Microsoft’s November 2020 Patch Tuesday Addresses 112 CVEs including CVE-2020-17087

Microsoft addressed over 112 CVEs in its November release, including a zero-day vulnerability in the Windows kernel that was exploited in the wild as part of a targeted attack.
Microsoft patched 112 CVEs in the November 2020 Patch Tuesday release, including 17 CVEs rated as critical. This month's Patch Tuesday release includes fixes for Microsoft Windows, Microsoft Office and Microsoft Office Services and Web Apps, Internet Explorer, Microsoft Edge (EdgeHTML-based), Microsoft Edge (Chromium-based), ChakraCore, Microsoft Exchange Server, Microsoft Dynamics, Microsoft Windows Codecs Library, Azure Sphere, Windows Defender, Microsoft Teams, Azure SDK, Azure DevOps, and Visual Studio.
As part of this month’s release, Microsoft has made a significant change to their Security Update Guide, as they will no longer provide vulnerability descriptions for each vulnerability. Rather, they are relying on the CVSS vectors to provide the contextual information regarding vulnerabilities. Without descriptions, some vulnerabilities will lack key details and context that could be used by administrators when considering how to prioritize updates or determining when mitigations can be used until they are ready to apply patches to critical infrastructure within their network.
CVE-2020-17087 | Windows Kernel Local Elevation of Privilege Vulnerability
CVE-2020-17087 is an elevation of privilege vulnerability in the Windows kernel Cryptography Driver, cng.sys, that was exploited in the wild as part of a vulnerability chain with CVE-2020-15999, a buffer overflow vulnerability in the FreeType 2 library used by Google Chrome. CVE-2020-17087 was used to escape Google Chrome’s sandbox in order to elevate privileges on the exploited system. This is the second vulnerability chain involving a Google Chrome vulnerability and a Windows elevation of privilege vulnerability exploited in the last year.
Chaining vulnerabilities is an important tactic for threat actors. While both CVE-2020-15999 and CVE-2020-17087 were exploited in the wild as zero-days, the Cybersecurity and Infrastructure Security Agency (CISA) published a joint advisory with the FBI last month that highlighted threat actors chaining unpatched vulnerabilities to gain initial access into a target environment and elevate privileges. Now that Google and Microsoft have patched these flaws, it is imperative for organizations to ensure they’ve applied these patches before threat actors begin to leverage them more broadly.
CVE-2020-17051 | Windows Network File System Remote Code Execution Vulnerability
CVE-2020-17051 is a critical remote code execution (RCE) vulnerability affecting the Windows Network File System (NFS). NFS is a file system protocol used for file sharing across multiple operating systems on a network. According to the limited information provided by Microsoft, the vulnerability appears to impact all supported versions of Windows and can be exploited without authentication or user interaction based on the CVSSv3 score of 9.8. In a blog post by McAfee, there is speculation about combining CVE-2020-17051 with CVE-2020-17056, a remote kernel data read vulnerability in NFS, in order to bypass address space layout randomization (ASLR), which could increase the probability of a remote exploit. Additionally, the blog post notes that it’s possible for CVE-2020-17051 to be wormable, assuming NFS has been configured to allow for anonymous write access. With Microsoft labeling this vulnerability as “Exploitation More Likely” under its Exploitability Index, we suggest that the organizations prioritize patches for both of these CVEs.
CVE-2020-17083 and CVE-2020-17084 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2020-17083 and CVE-2020-17084 are both RCE flaws within Microsoft Exchange Server. CVE-2020-17083 is scored as a CVSSv3 5.5 while CVE-2020-17084has a CVSSv3 score of 8.5. While both flaws are labeled as “Exploitation Less Likely,” from reviewing the CVSS score, it’s likely these vulnerabilities could be exploited by enticing a user to open a crafted email. The vulnerabilities are credited to Steven Seeley of Source Incite. While unconfirmed, it’s likely that these fixes are related to a bypass Seeley found for CVE-2020-16875. Seeley has noted on Twitter that the CVSS score for CVE-2020-17083 is incorrect and should be 8.5.
Maybe some of you are wondering where that blog post is regarding CVE-2020-16875? Well, it turns out I managed to bypass the patch.
— ϻг_ϻε (@steventseeley) October 2, 2020
Microsoft Exchange has continued to be a valuable target for attackers over the years and slow patching of Exchange servers has led to successful attacks against organizations. Our readers may recall CVE-2020-0688, which saw active exploration shortly after the patch was released in February of this year.
