OpenAI의 ChatGPT 및 GPT-4가 피싱 이메일 및 Twitter 스캠에서 가짜 OpenAI 토큰을 홍보하는 미끼로 사용

Hoping to cash in on the massive interest around OpenAI’s GPT-4 – ChatGPT’s new multimodal model – scammers have launched phishing campaigns via email and Twitter designed to steal cryptocurrency. Check out how they’re carrying out the scams and how you can avoid becoming a victim.
Background
On March 15, one day after the eagerly anticipated launch of OpenAI’s Generative Pre-trained Transformer Version 4 (GPT-4) in its artificial intelligence chatbot, ChatGPT, and via APIs for developers, scammers have begun sending phishing emails and tweeting phishing links to cryptocurrency enthusiasts about a fake OpenAI token.
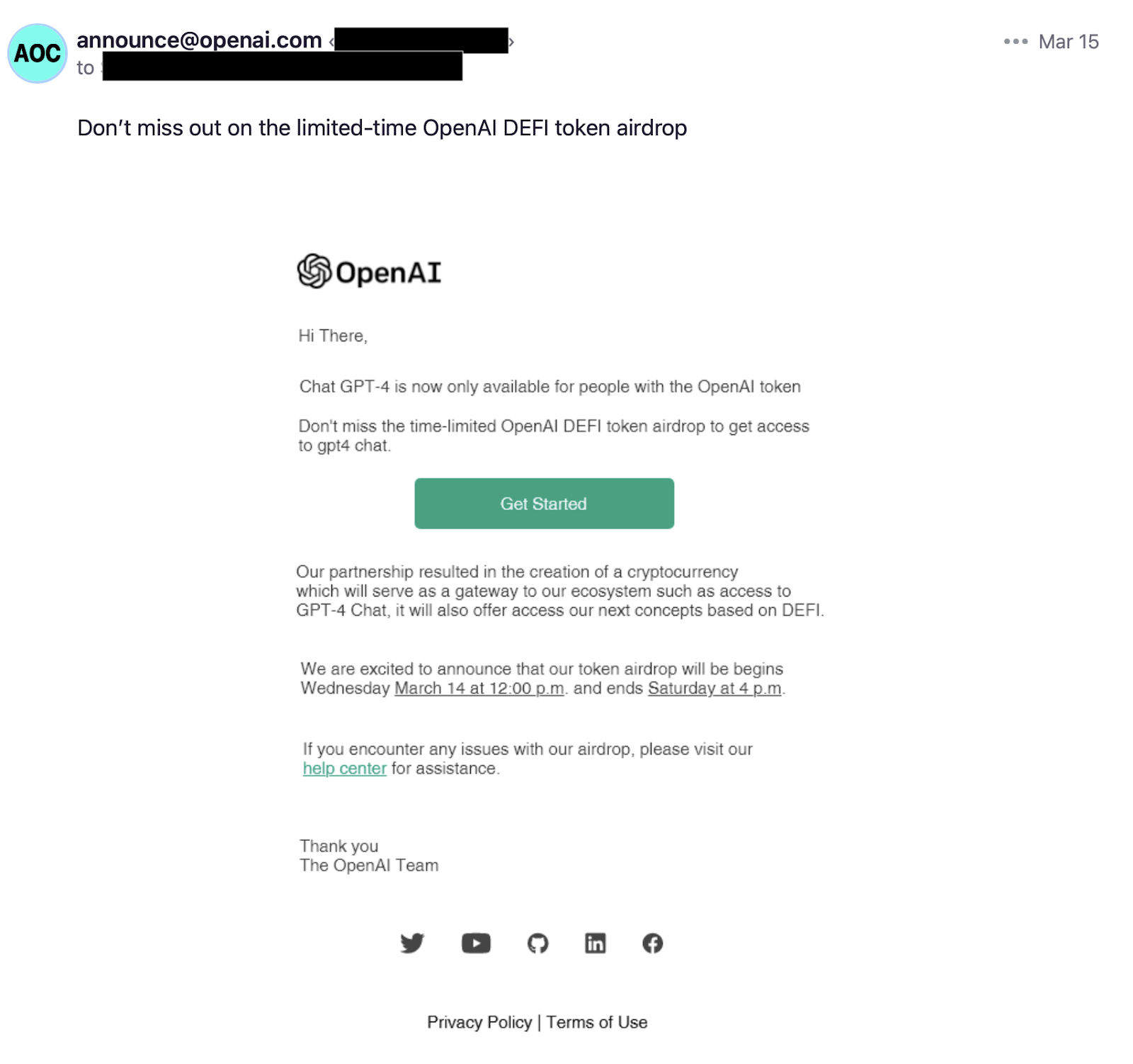
At the time this blog post was published, OpenAI only provides GPT-4 access to ChatGPT Plus subscribers and developers via its API. The unintended effect from this limited access is that scammers have an ideal hook to lure unsuspecting users to their phishing sites.
