모든 것을 수정할 수는 없습니다: 취약성 수정에 대해 위험 정보에 기반한 접근 방식을 사용하는 방법

Frameworks and standards for prioritizing vulnerability remediation continue to evolve, yet far too many organizations rely solely on CVSS as their de facto metric for exposure management. Here, we discuss other important frameworks and provide guidance on how Tenable can help.
A successful exposure management program requires having a strategy for prioritizing vulnerability remediation in the most efficient and effective manner possible. Given the number of CVEs published in the National Vulnerability Database (NVD) every year — over 20,000 in 2022 — and the fact that a number of those CVEs may require fixes in multiple products, it is not feasible for security and IT teams to fix everything.
Unfortunately, until recently the frameworks and standards used in the industry to help identify and prioritize which vulnerabilities to fix first have either failed entirely or fallen short. There are many factors that could be considered for determining what makes one vulnerability more important to remediate than another, and every organization will have their own unique requirements and expectations. Yet, in every case there are three foundational elements that should be considered in order to take a risk-informed approach to vulnerability management. These elements are:
- Impact: What is the impact to the affected application or system, as well as the organization, if the vulnerability is successfully exploited? Understanding the impact any given vulnerability can have in your particular organization is critical to prioritizing which ones to fix first.
- Likelihood of exploitation: Not all vulnerabilities are created equally and some are easier to exploit than others. Many attackers will aim for the lowest hanging fruit, so understanding which vulnerabilities are actually feasibly exploitable or are being actively exploited is critical.
- Asset value: Attackers look for assets with the highest value. For example, compromising a dev system that doesn’t have anything of value on it may provide a foothold but it isn’t going to be as interesting a target as compromising the domain controller or a company’s enterprise resource planning (ERP) system. Within the complex systems and environments with which businesses operate today, asset value is not always as simple as figuring out whether the system itself is running critical software. The roles and permissions granted to the users of that system can be equally important when we consider asset value. Determining asset value requires having a comprehensive view of identity data as well.
Vulnerability management starts with CVSS
While not its intended use case, the Common Vulnerability Scoring System (CVSS) has, in many organizations, become the de facto means for prioritizing vulnerability remediation. This is largely due to the lack of any other usable scoring standard within the industry. CVSS was never intended to be a mechanism for prioritizing remediation based on actual risk, but rather is simply a measure of the impact a vulnerability would have post exploitation.
The CVSS standard has evolved since its inception, with CVSSv3 being the current standard. CVSSv3 was published in 2015 with an aim at addressing some of the significant shortcomings of CVSSv2, the biggest of which was identifying vulnerabilities that, post exploitation, could result in the compromise of resources outside of the scope of the original application. CVSSv3.1 was published a few years later, but it primarily addressed guidance on analysis rather than actual scoring deficiencies. While these improvements were welcome, CVSSv3 is still best used as a measure of severity rather than a measure of risk.
The CVSS base metrics are made up of two components — the exploitability metrics and the impact metric. The exploitability metrics describe aspects of a vulnerability that may make it easier or harder to exploit, such as whether authentication is required or whether exploitation requires tricking someone into taking an action. The impact metrics describe the post-exploitation impact broken down into confidentiality, integrity, and availability.
CVSS temporal metrics, an extension of the CVSS base vector, take a tiny step in the direction of capturing risk by incorporating an exploit maturity metric, but even this falls significantly short as it is only a measure of the most mature exploit ever made available for that vulnerability. As a result, likelihood of exploitation and asset value are missing in most organization’s risk-based prioritization processes.
CVSS also provides an environmental metric, which enables an organization to adjust CVSS scores based on characteristics specific to its environment. The environmental metric can make CVSS more useful for prioritization, but is difficult to implement at scale and is rarely used.
Another core issue with using CVSS as a prioritization mechanism is that the scoring system results in far too many High and Critical vulnerabilities for any organization to successfully remediate.
