클라우드 구성 오류를 식별 및 수정
Identify and fix misconfigurations with ease. Cloud misconfigurations, like open storage buckets, overly permissive roles or insecure network settings, are a leading cause of breaches, compliance failures and data loss. Use Tenable Cloud Security to continuously detect and prioritize these risks through infrastructure as code (IaC) scanning, and across runtime and identity layers.
Go beyond alerts with automated cloud security
Expose storage buckets, grant overly permissive roles, and configure networks insecurely.
Achieve end-to-end cloud-native security
Secure your entire application lifecycle by preventing misconfigurations in code, enforcing policies at runtime and automating remediation with full risk context.
Continuously detect misconfigurations
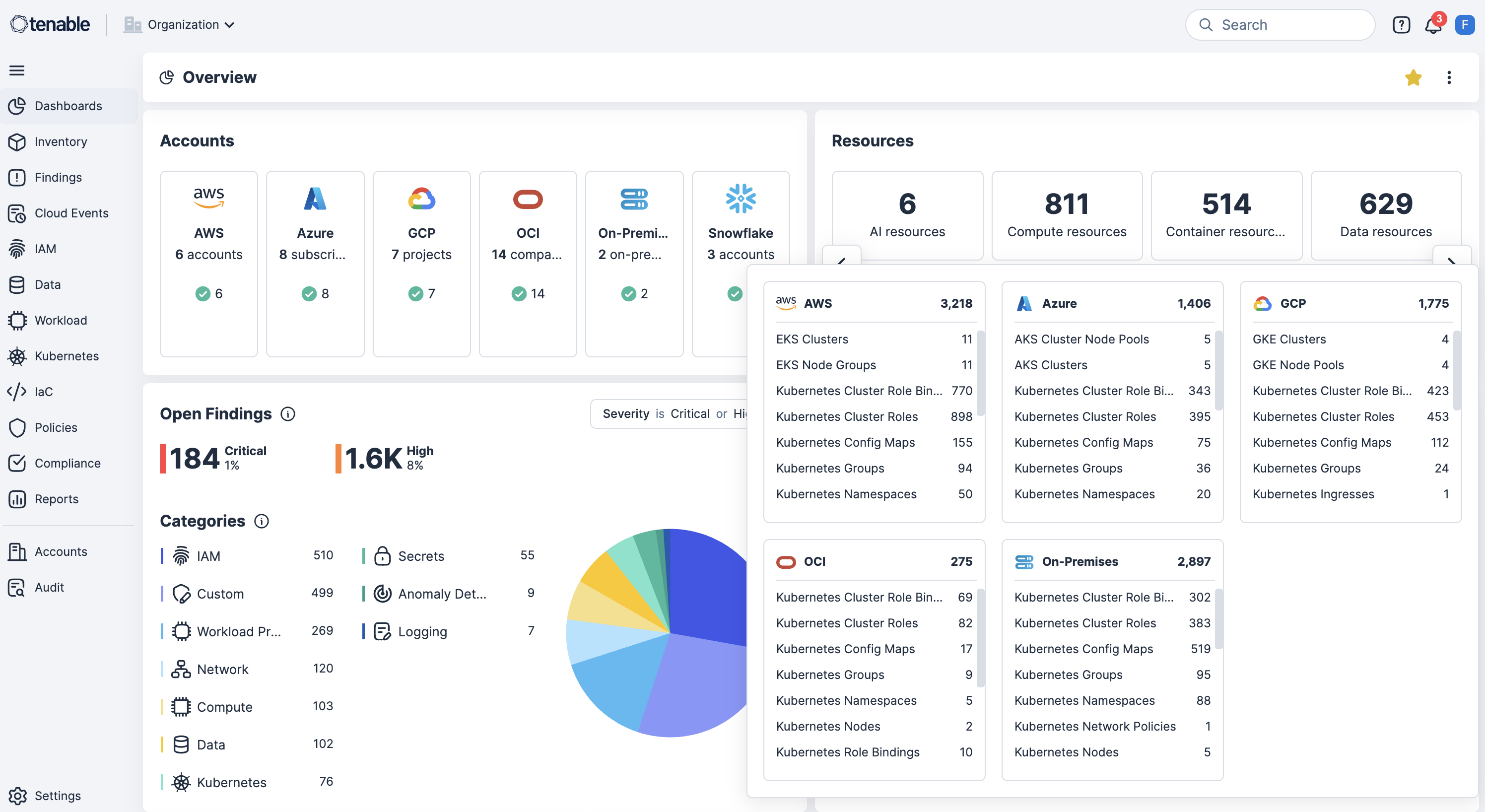
Continuously scan AWS, Azure, OCI, GCP, OCI and Kubernetes for misconfigurations, policy violations and publicly exposed resources to surface risks in real time.