The phishing email itself only contains a single block of text: “Don’t miss out on the limited-time OpenAI DEFI token airdrop.” It includes an image of an OpenAI email based on a template of what a legitimate OpenAI email might look like. However, the purported email contains a number of grammatical and spelling errors.
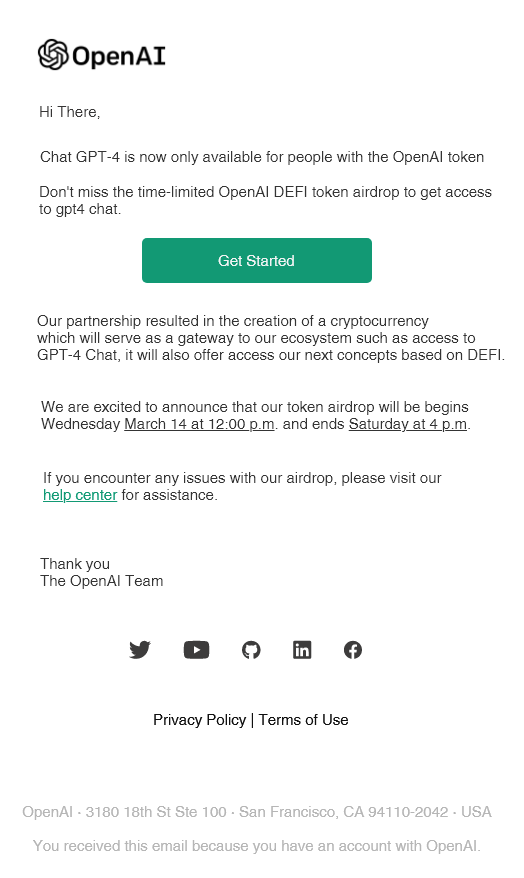
The phishing email claims that GPT-4 is “now only available for people with the OpenAI token.” This aligns with OpenAI’s choice to limit GPT-4 access, giving some legitimacy to the scam itself. However, the email also includes the wrong date, claiming that the “token airdrop” will start on Wednesday, March 14, when in fact, Wednesday was March 15.
Email messages sent to variety of users; possible link to crypto data breach
It is unclear how the scammers are targeting users through this campaign. I can’t say definitively if these scammers have managed to obtain a list of OpenAI users. One possibility is that the scammers managed to build a target list by using breach data obtained from SendGrid, which exposed information on users of the crypto tax service, CoinTracker.
Compromised Twitter accounts impersonate OpenAI to promote GPT-4 scam
On March 16, journalist Zack Abrams tweeted a photo of a tweet mention he received from a compromised Twitter account impersonating OpenAI. Abrams called the scam attempt “decent” adding that the “Picture, name, and blue check matches the real OpenAI.”
If you're curious what it's like being a journalist who covers crypto... I get about five of these in my mentions every day.
Decent scam attempt! Picture, name, and blue check matches the real OpenAI, though obviously the @ is a giveaway. pic.twitter.com/zTcCZkPGTI— Zack Abrams (@ZackDAbrams) March 16, 2023
The image of the tweet from Abrams also shows scammers promoting a “$GPT coin” saying that it may be “distributed to GPT-4 crypto users.”
Fake cryptocurrency giveaways on social media aren’t new, and spamming a user’s Twitter mentions has become a key component in the persistence of these types of crypto scams.
Phishing website looks like the OpenAI website
If a user clicks on the link in the phishing email, they’re directed to a website that looks very similar to the real OpenAI website for ChatGPT and GPT-4.