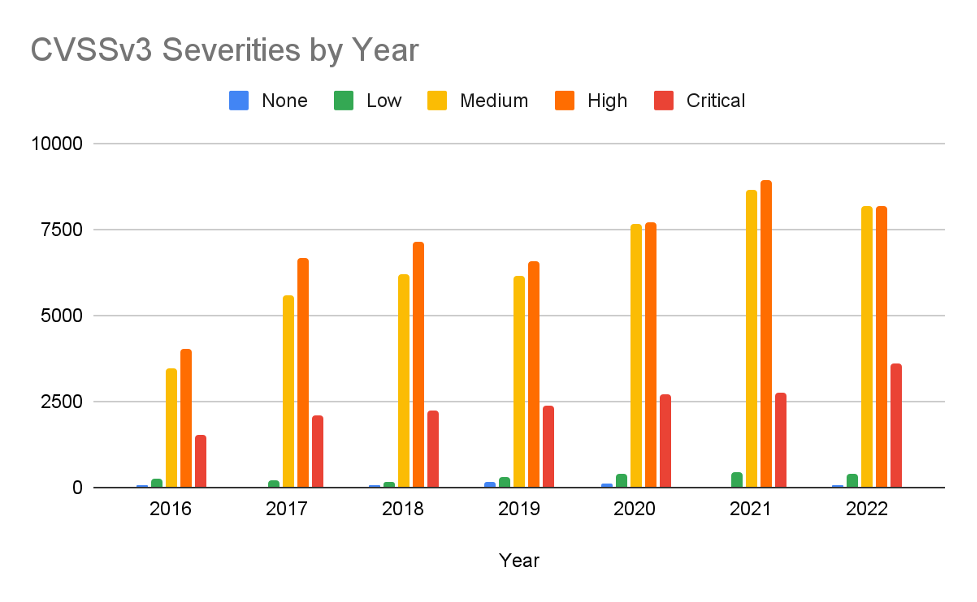
출처: Tenable Research, January 2023
In 2022 there were over 20,000 CVEs published to NVD with 40% of them getting a high severity and over 17% getting a critical severity. In other words, more than half of all published CVEs in 2022 would have required near-immediate attention by any organization that bases its remediation service level agreements (SLAs) on CVSSv3 ratings. That isn’t sustainable. The core limitation of CVSS is that it does not take into account the risk of exploitation. Based on observable data, Tenable Research has evidence of either proof of concept availability or actual exploitation in only 15% of all CVEs published. When we focus even further on vulnerabilities for which we have evidence that the vulnerability has been exploited in the wild, the percentage drops to around 3% of all CVEs.
How the cybersecurity industry is evolving vulnerability prioritization
We’ve seen an evolution in vulnerability management frameworks over the last couple of years, with several efforts aimed at delivering risk-informed prioritization by incorporating exploitation likelihood context. Below, we explore two core frameworks: Exploit Prediction Scoring System (EPSS) and Stakeholder-Specific Vulnerability Categorization (SSVC) .
EPSS
According to the Forum of Incident Response and Security Teams (FIRST), the Exploit Prediction Scoring System (EPSS) is “an open, data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild.” The goal of EPSS is to enable defenders to better prioritize vulnerability remediation by leveraging current threat information from real-world exploit data. The model produces a probability score between 0 and 1 that represents the likelihood that a vulnerability will be exploited.
EPSS is primarily focused on overcoming the fact that CVSS does not provide any measurement on exploitation risk. Unfortunately, EPSS does not provide any guidance on the impact of exploitation or the importance of the asset that is vulnerable, so on its own it is not sufficient for making well informed decisions around risk-informed prioritization.
SSVC
Stakeholder-Specific Vulnerability Categorization (SSVC) is a vulnerability analysis methodology developed by Carnegie Mellon Univeristy’s Software Engineering Institute in collaboration with the U.S. Cybersecurity and Infrastructure Security Agency (CISA). According to CISA, the core SSVC methodology looks at a vulnerability’s exploitation status, impacts to safety and prevalence of the affected product. Another important aspect of SSVC is that it is designed to be a customizable decision tree geared towards a company’s prioritization requirements.
