by David Schwalenberg
May 18, 2016
The Verizon Data Breach Investigation Report (DBIR), first published in 2008, is an annual publication that analyzes information security incidents from public and private organizations, with a focus on data breaches. Data breaches continue to have a major financial impact on organizations, as well as an impact on their reputations. Tenable Network Security offers dashboards that can assist organizations in meeting many of the recommendations and best practices in the DBIR.
The 2015 DBIR notes that as in previous years, a vast majority of all attacks fall into a few basic patterns. Looking back to the 2014 DBIR for each of these patterns, best practices are noted that can assist in thwarting the attacks. Some of the best practices can assist in thwarting multiple attack patterns. The Crimeware and Cyber-Espionage patterns mention the best practice of patching and correctly configuring web browsers.
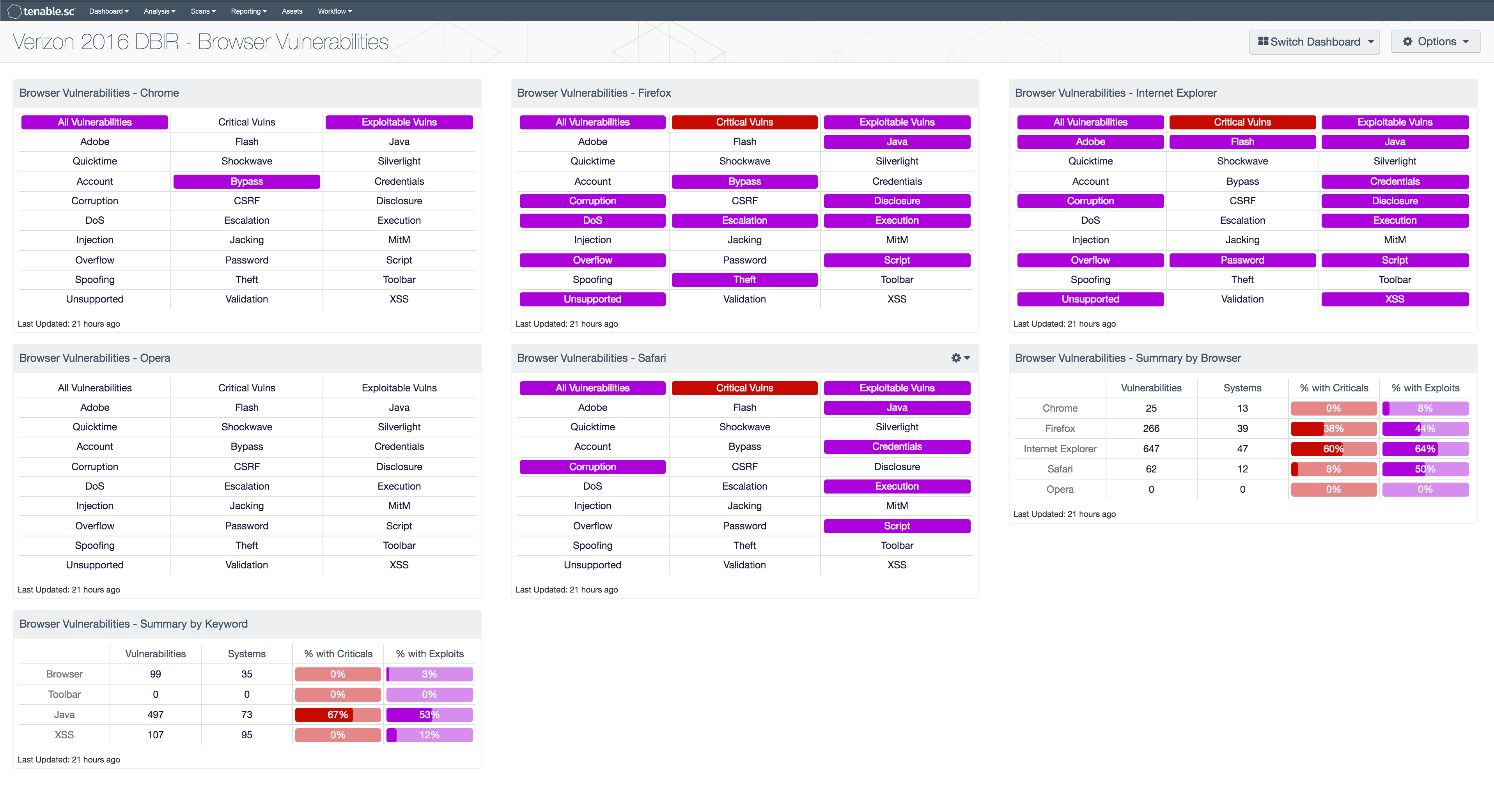
Vulnerable web browsers can pose a great security risk to the network. Since web browsers interact through the Internet with the outside world, they are often targeted by outside attackers. The use of unauthorized and vulnerable web browsers may allow the network to be compromised. This dashboard displays actively and passively detected vulnerability information for the major web browsers: Chrome, Firefox, Internet Explorer, Safari, and Opera. This information can assist the organization as it seeks to reduce its chances of a data breach by eliminating unauthorized web browsers (e.g. from critical servers and point-of-sale systems), patching browser vulnerabilities, and disabling vulnerable plugins (e.g. Java).