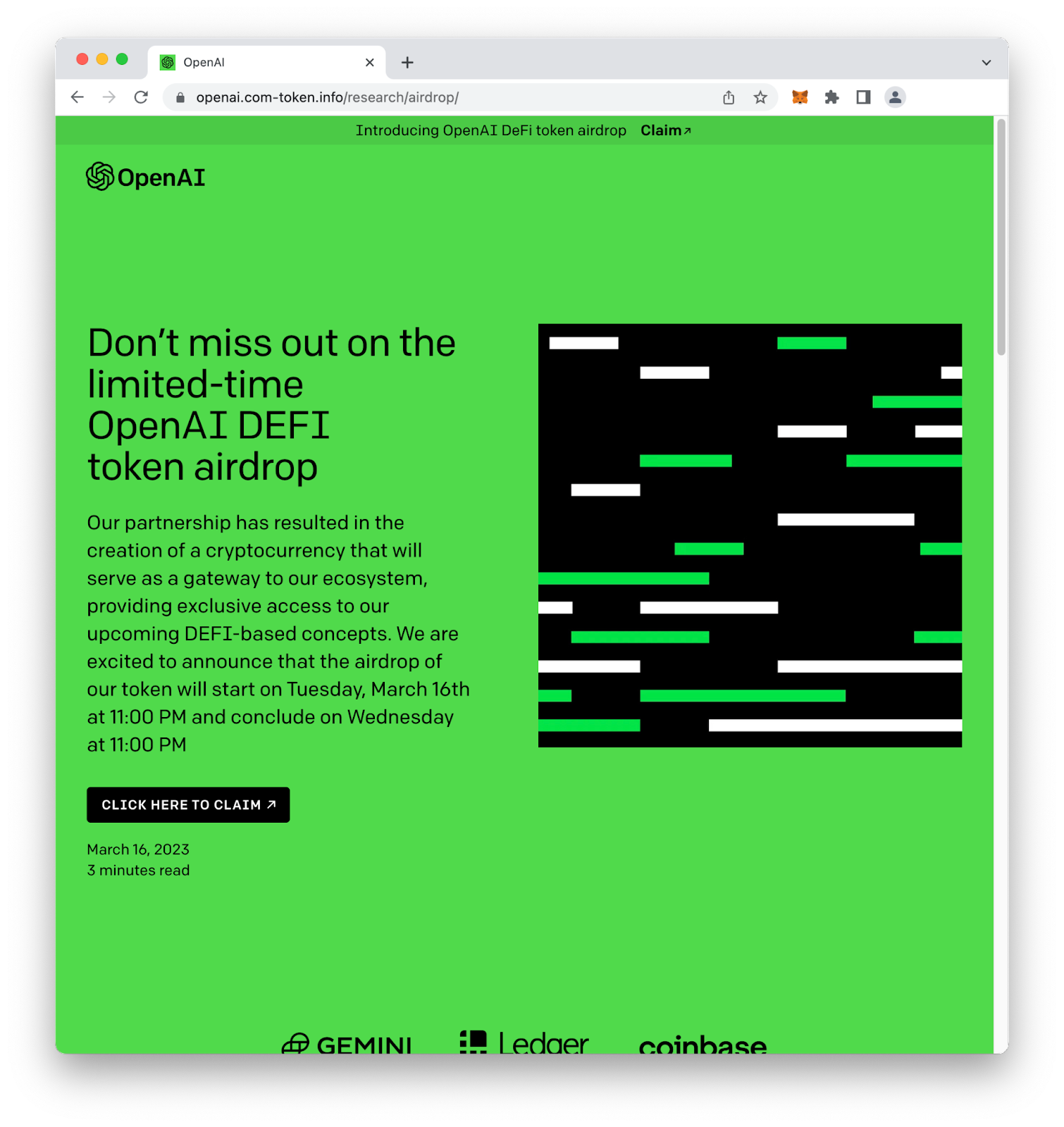
However, one primary difference in the phishing website is that it is promoting the “limited-time OpenAI DEFI token airdrop.” Using language like “limited-time” is linked to one of the key ingredients in cryptocurrency scams: scarcity. Stating that a “limited” number of tokens are being distributed for a “limited” time creates a sense of urgency. This leads to a fear of missing out, or FOMO, thus increasing the chances that potential victims will ignore red flags, such as the incorrect date (Tuesday was March 14, not March 16) or how decentralized finance should be stylized as DeFi not DEFI.
Another notable aspect of this phishing site is that it uses a hyphen in the domain name to allow the first half of the URL to appear as though it’s main domain is “openai.com.” This is achieved by using the subdomain “openai” with a second-level of “.com-token” followed by the top level domain of “.info.”

The website contains text claiming that holders of the fake OpenAI Token will receive exclusive access to preview “upcoming products” and test prototypes ahead of a public release. The scammers also specify that the OpenAI token will be designated with a token symbol of $OAI. At the time this blog post was published, OpenAI had not launched a cryptocurrency token and any tokens on the Ethereum blockchain using the symbol $OAI are not affiliated with OpenAI.