CISA SSVC Guide
CISA recently published a guide based on its implementation of SSVC. The CISA SSVC decision tree looks at five values:
- Exploitation status: This determines the current state of exploitation of a vulnerability based on information available at the time of analysis.
- Technical impact: Technical impact is similar to the CVSS base score’s concept of severity.
- Automatable: Automatable represents the ease and speed with which an exploit can propagate.
- Mission prevalence: Mision prevalence represents how critical an application or asset is to an organization’s function. An important distinction from the original SSVC framework is that mission prevalence is not simply a count of affected instances.
- Public well-being impact: This looks at the impact of an affected system compromise on humans.
According to the CISA guide, prioritization uses these five values to reach one of four possible decisions:
- Track: The vulnerability does not require action at this time. The organization would continue to track the vulnerability and reassess it if new information becomes available. CISA recommends remediating Track vulnerabilities within standard update timelines.
- Track*: The vulnerability contains specific characteristics that may require closer monitoring for changes. CISA recommends remediating Track* vulnerabilities within standard update timelines.
- Attend: The vulnerability requires attention from the organization's internal, supervisory-level individuals. Necessary actions include requesting assistance or information about the vulnerability, and may involve publishing a notification either internally and/or externally. CISA recommends remediating Attend vulnerabilities sooner than standard update timelines.
- Act: The vulnerability requires attention from the organization's internal, supervisory-level and leadership-level individuals. Necessary actions include requesting assistance or information about the vulnerability, as well as publishing a notification either internally and/or externally. Typically, internal groups would meet to determine the overall response and then execute agreed upon actions. CISA recommends remediating Act vulnerabilities as soon as possible.
One glaring issue here is that the phrase “standard update timelines” is not well defined in the guide. If the intent is that “standard update timelines” are whatever existing SLAs an organization has, these are typically based on CVSS metrics and can be very tight for anything that is rated a Critical vulnerability. On the other end of the spectrum, if the phrase is treated as “whenever the business would usually get around to patching the software” this could create a lack of clarity on priority or a growing list of vulnerabilities that will never be patched.
SSVC is designed to deliver on all of the foundational elements — impact, likelihood of exploitation and mission criticality for the asset. Additionally, SSVC by design, is customizable so organizations can tweak the decision tree to fit their needs. While SSVC is a significant step forward as a useful framework for risk based prioritization, many organizations will face barriers, some of them significant, in operationalizing the framework. Gaining access to reliable and accurate threat intelligence, having a strong understanding of asset context for all assets, including identity and cloud, and developing a system for performing the analysis and prioritization at scale require a high degree of maturity and significant investment.
Risk-informed prioritization with Tenable
Since 2018, Tenable has provided a number of capabilities that deliver on the concept of risk-informed prioritization. We have vulnerability and asset scores that not only deliver on the foundational measurements of vulnerability impact, likelihood of exploitation, and asset criticality but do so in a scalable way without requiring customers to maintain complex data tracking systems. Additionally, we have several reports and dashboards that bring focus to the most effective actions that customers can take to reduce risk across their assets. These capabilities, which are incorporated into the Tenable One Exposure Management Platform, include:
Vulnerability priority rating
Tenable’s vulnerability priority rating (VPR) can help users prioritize vulnerability remediation by assigning a rating based on two core components: technical impact and threat. VPR uses the CVSSv3 impact subscore to measure the technical impact on confidentiality, integrity and availability following exploitation of a vulnerability. Added to the technical impact is a threat component that reflects both recent and potential future threat activity against a vulnerability. This is critical, as it means that the risk associated with a vulnerability will evolve as the threat landscape evolves, ensuring that companies focus on the most important vulnerabilities of today rather than on an ever-growing list of vulnerabilities that have been exploited in the past.
자산 중요도 등급
Tenable’s asset criticality rating (ACR) represents an asset’s relative risk as an integer from 1 to 10, with a higher ACR value indicating greater risk. ACR is reflective of an asset’s risk based on measurements such as location on your network and proximity to the internet, device type and device capabilities. ACR can help users ensure that those devices which are likely to have the highest impact on business function are prioritized for remediation.