For each browser, a matrix displays warning indicators for detected vulnerabilities. On the top row, the "All Vulnerabilities" indicator turns purple if any vulnerabilities at any severity level related to the browser are detected. This will indicate whether the browser is being used on the network and the vulnerabilities present. Informational detections are included, such as detections of Java enabled in the browser. The "Critical Vulns" indicator turns red if any Critical severity vulnerabilities are detected and the "Exploitable Vulns" indicator turns purple if any vulnerabilities that are known to be exploitable are detected. These critical and exploitable vulnerabilities are the highest priority to remediate.
The next two rows in each browser matrix contain indicators for vulnerabilities in certain products used in conjunction with web browsers, such as Adobe, Flash, and Java. The indicators turn purple if any vulnerabilities at any severity level (including Informational) are detected. This will indicate whether these products are being used and the vulnerabilities present.
The remaining rows in each browser matrix contain indicators based on keywords present in detected vulnerabilities related to the browser. Here, vulnerabilities at all severity levels except Informational are included. The keywords cover the major web browser threats, such as memory corruption, information disclosure, remote code execution, buffer overflows, cross-site scripting (XSS), and more. A purple indicator means that one or more vulnerabilities contain the keyword. Indicators can be removed or new indicators added as desired.
Clicking on a highlighted indicator in a matrix will bring up the vulnerability analysis screen to display details on the vulnerabilities. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 6.3.4
- PVS 4.2.0
- LCE 4.4.1
Tenable.sc Continuous View (Tenable.sc CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with the Nessus Network Monitor (NNM), as well as log correlation with the Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best protect its network from data breaches.
Listed below are the included components:
- Browser Vulnerabilities - Chrome - This matrix displays warning indicators for vulnerabilities actively and passively detected on the network related to the Google Chrome web browser.
- Browser Vulnerabilities - Firefox - This matrix displays warning indicators for vulnerabilities actively and passively detected on the network related to the Mozilla Firefox web browser.
- Browser Vulnerabilities - Internet Explorer - This matrix displays warning indicators for vulnerabilities actively and passively detected on the network related to the Microsoft Internet Explorer web browser.
- Browser Vulnerabilities - Safari - This matrix displays warning indicators for vulnerabilities actively and passively detected on the network related to the Apple Safari web browser.
- Browser Vulnerabilities - Opera - This matrix displays warning indicators for vulnerabilities actively and passively detected on the network related to the Opera web browser.
- Browser Vulnerabilities - Summary by Browser - This matrix displays summary information by major web browser for vulnerabilities actively and passively detected on the network. (Rows for additional web browsers can be added as desired.) The total count of vulnerabilities is displayed, indicating whether the browser is being used on the network and the vulnerabilities present. The count of vulnerable systems and the percentages of those systems with critical and exploitable vulnerabilities are also displayed. These critical and exploitable vulnerabilities are the highest priority to remediate. Clicking on an indicator will bring up the vulnerability analysis screen to display details on the vulnerabilities. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present.
- Browser Vulnerabilities - Summary by Keyword - This matrix displays summary information by keyword for vulnerabilities actively and passively detected on the network. (Rows for additional keywords can be added as desired.) The total count of vulnerabilities containing the keyword is displayed, along with the count of vulnerable systems and the percentages of those systems with critical and exploitable vulnerabilities. These critical and exploitable vulnerabilities are the highest priority to remediate. Clicking on an indicator will bring up the vulnerability analysis screen to display details on the vulnerabilities. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present.