Connecting your wallet to a phishing site
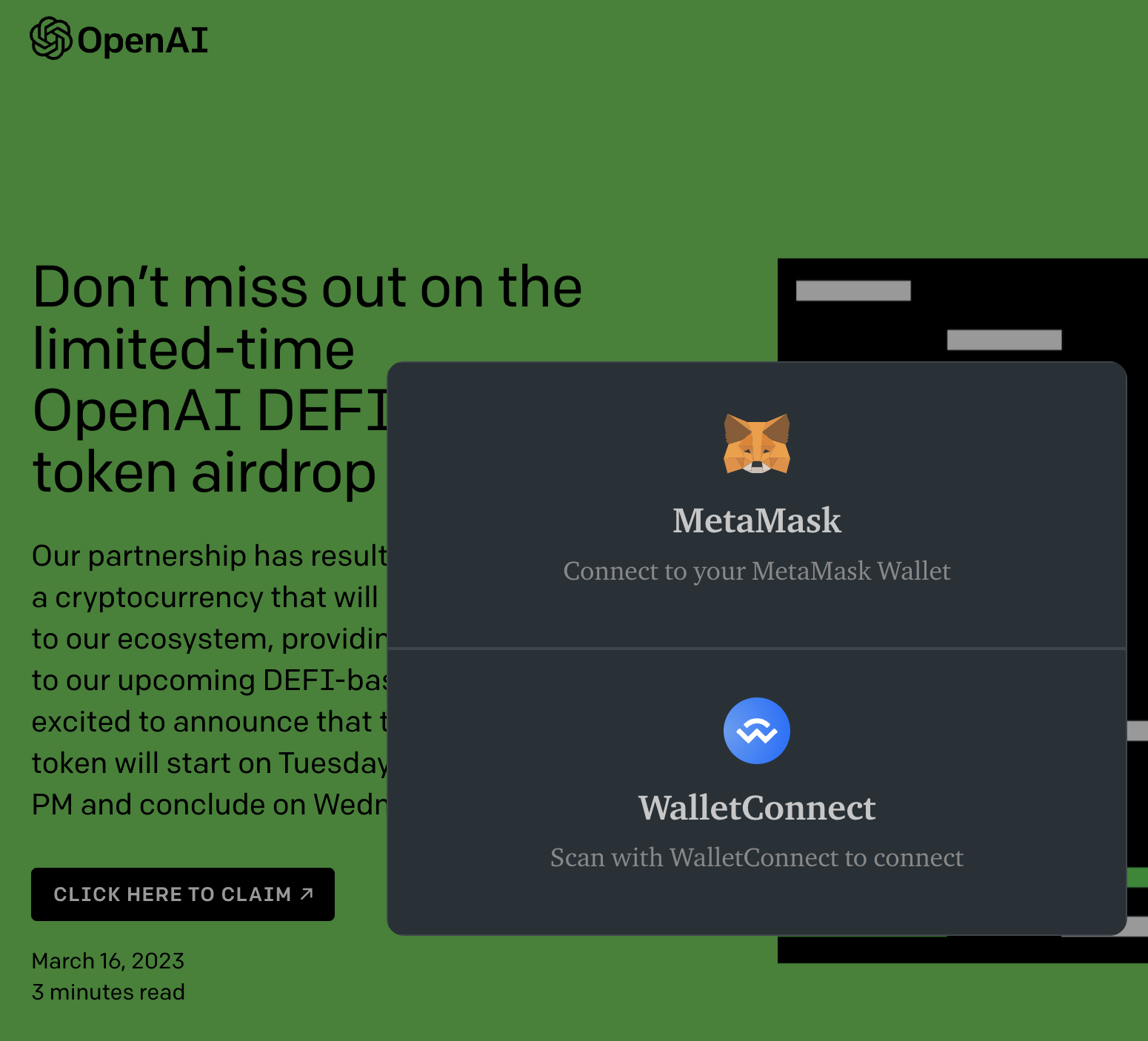
In order to “claim” the alleged OpenAI tokens, users are instructed to click a button that says “click here to claim,” which presents options for connecting your wallet to the website. This process is familiar to most cryptocurrency users, who often connect their wallets to decentralized apps or dApps for short. Because this is a familiar process, users may not think twice about connecting their wallet to this phishing site. Users are given an option to connect using the popular browser-based cryptocurrency wallet, MetaMask, or WalletConnect, a way to connect over 170 wallets to dApps.