Recommended actions
Tenable’s recommended actions capability identifies the set of remediations a user can apply in order to have the greatest impact on reducing cyber risk with the smallest number ofactions. This aggregates findings based on supersedence chains to show the top level patch, rather than a series of patches, to apply for a given product, and then calculates risk reduction against the aggregated vulnerability risk ratings and asset criticality. Taking these actions helps companies recognize risk-informed prioritization at larger scales without having to perform significant manual analysis of a wide range of vulnerabilities and assets.
공격 경로 분석
Going beyond the core fundamentals of understanding vulnerability risk and asset criticality, a new capability in Tenable One, Attack Path Analysis, allows users to better understand the attack paths that are present within their infrastructure. Users can further focus their prioritization efforts on the vulnerabilities that exist within a critical chain that would be of particular interest for an attacker. These attack paths are likely avenues that an attacker would leverage to gain access to a company’s most critical resources in a real world attack and, thus, are critical to prioritize for remediation.
Bringing it all together
Customers can leverage this data in a number of different ways depending on the Tenable products they are using.
Tenable One
Tenable One customers are able to leverage our full suite of tools, including Tenable.io, Tenable.cs, Tenable.ad and Attack Path Analysis to get a complete picture of their environment, going beyond just traditional vulnerability management assets. The asset overview feature in Tenable One allows users to see all of their assets and their associated Asset Exposure Score — a score that combines both VPR and ACR to create a risk score for a given asset (see example below).
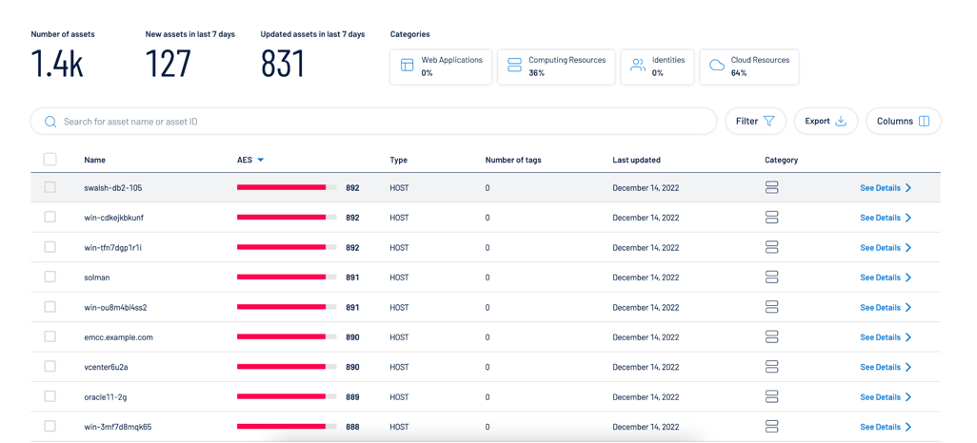
출처: Tenable Research, January 2023
As discussed previously, the recommended actions view enables organizations to identify a set of actions that will maximize risk reduction (see example below).
