Microsoft’s July 2024 Patch Tuesday Addresses 138 CVEs (CVE-2024-38080, CVE-2024-38112)

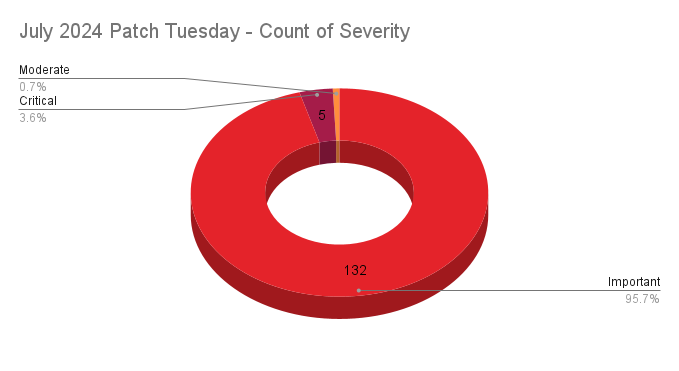
- 5Critical
- 132Important
- 1Moderate
- 0Low
Microsoft addresses 138 CVEs in its July 2024 Patch Tuesday release, with five critical vulnerabilities and three zero-day vulnerabilities, two of which were exploited in the wild.
Microsoft released 138 CVEs in July 2024 Patch Tuesday release, with five rated critical, 132 rated important and one rated moderate. Our counts omitted four vulnerabilities, two reported by GitHub, and one reported by CERT/CC and Arm each.
This month’s update includes patches for:
- .NET and Visual Studio
- Active Directory Federation Services
- Azure CycleCloud
- Azure DevOps
- Azure Kinect SDK
- Azure Network Watcher
- Line Printer Daemon Service (LPD)
- Microsoft Defender for IoT
- Microsoft Dynamics
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Streaming Service
- Microsoft WS-Discovery
- Microsoft Windows Codecs Library
- Microsoft WS-Discovery
- NDIS
- Role: Active Directory Certificate Services; Active Directory Domain Services
- Role: Windows Hyper-V
- SQL Server
- Windows BitLocker
- Windows COM Session
- Windows CoreMessaging
- Windows Cryptographic Services
- Windows DHCP Server
- Windows Distributed Transaction Coordinator
- Windows Enroll Engine
- Windows Fax and Scan Service
- Windows Filtering
- Windows Image Acquisition
- Windows Internet Connection Sharing (ICS)
- Windows iSCSI
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows LockDown Policy (WLDP)
- Windows Message Queuing
- Windows MSHTML Platform
- Windows MultiPoint Services
- Windows NTLM
- Windows Online Certificate Status Protocol (OCSP)
- Windows Performance Monitor
- Windows PowerShell
- Windows Remote Access Connection Manager
- Windows Remote Desktop
- Windows Remote Desktop Licensing Service
- Windows Secure Boot
- Windows Server Backup
- Windows TCP/IP
- Windows Themes
- Windows Win32 Kernel Subsystem
- Windows Win32K - GRFX
- Windows Win32K - ICOMP
- Windows Workstation Service
- XBox Crypto Graphic Services
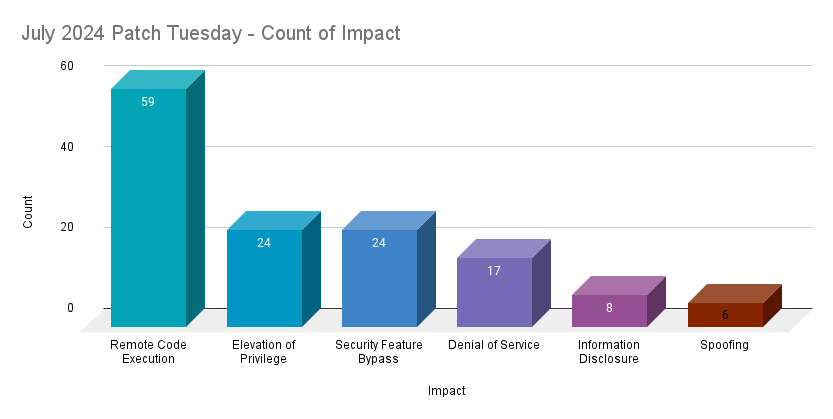
Remote Code Execution (RCE) vulnerabilities accounted for 42.8% of the vulnerabilities patched this month, followed by Elevation of Privilege (EoP) and Security Feature Bypass vulnerabilities at 17.4%.
