Enforce least privilege across cloud. Right-size permissions at scale.
Reduce excessive standing privileges, the silent enablers of data loss and lateral movement, and enable continuous least-privilege enforcement with Tenable Cloud Security. Analyze access patterns, flag overprivileged roles and automate just-in-time access without slowing developer velocity.
Ensure security follows the identity lifecycle
Moving from persistent access to just-in-time permissions.
Manage identity governance with Tenable Cloud Security
Reduce excessive cloud permissions, a top enabler of breaches and audit failures. Shrink identity blast radius, with visibility, automation and policy enforcement that aligns with least privilege best practices.
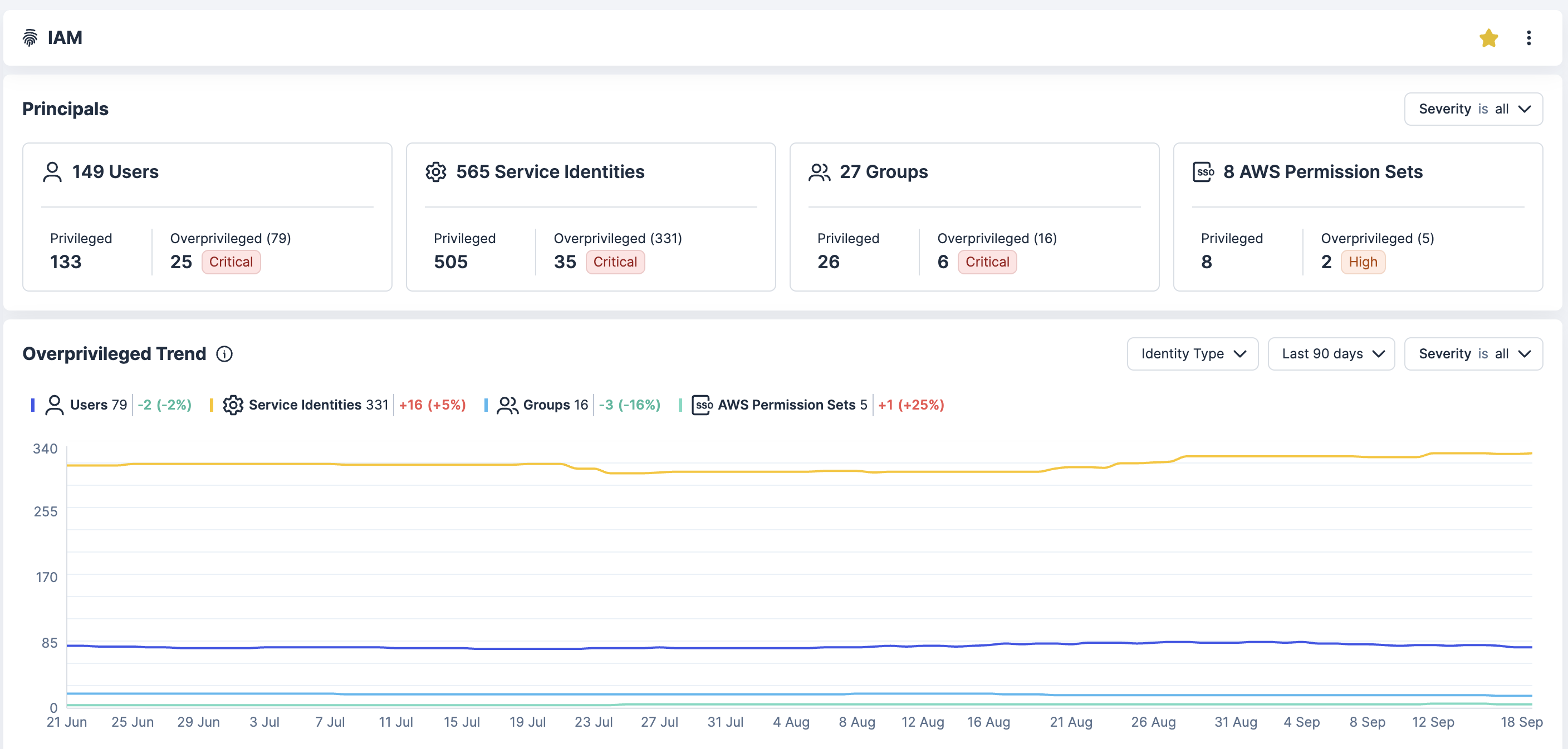
Discover identities and entitlements
Gain full visibility into all identities across AWS, Azure, GCP, and Kubernetes, including human users, service accounts and third-party integrations. Detect orphaned accounts, unused roles and excessive entitlements
Analyze privilege risk
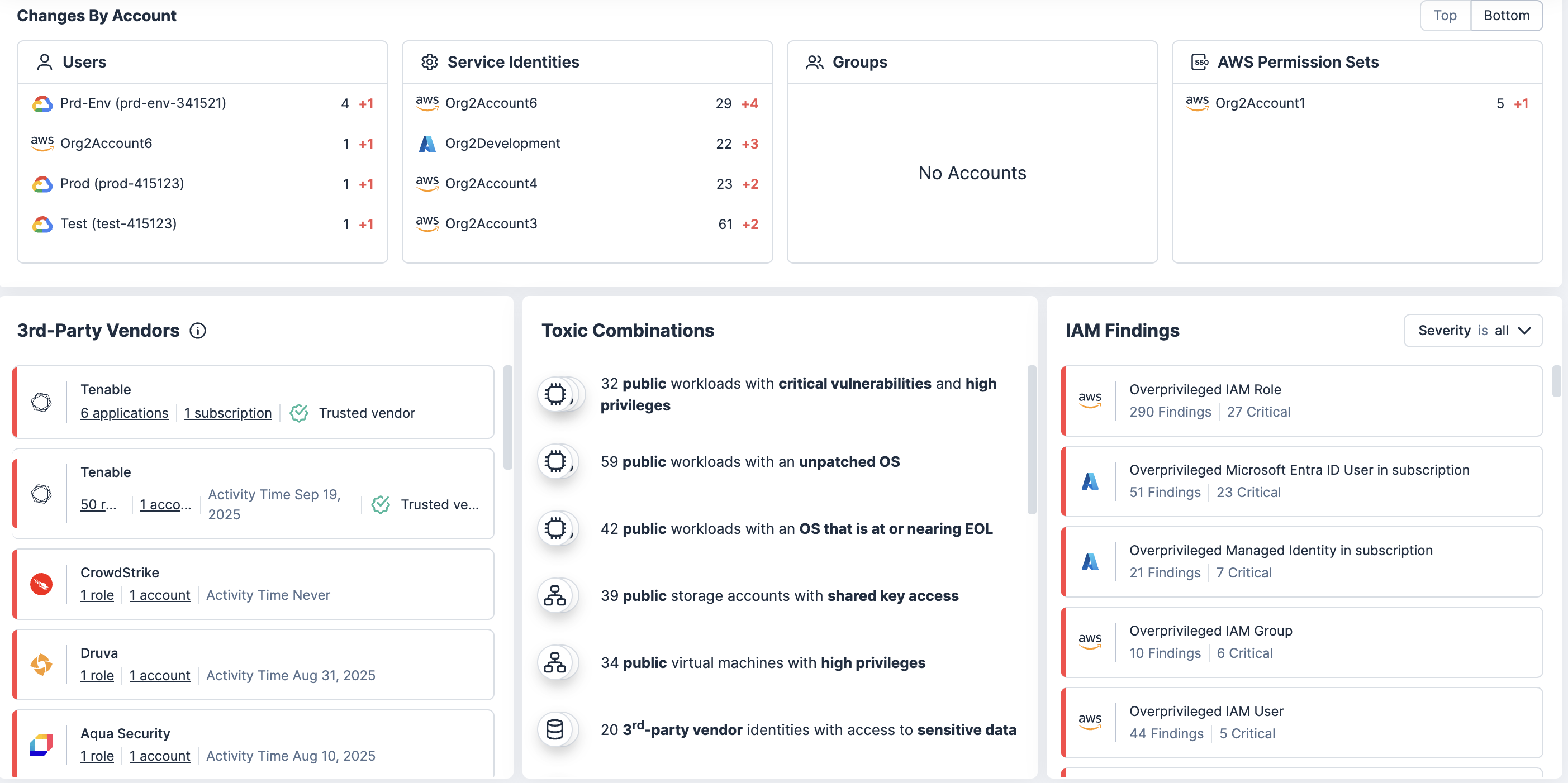
Analyze policies, group memberships and role assumptions to uncover privilege escalation risks and lateral movement opportunities. This context helps your teams eliminate high-risk paths.