Once connected, the phishing website is capable of stealing all the cryptocurrency tokens in the wallet, including non-fungible tokens (NFTs) automatically by transferring them to their own wallet. Once these tokens are transferred, the likelihood of recovery is slim to none.
Airdrops are a convenient way to scam cryptocurrency users
An airdrop is a type of event in the cryptocurrency space where users are rewarded with free tokens based on their participation in a protocol. The terminology is familiar, which makes it a convenient way for scammers to take advantage of users that are anticipating an airdrop, hoping to participate in an already announced airdrop, or even instances where no airdrop is planned. For example, the Arbitrum Foundation recently announced plans to conduct an airdrop. Within a day of this announcement, scammers have already replicated the Arbitrum Foundation website template as part of a phishing website.
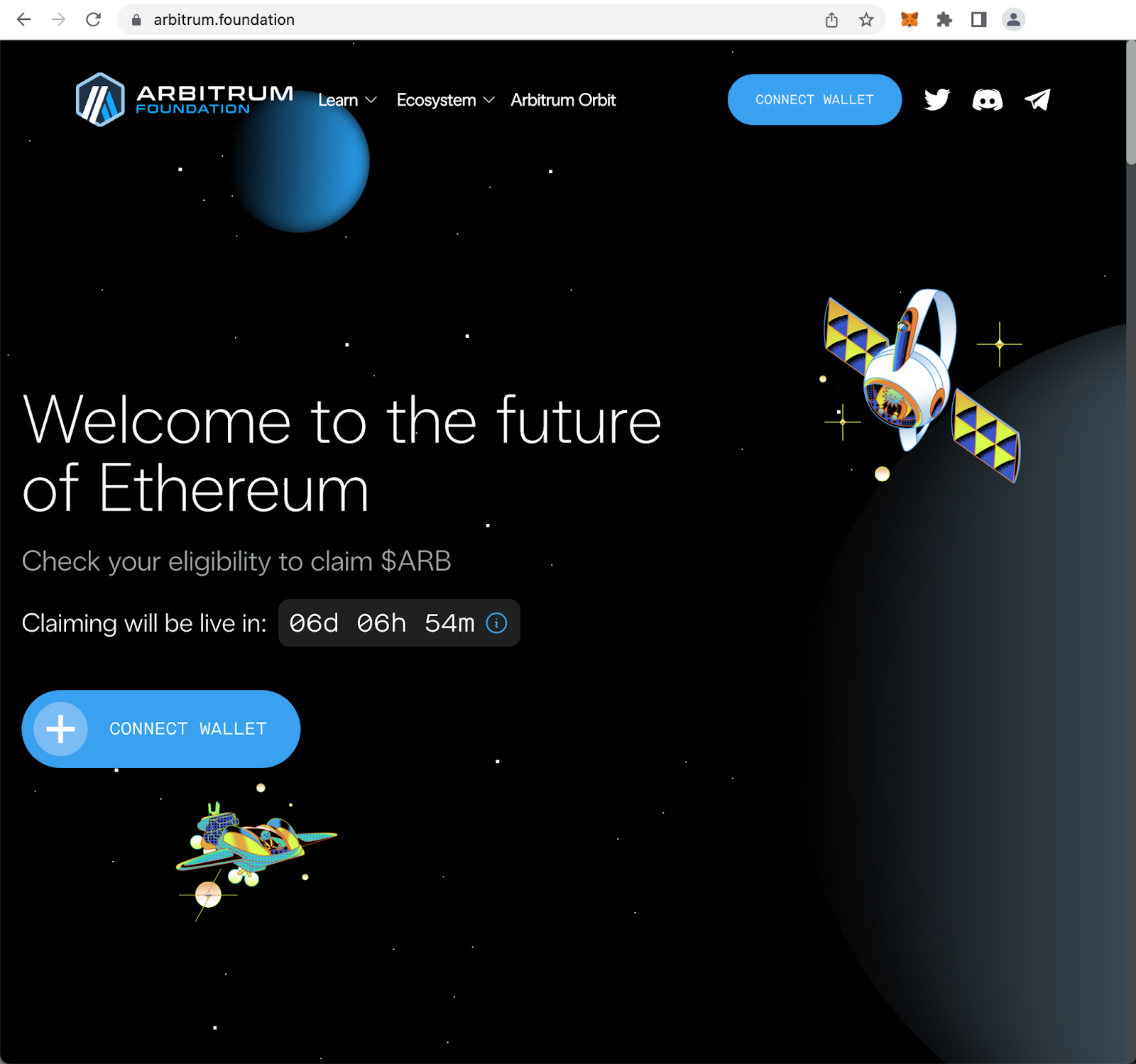
Example of the real Arbitrum Foundation website promoting an airdrop of its $ARB tokens
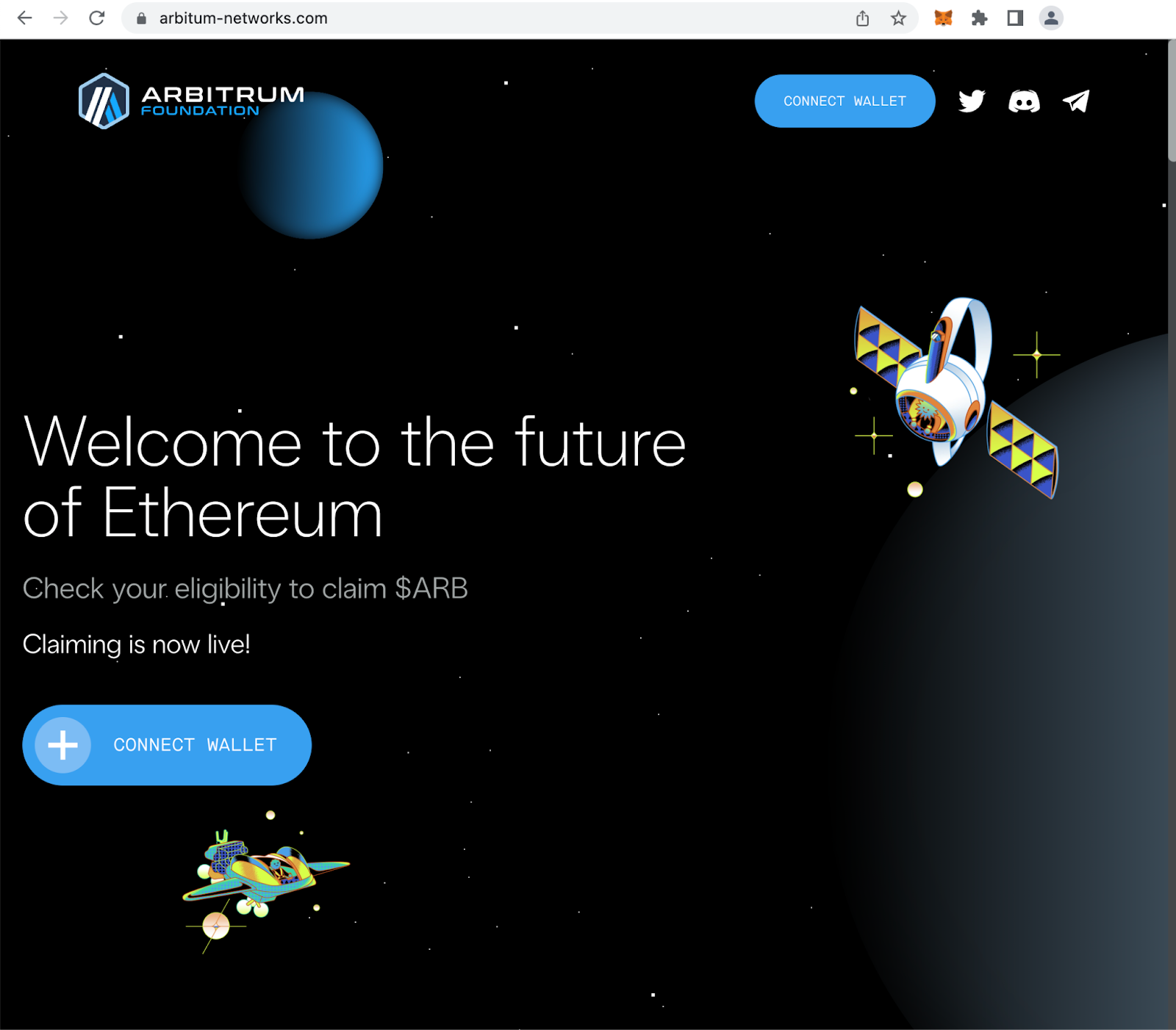
Example of a phishing site designed to look just like the real Arbitrum Foundation website
Unlike Arbitrum, Coinbase also announced the launch of Base, its own layer-2 scaling solution for Ethereum, but noted that there would be no native token for Base.
