Secure Kubernetes and containers
Protect Kubernetes and container environments against threats with powerful KSPM capabilities that ensure proper configurations and right-sized policies.
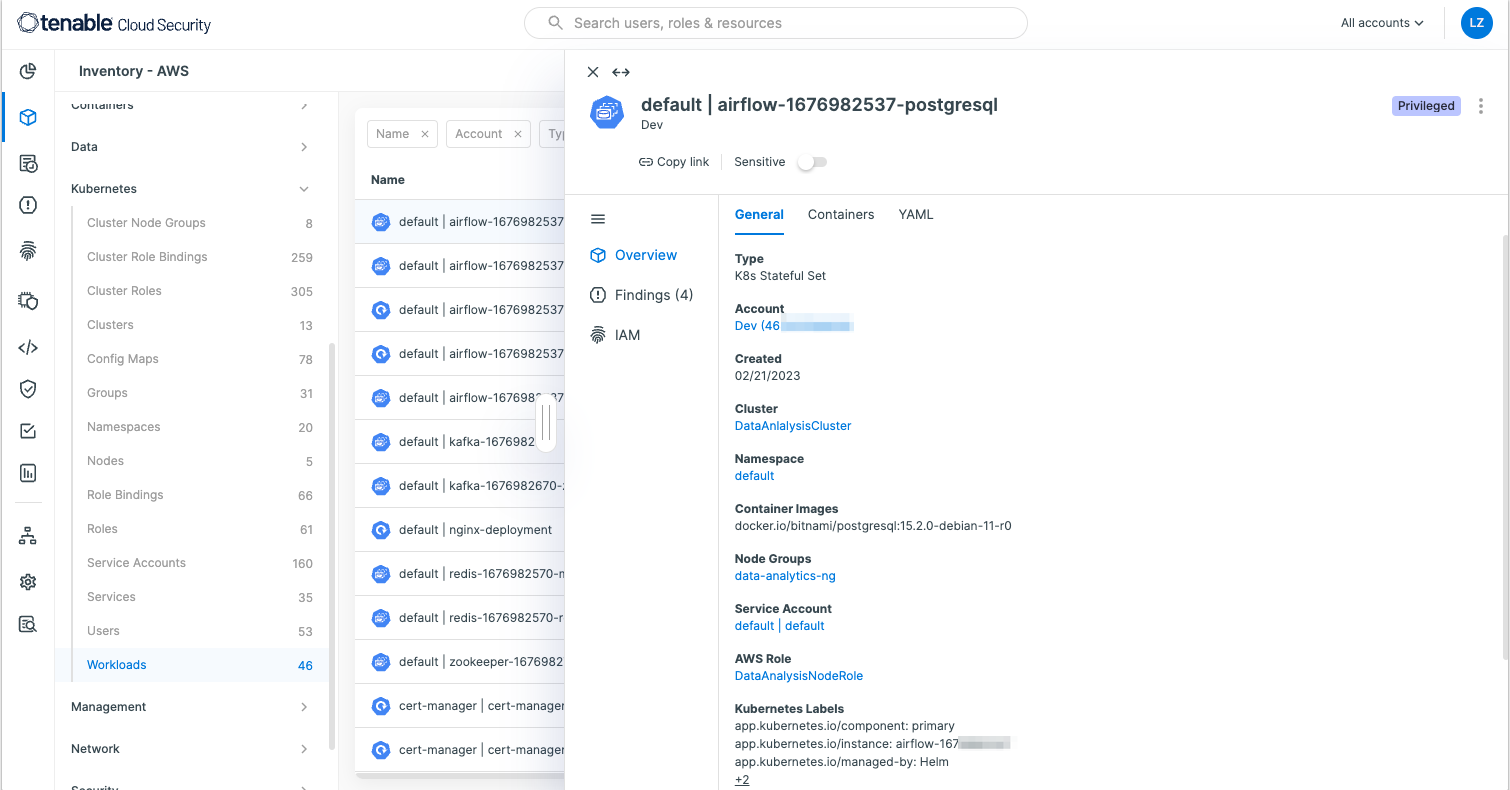
See inside Kubernetes clusters and scan container images
Overcome Kubernetes chaos and effectively govern with visibility into running clusters and ongoing security policy validation.
Secure human and machine identities within Kubernetes
Generate fine-grained least privilege policies for remediation
Validate Kubernetes configurations in minutes
Simplify and automate Kubernetes and container security
Scale visibility across public cloud and on–premises Kubernetes deployments
Protect Kubernetes clusters running on–premises, in private networks, as well as both managed and self–managed clusters with comprehensive visibility and reporting at scale. Unlock full visibility to resources in a cluster, including workloads, users, role bindings, namespaces and more.