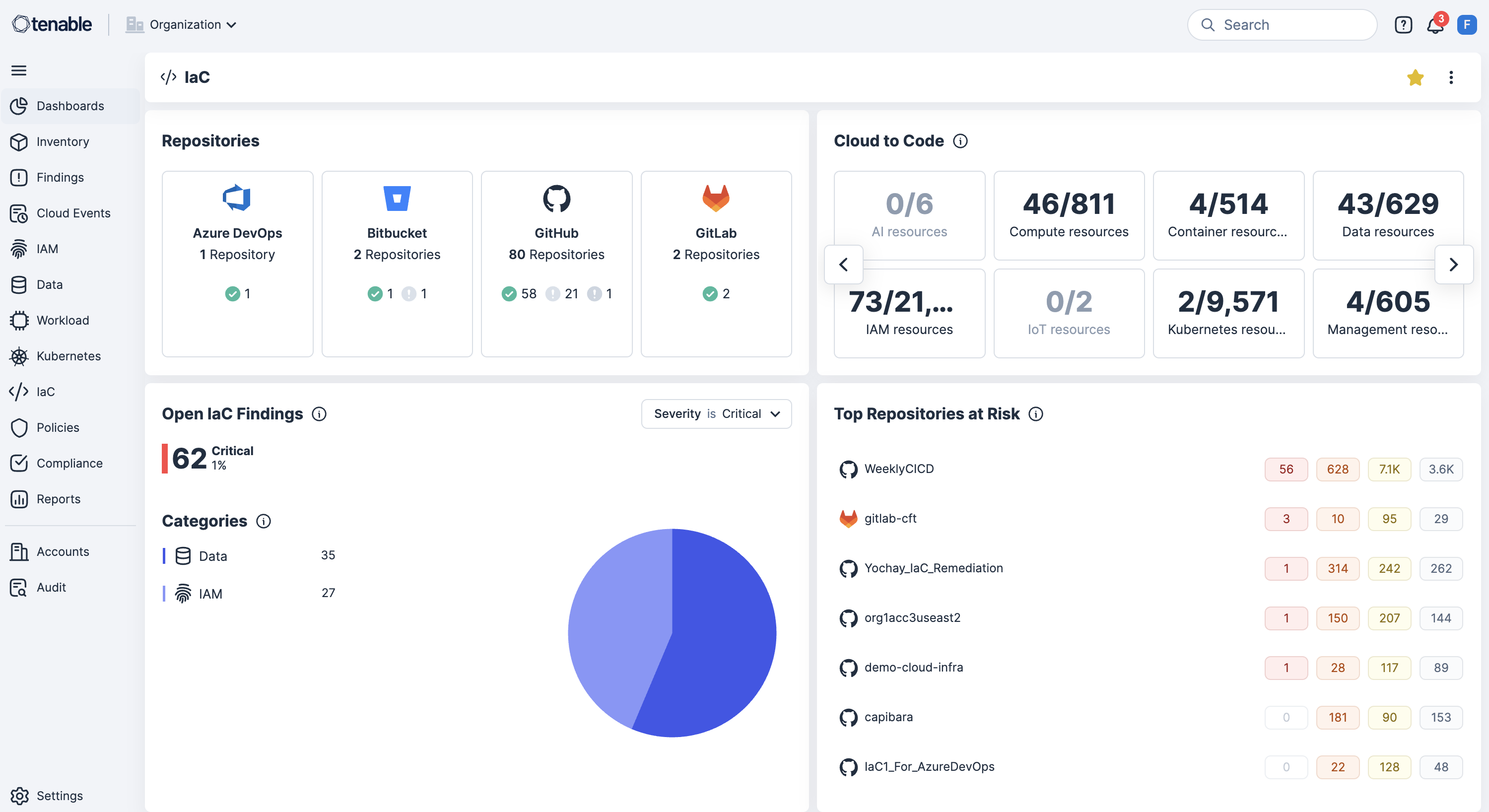
Shift left with IaC scanning in CI/CD pipelines
Integrate IaC scanning and CI/CD pipeline tools to detect misconfigurations before deployment to reduce rework and prevent security drift.