1/ Important: Base is *not* a token
We do not plan to issue a new network token for Base and will use ETH as the native gas token.— Base (@BuildOnBase) February 23, 2023
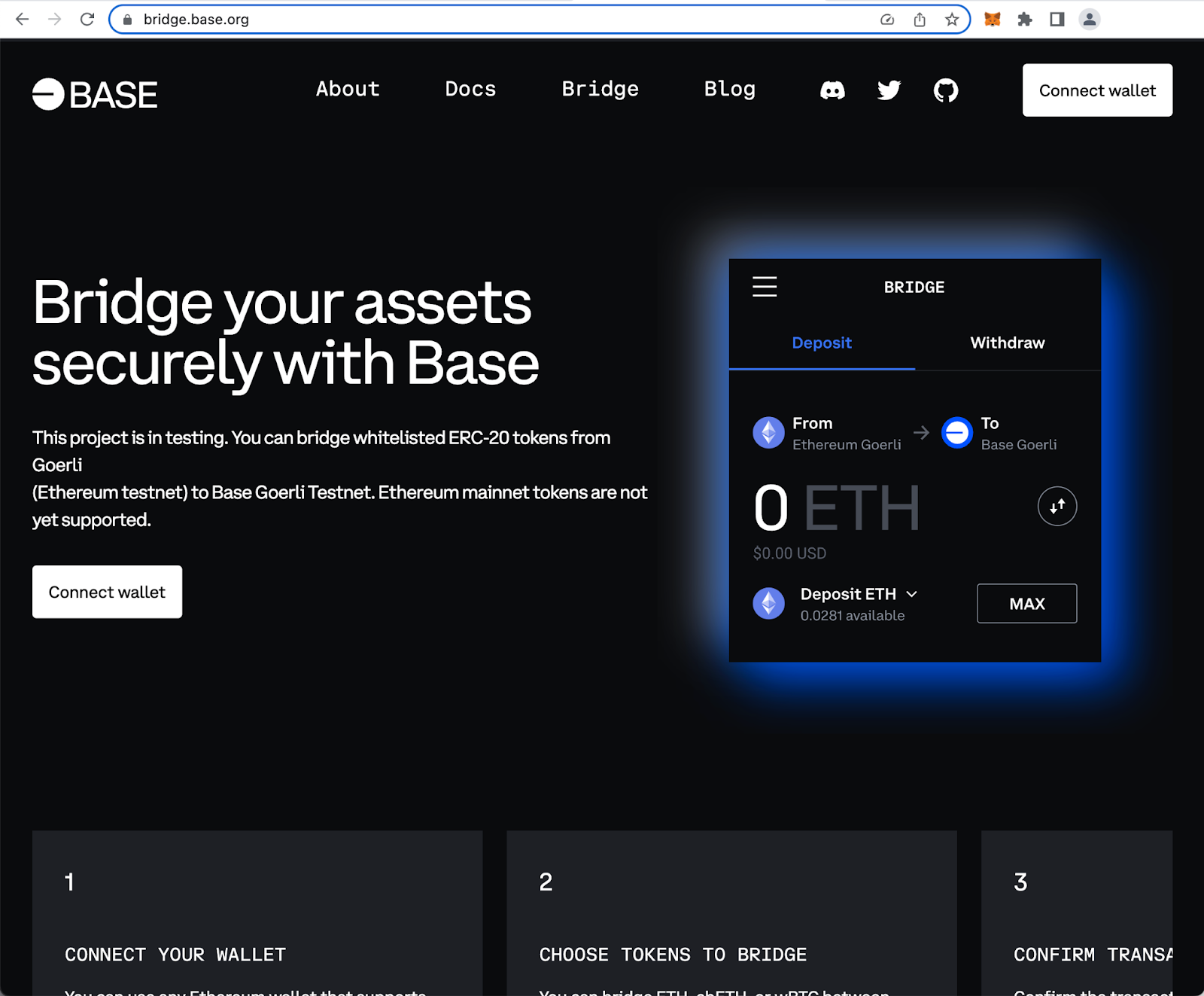
However, that hasn’t stopped scammers from creating a Base phishing site promoting an airdrop of $BASE tokens.
