Should You Still Prioritize Exploit Kit Vulnerabilities?

One of the greatest challenges that enterprises face is prioritizing vulnerabilities for remediation. Trying to determine which vulnerabilities pose a true imminent risk deserving of immediate attention can feel like a game of Whac-A-Mole due to the sheer volume of critical vulnerabilities.
An analysis of CVE data by Tenable Reseach’s Lucas Tamagna-Darr shows the number of disclosed vulnerabilities has grown on average by 15 percent year-over-year – with more than 12,000 unique vulnerabilities being added to CVE in 2017 alone! Of these, over 3,500 were rated with a High or Critical severity. That’s an average of almost 10 per day. And the situation is only getting more overwhelming – we project the total number of disclosed vulnerabilities will grow to above 15,000 in 2018.
Strategic remediation prioritization – know which vulnerabilities pose the biggest risk
The objective of strategic vulnerability remediation prioritization is to identify the vulnerabilities that pose the greatest actual risk to an organization. Many organizations rely on the Common Vulnerability Scoring System (CVSS) to prioritize. But, this yields far too many “critical” vulnerabilities for most organizations to realistically remediate or mitigate given the time and resources available to them. CVSS does a good job of generally evaluating the risk that a specific vulnerability poses. However, it fails to identify which vulnerabilities represent a true risk to a specific organization.
Shifting paradigms – Cyber Exposure management
Situational awareness is now a necessary component of an effective remediation prioritization strategy. This approach is sometimes called threat-centric, intelligence-driven, adversary-focused vulnerability management.
At Tenable, we call this Cyber Exposure. The Cyber Exposure discipline focuses on vulnerabilities that are actively being exploited in the wild by malware, ransomware, Exploit Kits (EKs) and threat actors and are therefore most likely to lead to an actual data breach. Ideally, the business criticality and context of an asset are also correlated to fully assess your Cyber Exposure. The objective is to filter down the overall volume of critical vulnerabilities to a manageable amount that merits immediate prioritization for remediation.
So, situational awareness becomes key. We must take into account adversaries’ activities in the wild and their actual Tactics, Techniques and Procedures (TTPs). Let’s stop looking at vulnerabilities in isolation and “all things being equal.” We should instead look at potential threats and their associated vulnerabilities to identify which ones subsequently represent the greatest risk. For that, you need to evaluate the threats themselves – to determine if they should be on your “watch list.”
Exploit Kits have been a prominent potential threat for enterprises for the past decade, targeting unsuspecting users by infecting them with malware via compromised websites. In the past year, active EK deployments – and their development by cyber criminals – has dropped. So, let’s take a look at whether EKs and the vulnerabilities they target still represent a critical, real-world risk that need to be prioritized first for remediation.
What is an Exploit Kit?
Exploit Kits are used to embed malicious code into a website. They provide pre-packaged exploits that target unpatched browsers and applications. There’s a thriving commercial market offering EKs. And many are easy to use, even by less technical cyber criminals. EKs generally target client-side vulnerabilities.
The majority of attacks using EKs infect a target without their knowledge, through two primary methods:
Opportunistic drive-by-exploitation
Cyberattackers will exploit vulnerable web servers to deploy the EK. They embed malicious code in websites, which can infect any visitor with a vulnerable web browser or enabled libraries and plugins.
Targeted exploitation through phishing
Attackers either set up their own website to deploy the EK or exploit a vulnerable website to do so. They then send a crafted email to a potential victim that includes a link to the infected website in the hope the target will click the link and visit the site.
Historically, the primary objectives when deploying EKs were stealing credentials and banking information, deploying ransomware and using the infected machines as bots in DDoS attacks. More recently though, threat actors are repurposing EKs to mine cryptocurrencies (so-called “drive-by-mining”).