Get contextual correlation and prioritization
Correlate excessive permissions with vulnerabilities, misconfigurations and sensitive data to see where privilege misuse could have the greatest impact.
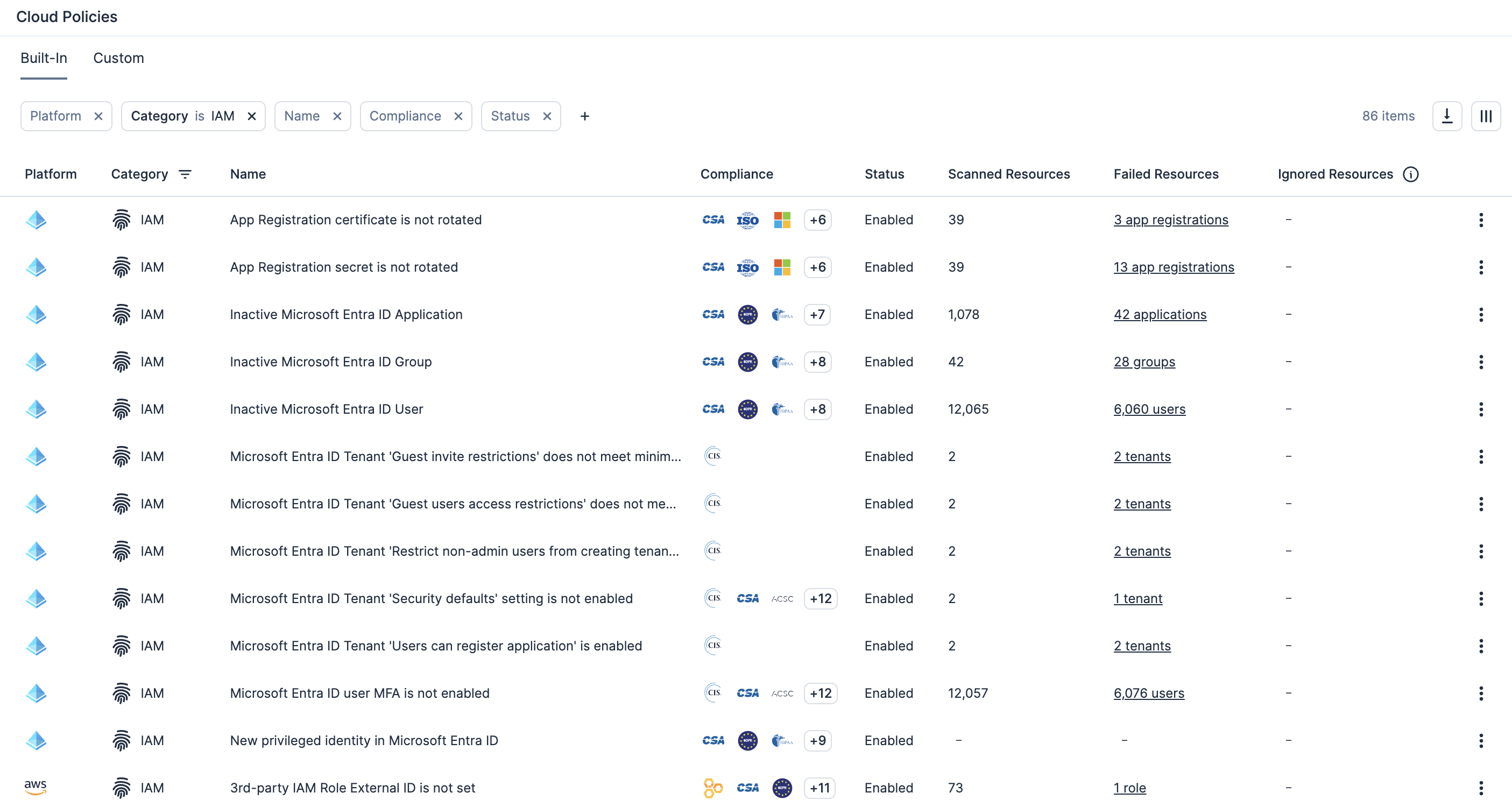
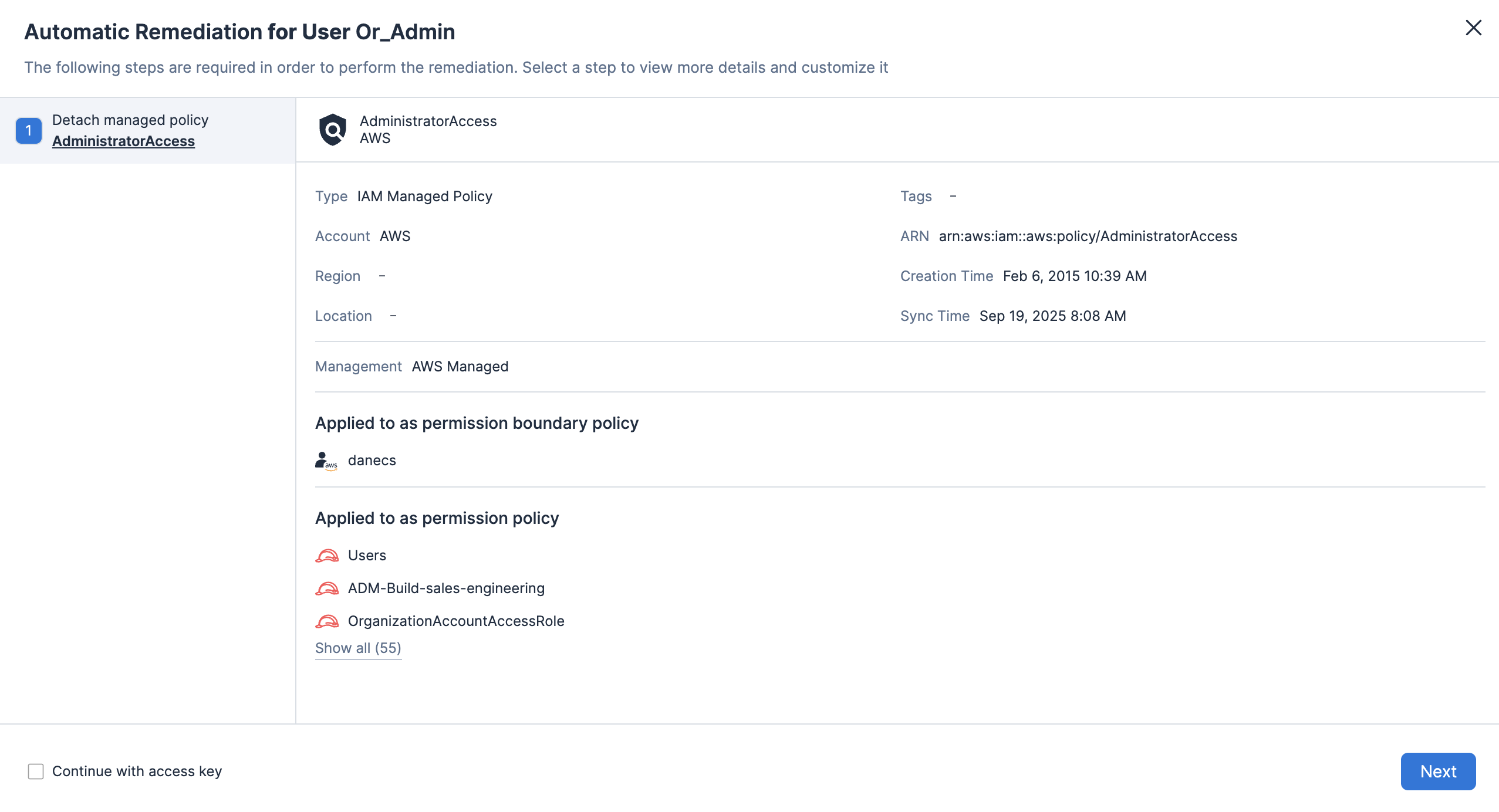
Enforce custom policies and automated remediation
Enable custom policy definition to detect excessive permissions or risky configurations on resources, then automatically trigger remediation workflows.
Integrate CIEM with Tenable One
Continuously enforce least privilege with cloud infrastructure entitlements management (CIEM) to ensure permissions are just enough, just in time and never excessive.
Tenable Cloud Security에 대해 자세히 알아보기
[Tenable Cloud Security] 자동화를 사용하여 저희는 과도한 수동 프로세스를 없애고 2명 또는 3명의 보안 팀원이 몇 달이 걸릴 수 있는 작업을 몇 분만에 수행합니다.
- Tenable Cloud Security