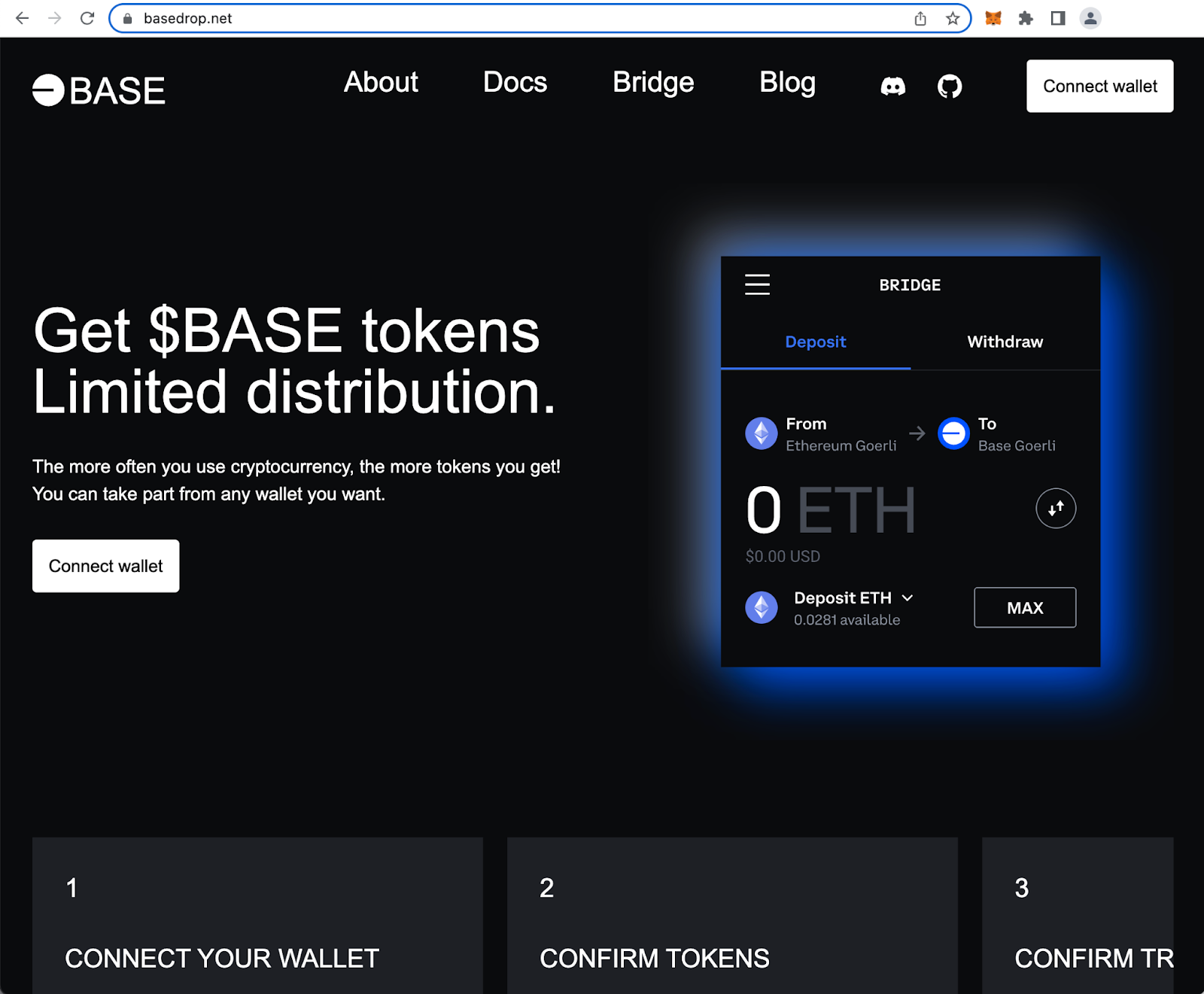
Cryptocurrency scams continue to impersonate popular brands and new technology
If there’s one thing I’ve learned over the last few years it’s that cryptocurrency scammers are opportunistic, impersonating noteworthy individuals or brands to promote fake tokens like Tesla tokens and SpaceX tokens as well as a plethora of fake giveaways. The impersonation of OpenAI and the promotion of a fake OpenAI token continues this trend.
For users interested in GPT-4 and ChatGPT or cryptocurrency and the blockchain, it’s paramount that they continue to operate with a high degree of skepticism when it comes to cryptocurrency giveaways and token airdrops. Continue to do your own research (DYOR) before connecting your wallets to such websites.
- Exposure Management



