microsoft patched 87 CVEs in the October 2020 Patch Tuesday release, including 11 CVEs rated critical. This release follows seven consecutive months of over 100 CVEs patched, in what has been an unusually busy year for Microsoft Patch Tuesday updates. This month's release includes fixes for Microsoft Windows, Microsoft Office and Microsoft Office Services and Web Apps, Microsoft JET Database Engine, Azure Functions, Azure Sphere, Open Source Software, Microsoft Exchange Server, Visual Studio, PowerShellGet, Microsoft .NET Framework, Microsoft Dynamics, Adobe Flash Player, and Microsoft Windows Codecs Library.
CVE-2020-16898 | Windows TCP/IP Remote Code Execution Vulnerability
CVE-2020-16898, dubbed “Bad Neighbor,” is a critical remote code execution (RCE) vulnerability within the Windows TCP/IP stack. The vulnerability exists due to improper handling of ICMPv6 Router Advertisement packets using Option Type 25 and an even length field. According to a blog post from McAfee, Microsoft Active Protections Program (MAPP) members were provided with a test script that successfully demonstrates exploitation of this vulnerability to cause a denial of service (DoS). While the test scenario does not provide the ability to pivot to RCE, an attacker could craft a wormable exploit to achieve RCE. While an additional bug would be required to craft an exploit, it is likely that we will see proof-of-concept (PoC) code released in the near future.
CVE-2020-16899 | Windows TCP/IP Denial of Service Vulnerability
Similar to CVE-2020-16898, CVE-2020-16899 is a DoS vulnerability within the Windows TCP/IP stack. The vulnerability also results from the improper handling of ICMPv6 Router Advertisement packets. Exploitation of this flaw requires an attacker to send crafted ICMPv6 Router Advertisement packets which could cause the system to stop responding. While Microsoft does recommend applying the security update to patch this flaw, a workaround is available via a PowerShell command to disable ICMPv6 RDNSS (Recursive DNS Server) in the event the patch cannot be immediately applied.
CVE-2020-16951, CVE-2020-16952 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2020-16951 and CVE-2020-16952 are RCE vulnerabilities in Microsoft SharePoint resulting from a failure to validate an application package’s source markup. To exploit the vulnerability, an attacker would need to be able to upload a specially crafted SharePoint application package to a vulnerable SharePoint server. Successful exploitation could allow an attacker to execute arbitrary code under the context of the SharePoint application pool and the SharePoint server farm account.
Steven Seeley, a security researcher on Qihoo 360’s Vulcan Team, is credited with discovering CVE-2020-16952. Seeley published an advisory on his website, which includes a PoC exploit script for the vulnerability.
CVE-2020-16947 | Microsoft Outlook Remote Code Execution Vulnerability
CVE-2020-16947 is an RCE flaw in Microsoft Outlook due to the improper handling of objects in memory. An attacker can exploit this vulnerability using a crafted email file sent to a user of a vulnerable version of Microsoft Outlook. Because Outlook’s Preview Pane is affected by this flaw, a user does not have to open the message in order for the vulnerability to be exploited. As Outlook is widely used for enterprise email, we highly recommend prioritizing the patching of this CVE.
CVE-2020-16929, CVE-2020-16930, CVE-2020-16931, CVE-2020-16932 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2020-16929, CVE-2020-16930, CVE-2020-16931 and CVE-2020-16932 are RCE vulnerabilities in Microsoft Excel because of the way the software improperly handles objects in memory. To exploit these vulnerabilities, an attacker must create a malicious Excel file and convince their target to open the file using a vulnerable version of Microsoft Excel, either by attaching the file to an email or hosting it on a website and enticing a user to visit the website. Successful exploitation would allow an attacker to gain arbitrary code execution on the vulnerable system with the same rights as the current user. Exploitation of this vulnerability could be exponentially worse if the current user has administrative privileges, which could grant the attacker the ability to perform a complete takeover of the vulnerable system.
CVE-2020-16918, CVE-2020-17003 | Base3D Remote Code Execution Vulnerability
CVE-2020-16918 and CVE-2020-17003 are RCE vulnerabilities in Base3D because its rendering engine handles memory improperly. Successful exploitation of these vulnerabilities would allow an attacker to gain arbitrary code execution on a vulnerable system.
CVE-2020-1167, CVE-2020-16923 | Microsoft Graphics Components Remote Code Execution Vulnerability
CVE-2020-1167 and CVE-2020-16923 are RCE vulnerabilities in Microsoft Graphics Components because of the way objects are handled in memory. To exploit these vulnerabilities, an attacker must create a specially crafted file and convince their target to open the file. This could be achieved through targeted social engineering. Successful exploitation would allow an attacker to gain arbitrary code execution on the vulnerable system.