CVE-2020-17061 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2020-17061 is a RCE vulnerability in Microsoft SharePoint. A remote attacker could exploit this vulnerability to gain code execution privileges on the SharePoint server. According to the advisory, an attacker requires low level privileges in order to exploit the vulnerability.
In September and October, we saw a stream of patches for SharePoint RCE vulnerabilities. SharePoint is an attractive target for both researchers and threat actors. One of the most notable SharePoint vulnerabilities, CVE-2019-0604 has been actively exploited for well over a year now. While CVE-2020-17061 is not as severe as CVE-2019-0604, the regularity with which we’re seeing patches for SharePoint vulnerabilities should serve as a reminder for defenders to ensure they’re patching SharePoint regularly to reduce the potential attack surface for their organization.
CVE-2020-17042 | Windows Print Spooler Remote Code Execution Vulnerability
CVE-2020-17042 is an RCE vulnerability in the Windows Print Spooler. Despite receiving an Exploitability Index rating of “Exploitation Less Likely,” this vulnerability should be high up on any organization's patch priority list as it received a CVSSv3 score of 8.8. Although Microsoft does not provide any details on the flaw or conditions to exploit, it’s important to consider past flaws in the Windows Print Spooler. In August, CVE-2020-1337 was patched by Microsoft shortly after being discussed in presentations at both the Black Hat USA and DEF CON conferences. The presentations, A Decade After Stuxnet's Printer Vulnerability: Printing is Still the Stairway to Heaven from SafeBreach Labs discusses how a flaw in the Windows Print Spooler could be chained with additional vulnerabilities to compromise a host and further propagate across a network. With interest in the print spooler as an attack vector from security researchers, we anticipate to see further information on this in the near future.
Interestingly enough, this month brought a patch to CVE-2020-17001, an elevation of privilege flaw in the Windows Print Spooler reported to Microsoft by James Forshaw of Google’s Project Zero team. According to the details from Project Zero, this is a bypass of the patch for CVE-2020-1337. The vulnerability disclosure provides a proof-of-concept (PoC) and although the vulnerability received only a CVSSv3 score of 7.8, this vulnerability could be used in a chained attack scenario as evident by the abuse of CVE-2020-1337.
CVE-2020-17019, CVE-2020-17064, CVE-2020-17065, CVE-2020-17066 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2020-17019, CVE-2020-17064, CVE-2020-17065, and CVE-2020-17066 are RCE flaws within Microsoft Excel. Each of these flaws received a CVSSv3 score of 7.8. The CVSS metrics call out that user interaction is required in order to exploit the flaws, however this is a common scenario for Microsoft Office related flaws. We speculate that the path to exploitation requires that a user open a crafted file with an affected version of Microsoft Excel. These vulnerabilities are likely to be exploited in phishing attacks. Despite a lower exploitation probability, these updates are important to apply.
CVE-2020-17091 | Microsoft Teams Remote Code Execution Vulnerability
CVE-2020-17091 is a RCE vulnerability in Microsoft Teams, a platform used by businesses, small teams and schools for collaboration and distance learning. The vulnerability is credited to Matt Austin, director of security research at Contrast Security. In November 2019, Austin tweeted that he discovered a “one click RCE” in Microsoft Teams that he submitted to Microsoft on September 1, 2018 that was still an open case one year later.
I wanted to fully test this “Responsible Disclosure” theory so I submitted a one click RCE in Microsoft Teams to #msrc on Sep 01, 2018. It is still open. The disclosure policy of @taviso and others gets bugs fixed. This does not.
— Matt Austin (@mattaustin) November 30, 2019
Austin also tweeted a proof-of-concept video showing successful exploitation.
— Matt Austin (@mattaustin) November 30, 2019
It is unclear if CVE-2020-17091 is the same vulnerability, but since it is credited to the researcher, we surmise this might be the case.
Because Microsoft Teams has seen a 50% increase in daily active users, from 75 million to 115 million over the last year, it is extremely important to ensure your organization or your schools apply this patch as soon as possible.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains November 2020.
