CVE-2023-2868: Barracuda and FBI Recommend Replacing Email Security Gateway (ESG) Devices Immediately

Since October 2022, attackers have been exploiting a zero-day vulnerability in Barracuda Email Security Gateway devices, and both the vendor and the FBI urge customers to replace these devices immediately
Background
On May 19, Barracuda published an incident report that detailed an investigation into a zero-day vulnerability in its Email Security Gateway (ESG) appliances:
| CVE | Description | CVSSv3 | Severity |
|---|---|---|---|
| CVE-2023-2868 | Barracuda ESG Appliance Remote Command Injection Vulnerability | 9.8 | Critical |
Barracuda hired Mandiant to aid in its investigation into the vulnerability and identify indicators of compromise related to attacks linked to its exploitation.
Analysis
CVE-2023-2868 is a remote command injection vulnerability in Barracuda ESG appliances due to improper handling of emails with attachments. Specifically, the vulnerability is linked to the parsing logic used for Tape Archive files, also known as TAR files.
As part of the investigation, Mandiant discovered that attackers had been exploiting the vulnerability as a zero-day as early as October 2022.
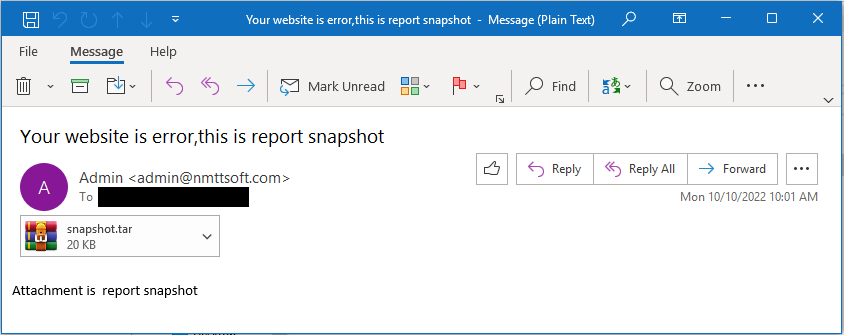
Image Source: Mandiant, June 2023
To exploit the vulnerability, an attacker would send a specially crafted TAR file containing a malicious payload within the filename. The specially crafted files could use a variety of file extensions including .tar, .dat and .jpg. Successful exploitation would result in remote code execution.
Both Mandiant and the Federal Bureau of Investigation (FBI) attribute the zero-day attacks exploiting CVE-2023-2868 to a People’s Republic of China (PRC) aligned threat actor. Mandiant refers to this group as UNC4841.
In these attacks, UNC4841 leveraged multiple backdoor malware families, dubbed SALTWATER, SEASPY, SEASIDE, SUBMARINE (DEPTHCHARGE), and WHIRLPOOL.
In a follow up blog post on August 29, Mandiant provided additional details from their investigation of the eight-month long campaign by UNC4841. Mandiant notes that since the patch was released on May 20, they did not observe any newly compromised ESG appliances. However the devices that were already compromised prior to patching revealed a number of sophisticated malicious scripts and activity used by the attackers to maintain persistence. These additional malware families are known as SKIPJACK and FOXTROT/FOXGLOVE. Mandiant’s blog post goes on further to describe how the attackers used these malware families to maintain persistence and, in some cases, move laterally in targeted networks after the public disclosure of CVE-2023-2868 by Barracuda.
For more details into the post exploitation activities associated with these attacks, including indicators of compromise (IOCs), please refer to Mandiant’s blog post from June 15 and follow up blog post from August 29.
Proof of concept
At the time this blog was published, several proofs-of-concept (PoCs) were publicly available for CVE-2023-2868. However, we strongly advise exercising caution when interacting with publicly available PoCs, as they may also be malicious in nature.
Solution
On May 20, Barracuda released security patches to “remediate the vulnerability.” The affected Barracuda ESG appliances include versions 5.1.3.001 through 9.2.0.006, while the fixed version released by Barracuda is version 9.2.0.008.
However, in an FBI flash alert (AC-000172-TT) published on August 23, the agency says that the “patches released by Barracuda in response to this CVE were ineffective” adding that they continue to “observe active intrusions and considers all affected Barracuda ESG appliances to be compromised and vulnerable to this exploit.”
Recommendations into the replacement of Barracuda ESG appliances
Following its investigation into the incident, Barracuda recommended the “immediate replacement of compromised ESG appliances, regardless of patch level.” This guidance was underscored by the FBI in its recent flash alert, as the agency “strongly advises all affected ESG appliances be isolated and replaced immediately.”
In a blog post from Mandiant on August 29, the firm states that their recommendations remain the same and that “victims impacted by this campaign should contact Barracuda support and replace the compromised appliance.”