CVE-2020-16891 | Windows Hyper-V Remote Code Execution Vulnerability
CVE-2020-16891 is an RCE vulnerability on the host server of Windows Hyper-V when inputs from an authenticated user on the guest operating system (OS) are not properly validated. To exploit this vulnerability, an attacker would need to run a malicious application on the guest OS, which could result in arbitrary code execution on the host OS.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains October 2020.
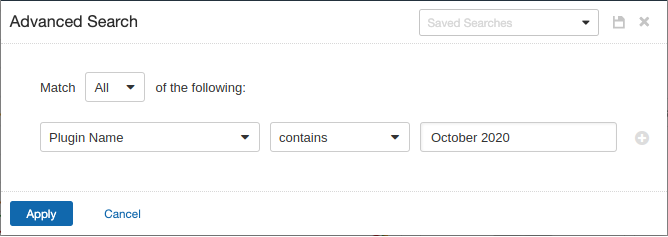
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example using March 2019 from Tenable.io:
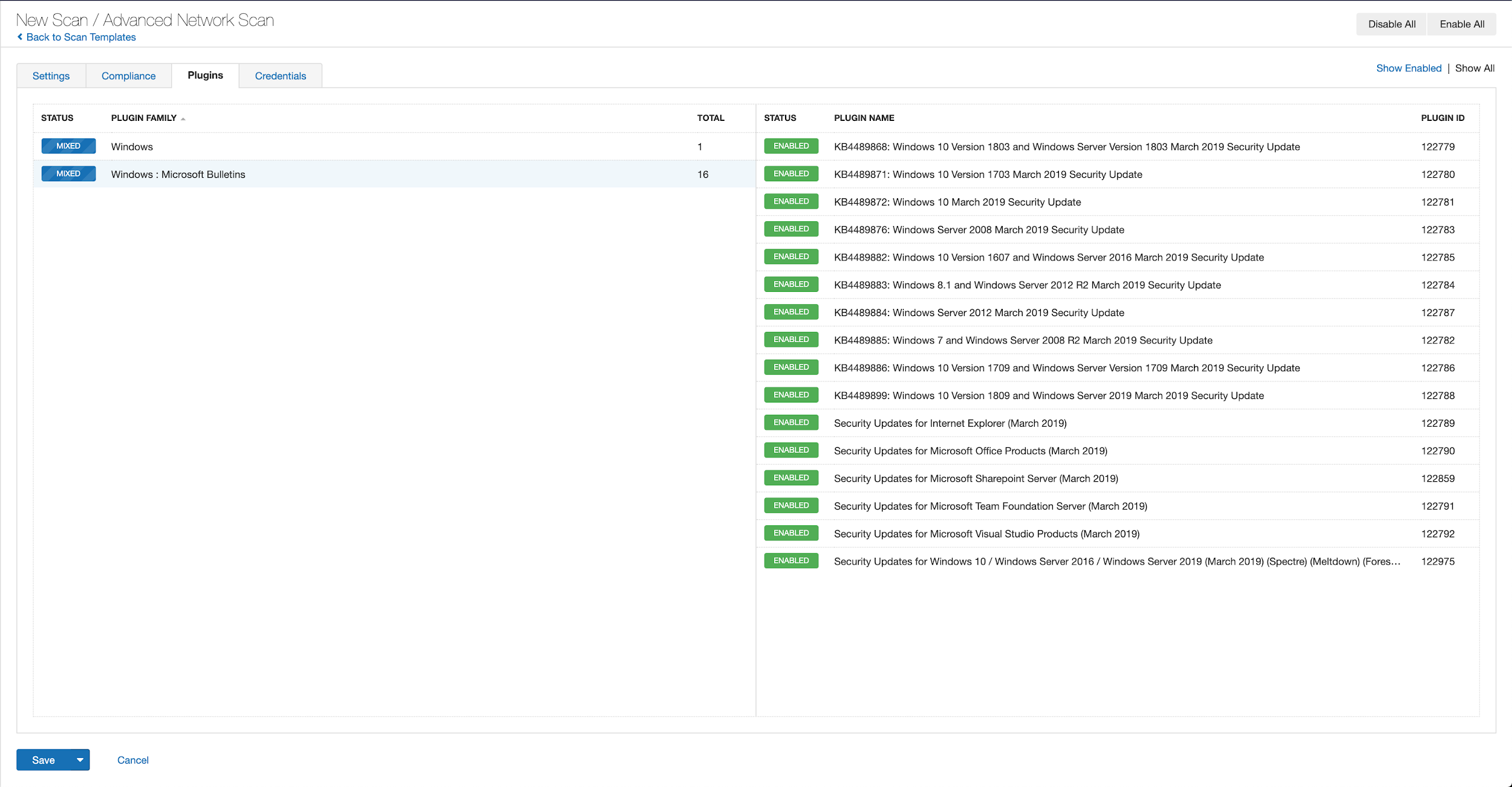
A list of all the plugins released for Tenable’s October 2020 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's October 2020 Security Updates
- Tenable plugins for Microsoft October 2020 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