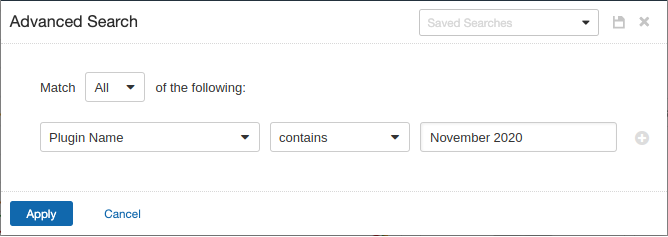
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example using March 2019 from Tenable.io:
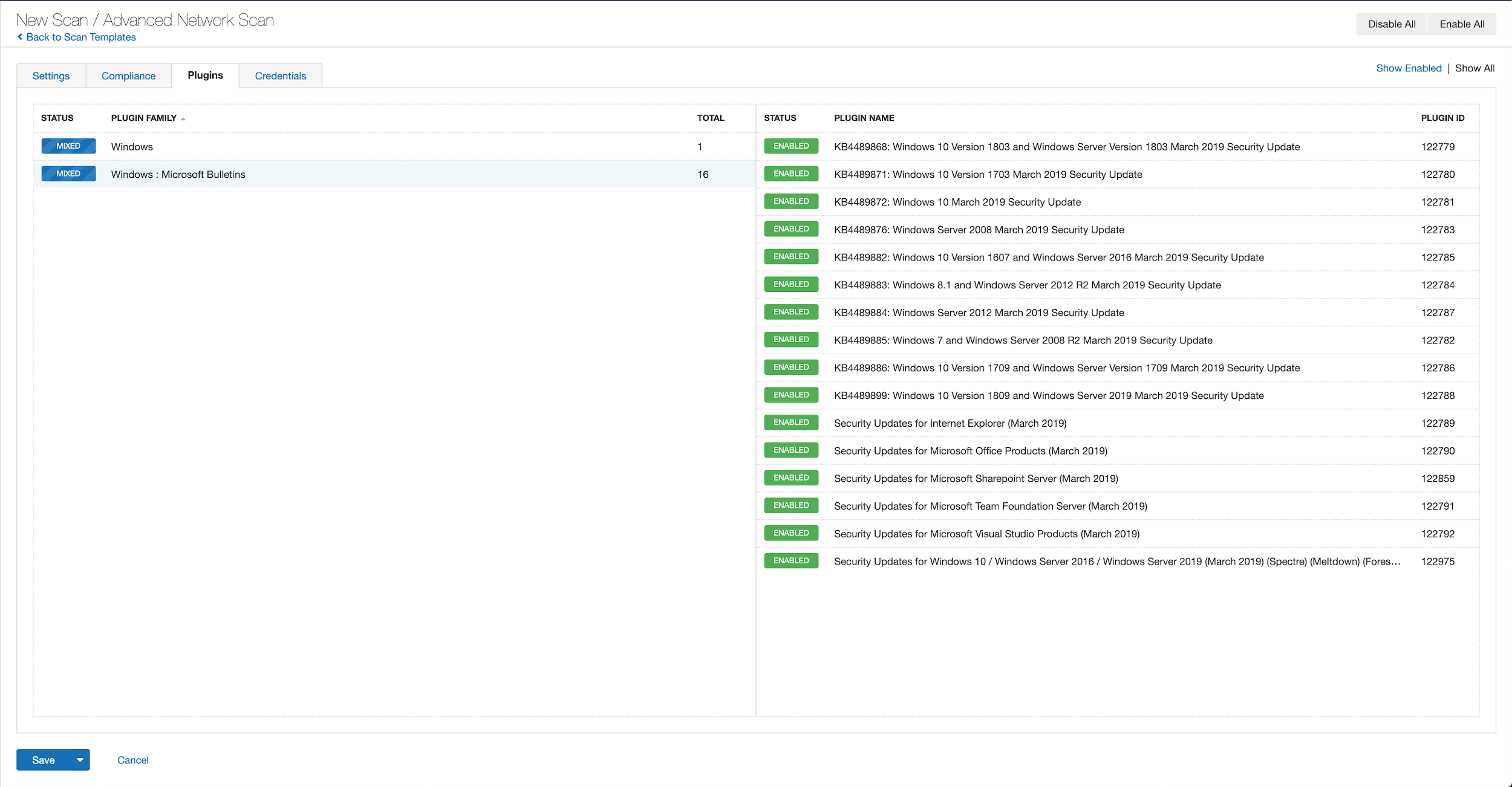
A list of all the plugins released for Tenable’s November 2020 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's November 2020 Security Updates
- Tenable plugins for Microsoft November 2020 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