Additionally, on August 29, the Cybersecurity and Infrastructure Security Agency (CISA) released additional IOCs to aid incident responders investigating exploitation of CVE-2023-2868.
Identifying affected systems
The following Tenable plugins are available to identify Barracuda ESG assets in customer environments as well as those vulnerable to CVE-2023-2868:
| Plugin ID | Name | Type | Requirements |
|---|---|---|---|
| 177507 | Barracuda Email Security Gateway Service Detection | Detection | HTTP Credentials |
| 177587 | Barracuda Email Security Gateway 9.2.0.008 Command Injection (CVE-2023-2868) | Version | HTTP Credentials |
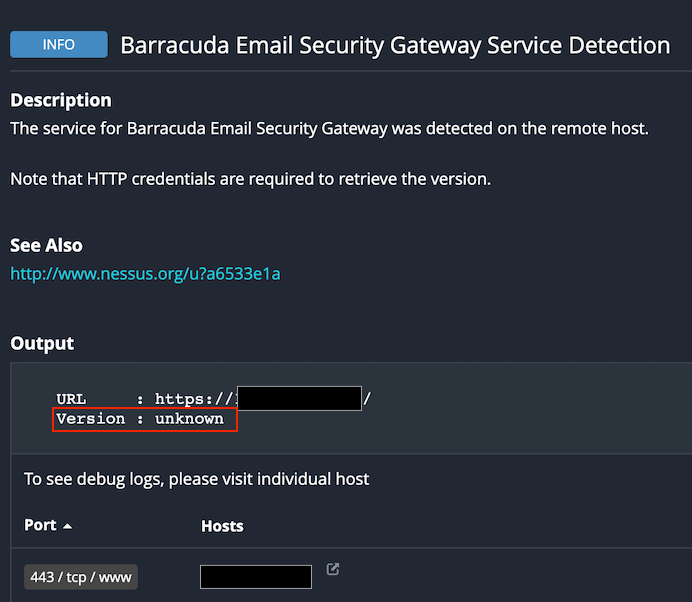
Please note that in order for the plugins to work, HTTP credentials are required to detect the version of the Barracuda appliance. Here is an example plugin output if HTTP credentials are NOT supplied:
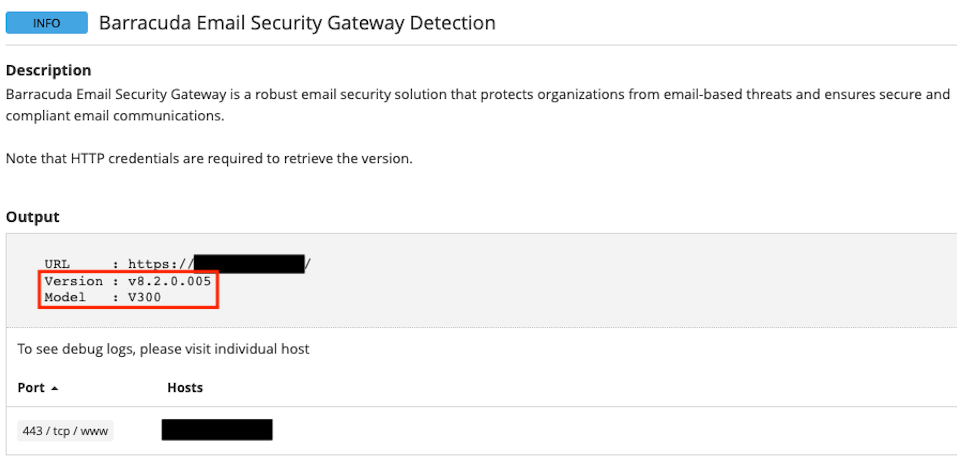
However, when HTTP credentials are supplied, the detection plugin will return version and model information for the ESG appliance:
We strongly encourage customers to scan for these devices on your networks by supplying HTTP credentials and to isolate these devices and replace them as soon as possible. For more information on configuring the scan policy for HTTP credentials, please refer to the applicable documentation below:
- Tenable Nessus
- Tenable Security Center (formerly Tenable.sc)
- Tenable Vulnerability Management (formerly Tenable.io)
Get more information
- Barracuda Incident Report from May 2023
- Barracuda Email Security Gateway Appliance (ESG) Vulnerability
- Mandiant: Barracuda ESG Zero-Day Vulnerability (CVE-2023-2868) Exploited Globally by Aggressive and Skilled Actor, Suspected Links to China
- Mandiant: Diving Deep into UNC4841 Operations Following Barracuda ESG Zero-Day Remediation (CVE-2023-2868)
- FBI Flash Alert: Suspected PRC Cyber Actors Continue to Globally Exploit Barracuda ESG Zero-Day Vulnerability (CVE-2023-2868)
- CISA Releases IOCs Associated with Malicious Barracuda Activity
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management