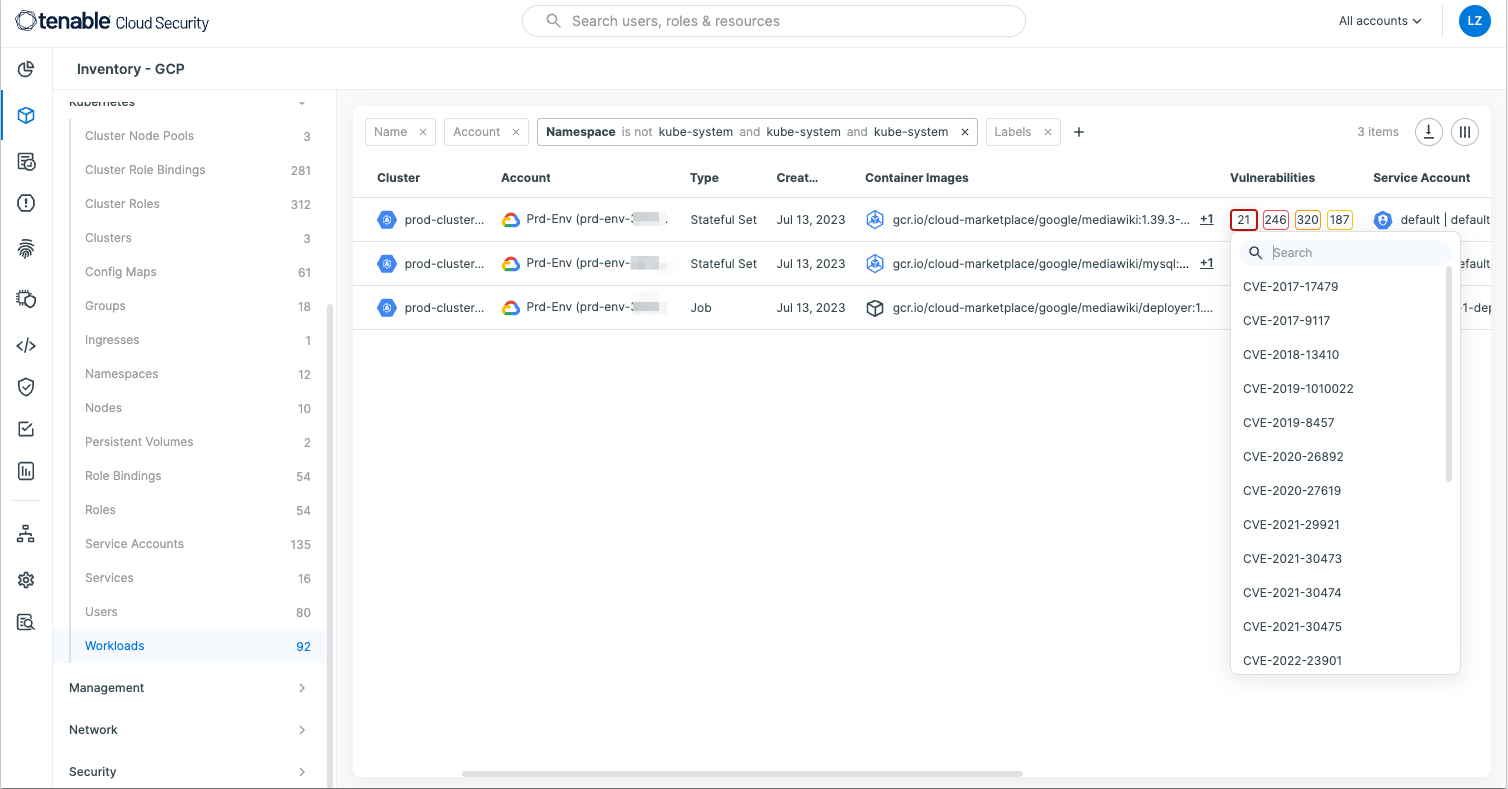
Detect container vulnerabilities and malware
Eliminate the need for multiple security tools by detecting vulnerabilities and malware in container images and viewing the findings and risks as part of the Kubernetes inventory all in the same user interface. Using the solution. 가능한 작업:
- Detect images deployed to running containers
- Scan images in registries before they are deployed
- Allow DevSecOps teams to trigger a scan of an image from the CI/CD pipeline, bringing “shift left” to vulnerability management of containers
Automate Kubernetes Compliance Audits and Reports
Simplify how you maintain the integrity and adherence to regulations of Kubernetes deployments with automated mapping to industry standards and regulatory frameworks. Get multi-cloud support across multiple frameworks, including CIS, GDPR, NIST, and PCI-DSS and custom policies. Conduct thorough audits, identify compliance violations early and generate detailed reports for internal and external stakeholders.
Detect and prioritize risk in context
Optimize your response strategies with Tenable's ability to prioritize findings contextually. Tenable Cloud Security delivers a full-stack risk analysis for Kubernetes workloads, identifying and prioritizing risks with context so you can:
- Detect container vulnerabilities deployed on Kubernetes clusters by using workload image scanning
- Detect misconfigurations defined in Kubernetes manifests by using integrated infrastructure as code (IaC) scanning
Use guided remediation to reduce risk faster
Get automated and guided remediation of misconfigurations, policy violations and risky privileges within clusters and for your full cloud environment.
Capabilities incluce:
- Use of wizards
- Pre-populated policies
- Configuration fixes
Tenable Cloud Security speeds up the mitigation process and provides secure role-based access control (RBAC) within Kubernetes, to safeguard internal roles, cluster roles and identities.
Cloud Security for enhanced Kubernetes
and container protection
Tenable Cloud Security에 대해 자세히 알아보기
[Tenable Cloud Security] 자동화를 사용하여 저희는 과도한 수동 프로세스를 없애고 2명 또는 3명의 보안 팀원이 몇 달이 걸릴 수 있는 작업을 몇 분만에 수행합니다.
- Tenable Cloud Security