Analysis
We analyzed many different EK’s1 using a variety of sources2 to gather a list of commonly targeted vulnerabilities (see below):
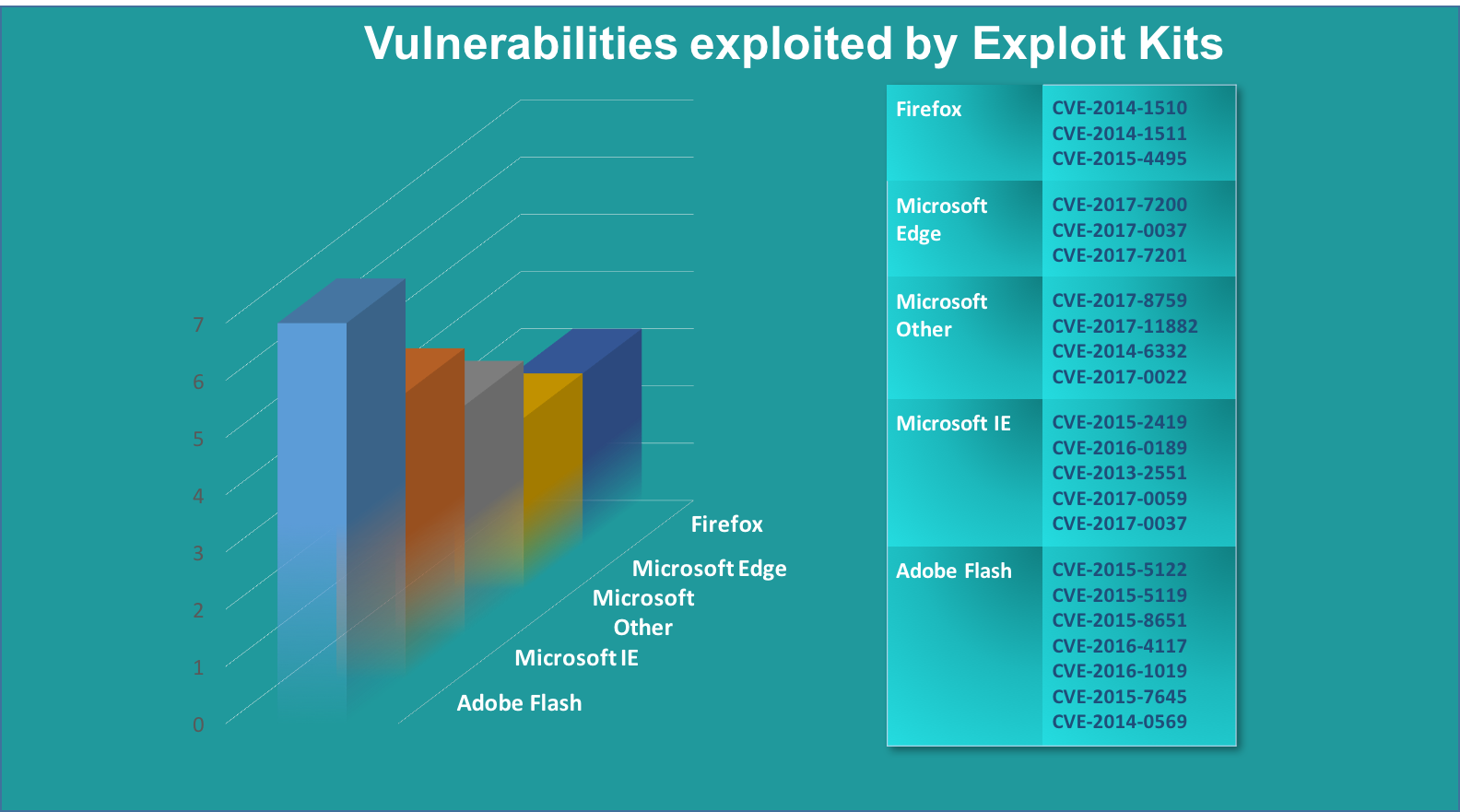
The first thing that’s noticeable is how old many of the targeted vulnerabilities are – some CVEs date back to 2014! Adobe Flash still dominates the top lists. (Although new exploits targeting Flash have become less common, reflecting its shrinking prevalence in the wild.)