CVE-2024-38080 | Windows Hyper-V Elevation of Privilege Vulnerability
CVE-2024-38080 is an EoP vulnerability in Microsoft Windows Hyper-V virtualization product. It was assigned a CVSSv3 score of 7.8 and is rated as important. A local, authenticated attacker could exploit this vulnerability to elevate to SYSTEM privileges.
According to Microsoft, this vulnerability was exploited in the wild as a zero-day. It was reported by a researcher that chose to remain Anonymous. No further details have been shared about the in-the-wild exploitation.
There have been 44 vulnerabilities in Windows Hyper-V that have been patched since 2022. This is the first Hyper-V vulnerability that has been exploited in the wild as a zero-day.
CVE-2024-38112 | Windows MSHTML Platform Spoofing Vulnerability
CVE-2024-38112 is a spoofing vulnerability in Windows MSHTML. It was assigned a CVSSv3 score of 7.5 and is rated important. An unauthenticated, remote attacker could exploit this vulnerability by convincing a potential target to open a malicious file. Microsoft notes that in order to successfully exploit this flaw, an attacker would also need to take “additional actions” to “prepare the target environment.”
According to Microsoft, this vulnerability was exploited in the wild as a zero-day. It was disclosed to Microsoft by Haifei Li of Check Point Research. At the time this blog post was published, no further details about in-the-wild exploitation were available. However, we anticipate further details will be made public soon.
CVE-2024-35264 |.NET and Visual Studio Remote Code Execution Vulnerability
CVE-2024-35264 is a RCE vulnerability affecting.NET and Visual Studio. It was assigned a CVSSv3 score of 8.1 and is the third Microsoft zero-day vulnerability patched this month. While it was not exploited in the wild, details were made public prior to the release of a patch. According to the advisory, exploitation requires an attacker to win a race condition and the exploitability reflects this as it is rated as “Exploitation Less Likely.”
CVE-2024-38060 | Windows Imaging Component Remote Code Execution Vulnerability
CVE-2024-38060 is a RCE vulnerability affecting the Windows Imaging Component, a framework used for processing images. Microsoft rates this vulnerability as “Exploitation More Likely” and assigned a CVSSv3 score of 8.8 as well as a critical severity rating. Exploitation of this flaw requires an attacker to be authenticated and utilize this access in order to upload a malicious Tag Image File Format (TIFF) file, an image type used for graphics.
CVE-2024-38059 and CVE-2024-38066 | Windows Win32k Elevation of Privilege Vulnerability
CVE-2024-38059 and CVE-2024-38066 are EoP vulnerabilities affecting Windows Win32k, a core kernel-side driver used in Windows. They were both assigned CVSSv3 scores of 7.8 and are rated as important. An attacker could exploit these vulnerabilities as part of post-compromise activity to elevate privileges to SYSTEM. Microsoft rates these vulnerabilities as “Exploitation More Likely.”
CVE-2024-38021 | Microsoft Office Remote Code Execution Vulnerability
CVE-2024-38021 is a RCE vulnerability affecting Microsoft Office 2016. This vulnerability was assigned a CVSSv3 score of 8.8 and rated as “Exploitation More Likely.” Successful exploitation would allow an attacker to gain elevated privileges, including write, read and delete functionality. MIcrosoft notes that exploitation requires an attacker to create a malicious link that can bypass Protected View Protocol. Based on Microsoft’s description, an attacker would have to entice a user into clicking the link, likely by sending it to an unsuspecting user in a phishing attack. This would result in the attacker gaining access to local NTLM credential information which could be utilized for elevated access to achieve RCE.
38 CVEs | Microsoft OLE DB Driver and SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability
This month's release included 38 CVEs for RCEs affecting SQL Server Native Client OLE DB Provider and the OLE DB Driver for SQL Server. All of these CVEs received CVSSv3 scores of 8.8 and were rated as “Exploitation Less Likely.” Successful exploitation of these vulnerabilities can be achieved by convincing an authenticated user into connecting to a malicious SQL server database using an affected driver. A full list of the CVEs are included in the table below.
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2024-20701 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21303 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21308 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21317 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21331 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21332 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21333 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21335 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21373 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21398 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21414 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21415 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21425 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21428 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-21449 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-28928 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-35256 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-35271 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-35272 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37318 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37319 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37320 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37321 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37322 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37323 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37324 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37326 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37327 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37328 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37329 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37330 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37331 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37332 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37333 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37334 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-37336 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-38087 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
| CVE-2024-38088 | SQL Server Native Client OLE DB Provider Remote Code Execution Vulnerability | 8.8 |
Tenable Solutions
A list of all the plugins released for Microsoft’s July 2024 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's July 2024 Security Updates
- Tenable plugins for Microsoft July 2024 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management