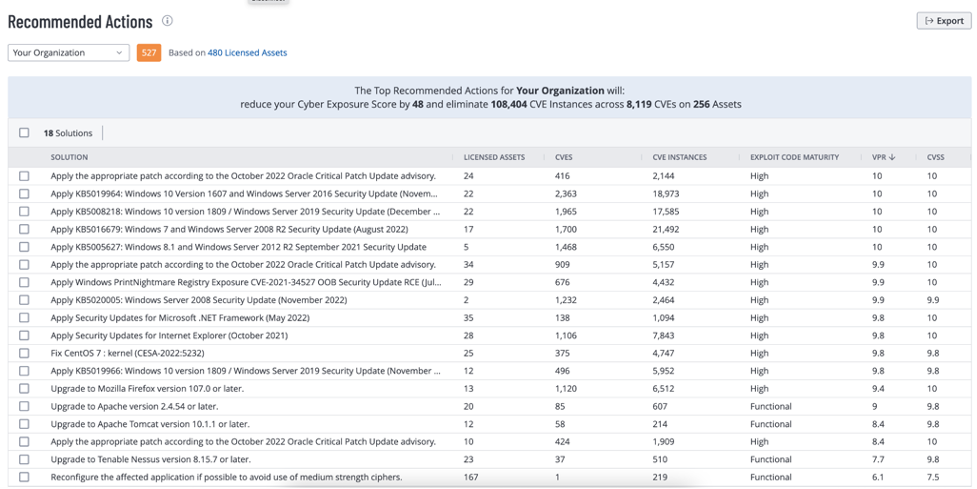
출처: Tenable Research, January 2023
Tenable.sc provides an ACR summary dashboard (https://www.tenable.com/sc-dashboards/acr-summary) which includes a component ACR Summary - Highlighted Patches (VPR and ACR 7-10). These are going to be the assets and vulnerabilities that have high risk of exploitation, high technical impact, and represent an asset that is a high risk.
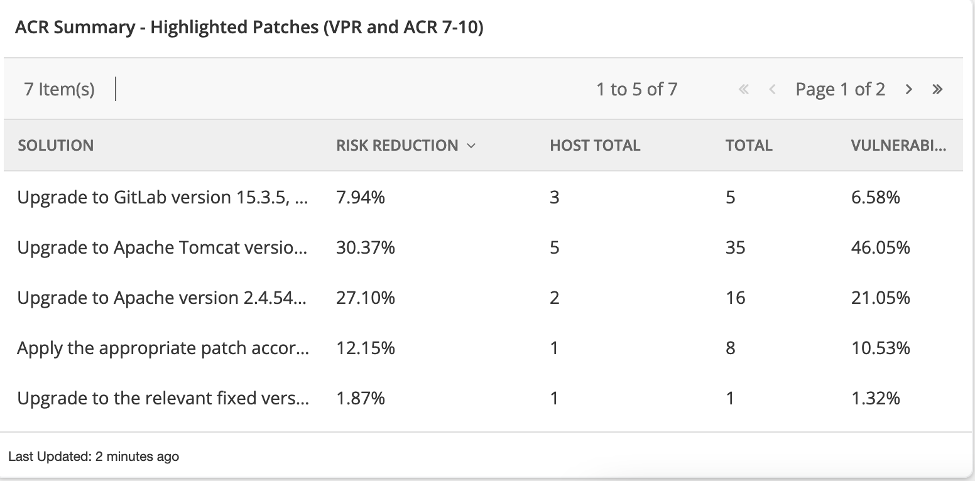
출처: Tenable Research, January 2023
Tenable.sc and Tenable Lumin
Tenable.sc and Tenable Lumin customers can also leverage the solutions and recommended actions views, respectively, to determine the fixes they can apply that will achieve the highest risk reduction in the most efficient manner possible. These views enable risk reduction that takes into account the number of hosts affected, the number of vulnerabilities that would be remediated and the highest VPR score for the vulnerabilities that would be remediated.
Takeaway
Developing an exposure management program requires taking a risk-informed approach to vulnerability remediation that goes well beyond CVSS metrics. No one solution is right for every organization. While we have seen positive steps in industry frameworks over the last couple of years, there are still a number of hurdles to overcome. Whether you’re ready to kick off an exposure management program or are simply looking to embrace a more risk-informed approach to vulnerability remediation, Tenable has several solutions that provide mature and scalable capabilities.
자세히 알아보기
- Read the blog: Tenable One - 노출 관리 플랫폼 소개
- Download the white paper: 사이버 보안 조직이 직면한 3가지 실제 과제: How Exposure Management Can Help
- View the on-demand webinar: Tenable ONE - 노출 관리 플랫폼 소개: Now You Can Anticipate Likely Attacks and Proactively Reduce Cyber Risk
- Exposure Management
- Risk-based Vulnerability Management
- Security Frameworks
- Vulnerability Management