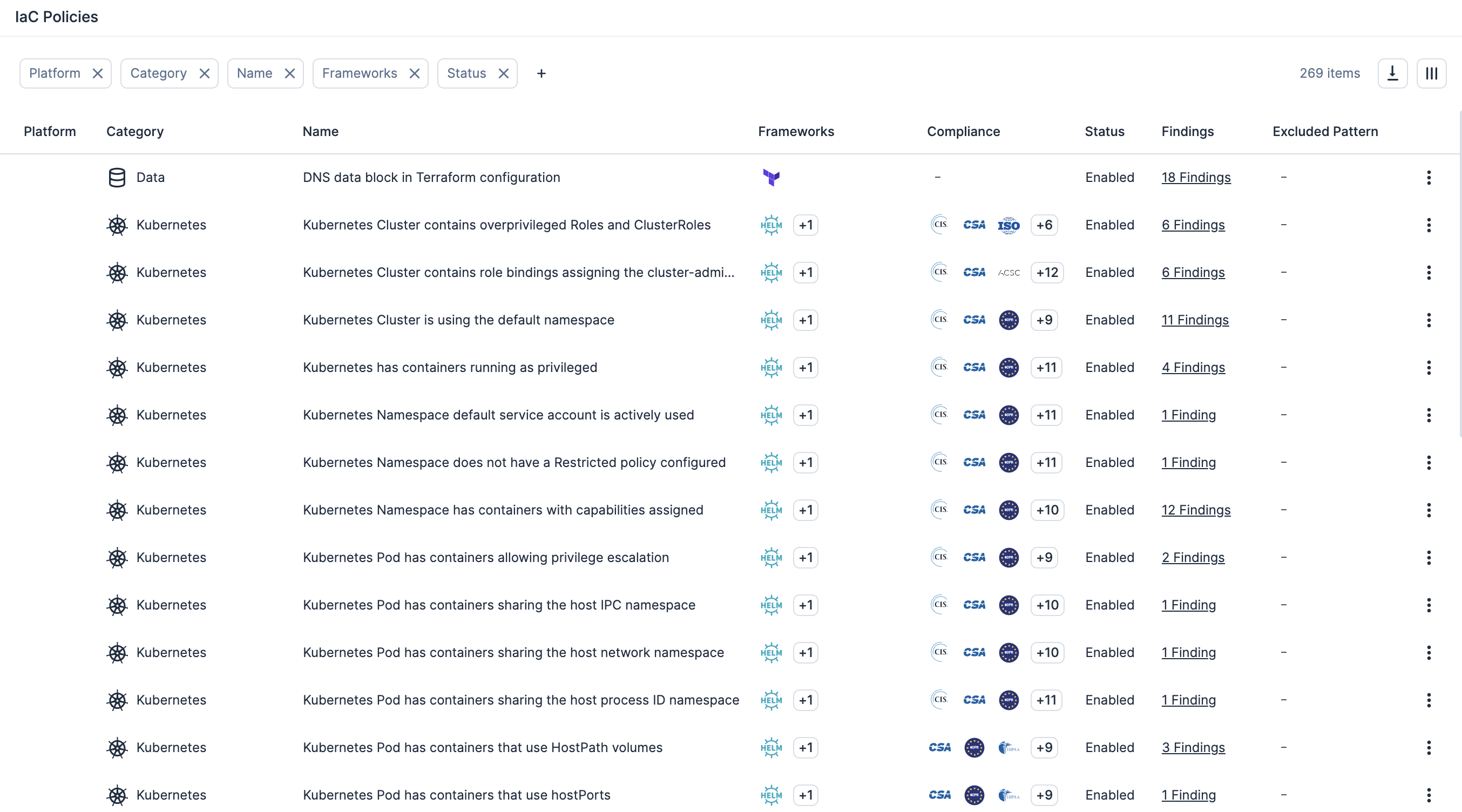
Enforce security guardrails at Kubernetes deployment
Enforce security guardrails at the cluster level by blocking misconfigured workloads at deployment time to build in compliance and security from the start.
Use custom policies with automated response
Enable custom policy definition to detect excessive permissions or risky configurations on resources, then automatically trigger remediation workflows.