In second place come Microsoft applications, specifically Internet Explorer, Edge and their associated libraries. These targeted vulnerabilities are more recent, with the majority disclosed in 2017.
Threat actors are not dumb. Like any commercial endeavor, they focus on return on investment (ROI). The fact they’re still targeting old vulnerabilities shows they’re still achieving some success with them. But, it also shows that EK developers are having to rely on older vulnerabilities, indicating a lack of more recent effective exploits.
This also isn’t the first time that EKs have faced declining effectiveness. Prior to 2016, EKs primarily targeted Java vulnerabilities, but pivoted to exploiting Flash due to the declining availability of effective Java exploits.
Our own analysis indicates the vulnerabilities currently being targeted by EKs have a very low prevalence in customer environments. That’s not surprising, considering the age of many of them. But, it’s important to note that our own data set is focused on organizations that conduct active vulnerability management. This is not always the case. A recent joint report from Ponemon and ServiceNow states that 37% of the enterprises they surveyed that had experienced a breach in the past 24 months did not scan for vulnerabilities at all. Home users and many small businesses also often do not actively manage vulnerabilities.
Conclusion: Exploit Kits are in decline – for now
An observant and facetious reader may say the best defensive strategy to protect against EKs is to dump Internet Explorer and Adobe Flash. And there is, in fact, a lot of merit in that advice.
Other browsers are far less commonly exploited by EKs, most obviously Google Chrome, despite a market share of just over 60 percent. Flash is already being phased out, with the proportion of Flash-enabled sites rapidly declining. In addition, Flash will be EOL in 2020. Aside from legacy applications and dependencies, there’s no good reason for anyone to still have Flash installed.
Real-world EK activity has been observed to be on the decline in the past 24 months. From 2016 to 2017, EK deployments, measured by the volume of websites serving EKs, has dropped by 300%, according to some sources. The active development of EKs has also declined by as much as 62%.
There are a variety of reasons for this. Arrests of cyber criminals offering EKs and the concerted takedown of EK infrastructure by law enforcement and tech companies have had an impact. But a primary reason for the decline is based on a lack of effective client-side exploits and subsequently vulnerable targets.
More generally, our overall conclusion is EKs are not the risk they once were. They don’t warrant the same strategic focus as in past years.
To be clear, we’re not saying that you should not remediate the targeted vulnerabilities if you have the resources. But, if your objective is to identify the threats and associated vulnerabilities for remediation that reduce the most amount of real-world risk, EKs right now don’t make the top of the list.
But this will also always depend on what specific software you have deployed and the maturity of your vulnerability management program. If you’re still heavily using IE and have older versions of Flash installed, EKs still pose a relevant threat.
We should also not make the mistake of interpreting a EK hiatus as the final gasp. The rumors of the death of EKs may have been exaggerated. EK developers can easily add new exploits as they become available. An EK is, by design, a delivery platform for exploits, weaponizing them to automate attacks. The amount of suitable and effective vulnerabilities for weaponization in EKs has currently shrunk. And browser security mechanisms have improved. But, it’s unclear if this will be permanent or if a new wave of discovered vulnerabilities will breathe new life into EKs as a critical threat.
The EK model is mature, tried and tested. And we’re already seeing them being repurposed for other tasks. While the names of the actors may change and the stage is smaller, the play itself has actually become more lucrative if we consider the rise in drive-by-mining.
For now, EKs represent a diminished risk compared to prior years. But, let’s not get complacent. The threat environment is dynamic and constantly evolving. We’ll be monitoring threat activity in case this changes again in the future.
Notes
- These included Neutrino, Hunter, RIG, Disdain, Terror, Magnitude, Electroneum, XMRig, Astrum, Gh0st RAT, Nuclear Pack, Angler, Sundown and Kaixin
- Recorded Future, Talos, ZScaler, Palo Alto, Symantec and various blogs