by Andrew Freeborn
November 11, 2015
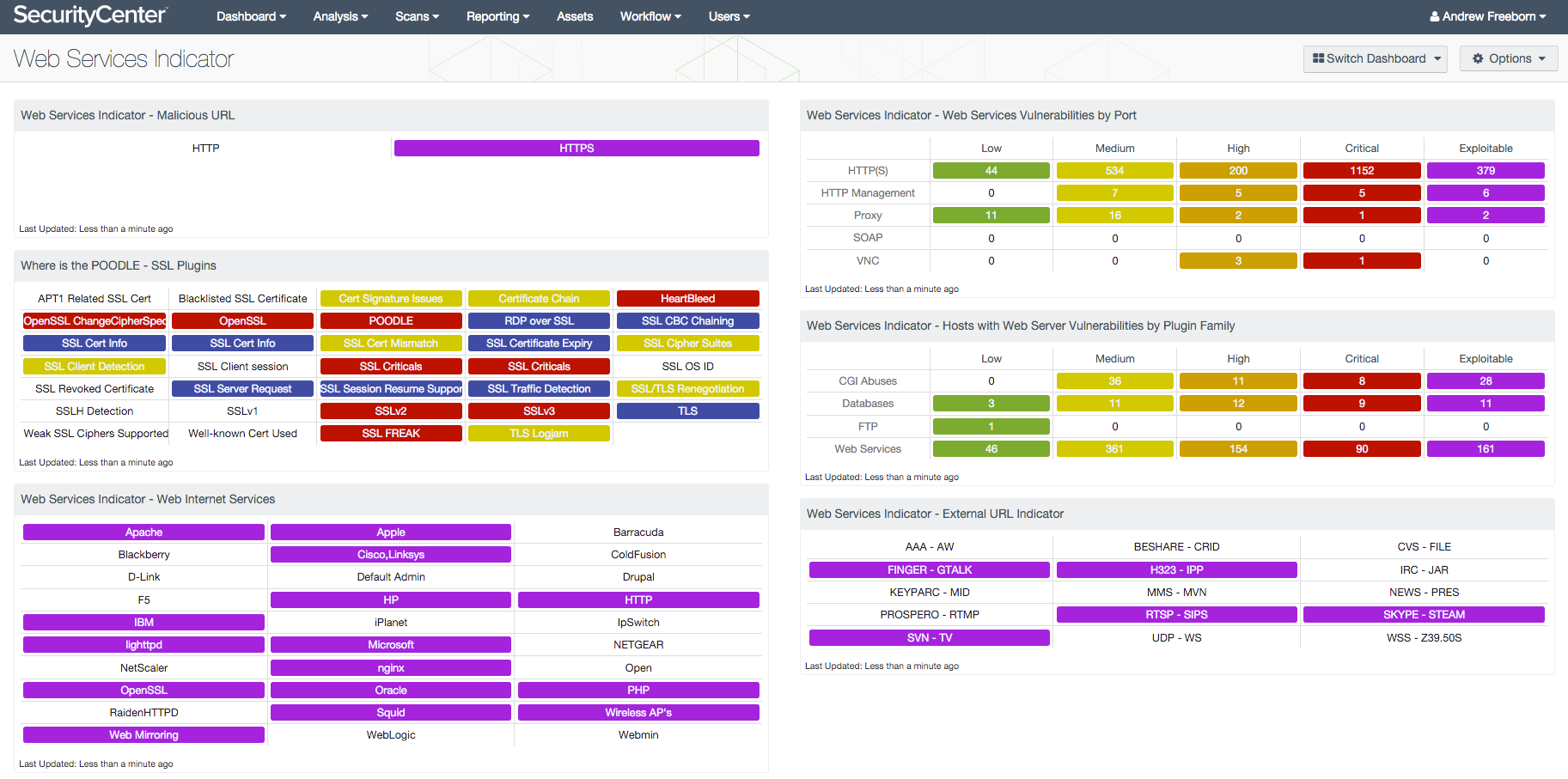
Services across enterprises are increasingly becoming web connected, but not all web services are secure. Organizations need to know what web services are operating in the environment in order to understand their vulnerability status. This dashboard provides insight into the web services in the environment and the vulnerabilities associated with them.
Administrators and analysts can better assess and defend the organization when they have the necessary information. This dashboard provides information based around web services in the environment. Web services and the technology that hosts them are supported and implemented in various ways. The vulnerabilities of web services, web service platforms, and related technologies are displayed in ways that are easy to understand. Analysts can see vulnerabilities based on ports, web service activities leaving the organization, and web services that are present with known vulnerabilities. Network defenders can use the insight into the vulnerabilities in web services provided by this dashboard to more effectively secure their network.
Web services introduce a complexity into the environment that sometimes translates into hoping that the web services can stay up with minimal supervision. Many times, those web services need to offer a secure communication channel. Technologies such as Apache and Microsoft IIS rely upon separate secure channel communication technologies, such as SSL, to implement those technologies in a secure fashion. Administrators and analysts can use this dashboard to gain a security-focused insight into the secure technologies that help protect web services.
Risks to the environment can come from software vulnerabilities in web services. If an attacker has a presence in the environment, they may try to exfiltrate data out of the environment by exploiting vulnerabilities associated with web services. Atypical or anomalous network traffic destined for external web services such as cloud-based file hosting services or even malicious websites may be an indication of network compromise. Administrators and analysts can monitor network traffic towards external web services and detect unexpected activity with this dashboard. Outbound network traffic connecting to external web services is displayed, along with details about the specific web services being used. This dashboard provides analysts with actionable information about external web services and can help reduce the time between detection and resolution.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 4.8.2
- Nessus 6.4.3
- PVS 4.4.0
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk and ensure compliance. Our family of products includes SecurityCenter Continuous View (CV), Nessus, and Passive Vulnerability Scanner (PVS). SecurityCenter CV provides the most comprehensive and integrated view of network health. Nessus is the global standard in detecting and assessing network data. PVS provides deep packet inspection to continuously discover and track users, applications, cloud infrastructures, trust relationships, and vulnerabilities.
This dashboard contains the following components:
- Malicious URL: The “Malicious URL” matrix component shows whether or not HTTP or HTTPS traffic has been detected going out to malicious websites.
- SSL Plugins: All the plugins that refer to SSL or certificates have been grouped into these indicators.
- Web Internet Services: The “Web Internet Services” matrix component displays an overview of web services potentially in the environment and whether related vulnerabilities have been detected.
- Web Services Vulnerabilities by Port: The “Web Services Vulnerabilities by Port” matrix component provides insight into vulnerabilities by the listed service with a corresponding set of common ports.
- Hosts with Web Server Vulnerabilities by Plugin Family: The “Hosts with Web Server Vulnerabilities by Plugin Family” matrix component shows a detailed viewing of vulnerabilities of web technologies and potentially related software technologies.
- External URL Indicator: The “External URL Indicator” matrix component displays indicators for various groups of externally hosted URLs.