CVE-2020-10189: Deserialization Vulnerability in Zoho ManageEngine Desktop Central 10 Patched (SRC-2020-0011)

Zoho releases a patch for a critical remote code execution flaw in ManageEngine one day after the vulnerability was publicly disclosed.
Update 03/09/2020: Updated the Analysis section to include information on reports of active exploitation of this vulnerability.
Background
On March 5, Steven Seeley, an information security specialist at Source Incite, published an advisory for a vulnerability in Zoho ManageEngine Desktop Central. Desktop Central is a centralized management solution for a variety of devices – from personal computers (e.g., desktops, laptops) to mobile devices (e.g., smartphones, tablets). The vulnerability affects Desktop Central build 10.0.473 and below.
분석
CVE-2020-10189 is an untrusted deserialization vulnerability in Zoho ManageEngine Desktop Central. The vulnerability stems from an improper input validation in the FileStorage class. According to Seeley, an unauthenticated, remote attacker can abuse the lack of validation in the FileStorage class to upload a malicious file containing a serialized payload onto the vulnerable Desktop Central host. To trigger the untrusted deserialization, an attacker would then need to make a subsequent request for the file uploaded onto the vulnerable host. This would then grant the attacker arbitrary code execution with SYSTEM/root privileges. For more detail, please refer to the proof-of-concept section, which contains Seeley’s detailed breakdown of the vulnerability.
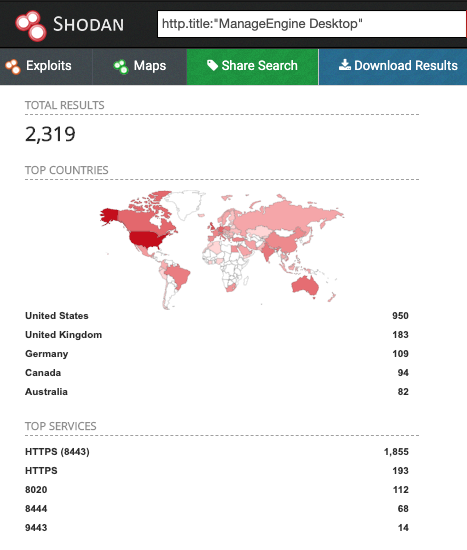
https://t.co/cCOrj1t6bo - "only" 2300+ of these online.....
— Nate Warfield (@n0x08) March 5, 2020
According to a Shodan search by Nate Warfield, senior security program manager at Microsoft, there are over 2,300 publicly accessible Desktop Central instances.
On March 9, we became aware of reports this vulnerability is now being actively exploited in the wild, including a list of indicators of compromise.
Active exploitation of Zoho ManageEngine (CVE-2020-10189 ) now seen in the wild - https://t.co/LeY8OnAvdR - Some additional IOCs @ https://t.co/IN1ubCXRvp
— chris doman (@chrisdoman) March 9, 2020
Proof of concept
Along with his advisory, Seeley published a proof-of-concept (PoC) for the vulnerability, which he shared in a tweet.
솔루션
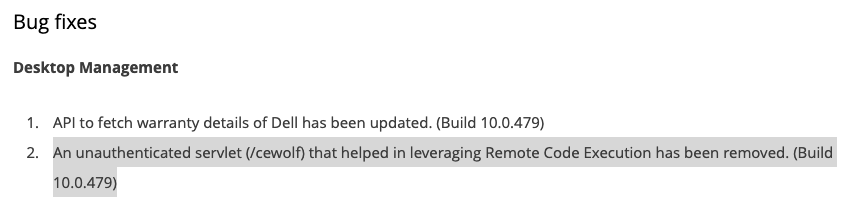
Zoho released a patch on March 6 to address this vulnerability in Desktop Central build 10.0.479. Users are strongly encouraged to patch as soon as possible by visiting ManageEngine’s service pack release page. The page also includes a link to download build 10.0.479.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
Get more information
- SRC-2020-0011: Source Incite Advisory for CVE-2020-10189
- SRC-2020-0011: Source Incite Proof-of-Concept for CVE-2020-10189
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