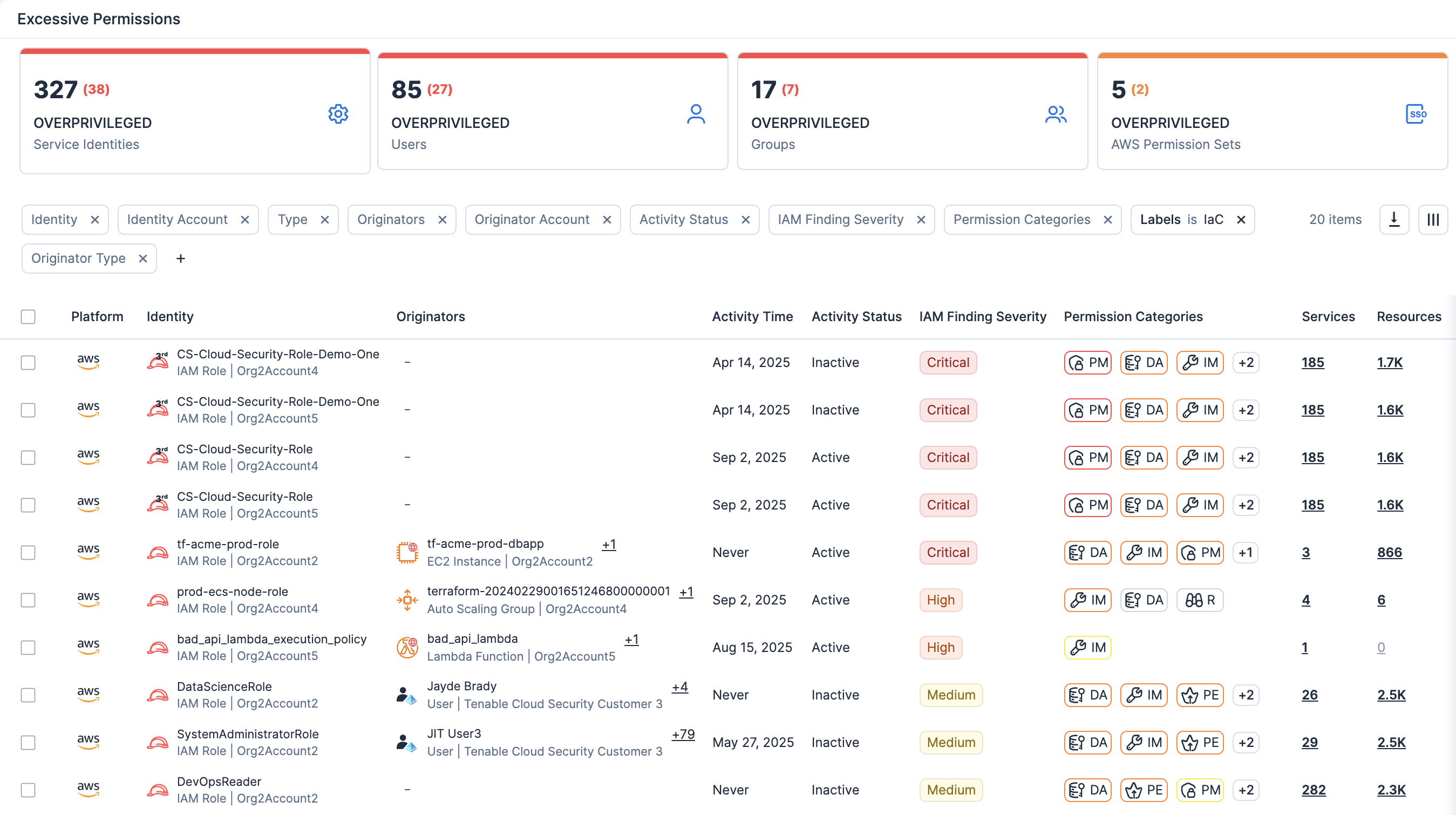
See contextual risk correlation with identity-aware remediation
Correlate misconfigurations with vulnerabilities, excessive permissions and sensitive data exposure, while mapping identities with cloud infrastructure entitlement management (CIEM) to enforce least privilege and accelerate remediation.
Tenable Cloud Security에 대해 자세히 알아보기
[Tenable Cloud Security] 자동화를 사용하여 저희는 과도한 수동 프로세스를 없애고 2명 또는 3명의 보안 팀원이 몇 달이 걸릴 수 있는 작업을 몇 분만에 수행합니다.
- Tenable Cloud Security