One Year Later: What Can We Learn from Zerologon?

In a year of headline-making vulnerabilities and incidents, Zerologon (CVE-2020-1472) stands out due to its widespread adoption by threat actors and its checkered disclosure timeline.
In our Threat Landscape Retrospective (TLR) published earlier this year, the Tenable Security Response Team (SRT) highlighted CVE-2020-1472, aka Zerologon, as one of the Top Five Vulnerabilities of 2020.

However, Zerologon had humble beginnings: It received limited mention in most Patch Tuesday analyses when it was initially fixed in August 2020 but, by the end of the year, Zerologon was featured in several government alerts and had been adopted by threat actors of various motivations and capabilities. Zerologon was one of the top exploited vulnerabilities of 2020, according to a recent joint cybersecurity alert from international government agencies.
If vulnerabilities had Cinderella stories, this might be one. How did this vulnerability initially get lost in the shuffle and what can security professionals learn from this to avoid any future scrambles like the one experienced at the end of summer 2020?
Priority overload: 2020’s vulnerability season
You might have blocked it from your memory, or it may have been overwritten by the many other major news cycles we’ve experienced since, but the summer of 2020 was an exhaustingly busy few months. Just in the scheduled, recurring security releases from Oracle, Microsoft and Adobe, over 800 vulnerabilities were added to prioritization queues between July 14 and September 10, 2020. But, of course, it’s never just the scheduled releases. In the months surrounding the disclosure of CVE-2020-1472 and the publication of Secura’s white paper, the Security Response Team reported on a dozen notable vulnerabilities.
Source: Tenable, August 2021
To get a more detailed overview of the 2020 Vulnerability Season and how it fits into the larger security landscape, read the TLR.
Patch Tuesday: August 2020
So that’s everything that was happening around August Patch Tuesday. Let’s take a moment to examine that release itself. Microsoft patched 120 CVEs, breaking 100 CVEs for the sixth month in a row. Seventeen of the CVEs were rated Critical, seven as “Exploitation More Likely” and two vulnerabilities (CVE-2020-1464 and CVE-2020-1380) were under active exploitation. More than half (61) of the CVEs were Elevation of Privilege (EoP), though the actively exploited vulnerabilities received the bulk of the attention in third-party analysis of the Patch Tuesday release.
Now that we have a better understanding of the context surrounding the initial release of CVE-2020-1472, let’s examine the vulnerability itself and how its disclosure proceeded.
About CVE-2020-1472: sneaky updates cause problems
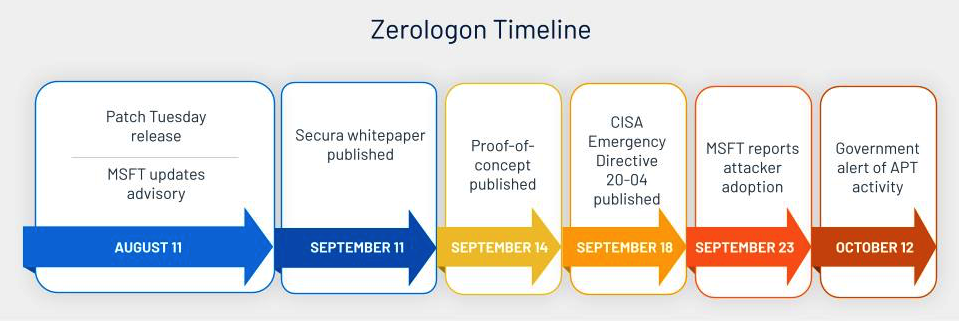
Source: Tenable, August 2021
CVE-2020-1472 is an elevation of privilege vulnerability in Microsoft's Netlogon Remote Protocol (MS-NRPC). This protocol is used to maintain relationships of domain controllers (DCs) within and across domains. Critically, MS-NRPC is also used to manage account changes for DCs, like passwords. The flaw exists because of a flaw in how MS-NRPC implements AES-CFB8 encryption. Because this is a local privilege escalation flaw, an attacker needs to be on the same local area network (LAN) as their target.
Active Directory (AD) is a target of serious concern with Zerologon. If an attacker was able to exploit it against AD, they could impersonate any machine on the network, reset the domain controller’s administrator password or launch ransomware attacks against the entire network.
Initially, CVE-2020-1472 was published with a CVSSv3 score of 8.8 and “Exploitation Less Likely” designation, according to the Microsoft Exploitability Index. TrendMicro Zero Day Initiative did point out that a critical rating for an EoP is “rare” and that might have been our first and only hint that something was up. However, two other EoP vulnerabilities in this release (CVE-2020-1509, CVE-2020-1585) also received 8.8 CVSSv3 scores. The same day of the Patch Tuesday release, Microsoft updated the CVSSv3 score for CVE-2020-1472 to 10.0 and upgraded it to “Exploitation More Likely.”
This surreptitious update is likely a major reason CVE-2020-1472 flew under the radar initially. You can see in the image below that the update on Microsoft’s Security Update Guide is listed before the information was published. Version 1.1 is listed as preceding version 1.0. Analysts and reporters jump on Patch Tuesday as quickly as possible looking for the next “big” vulnerability and likely missed this important revision.
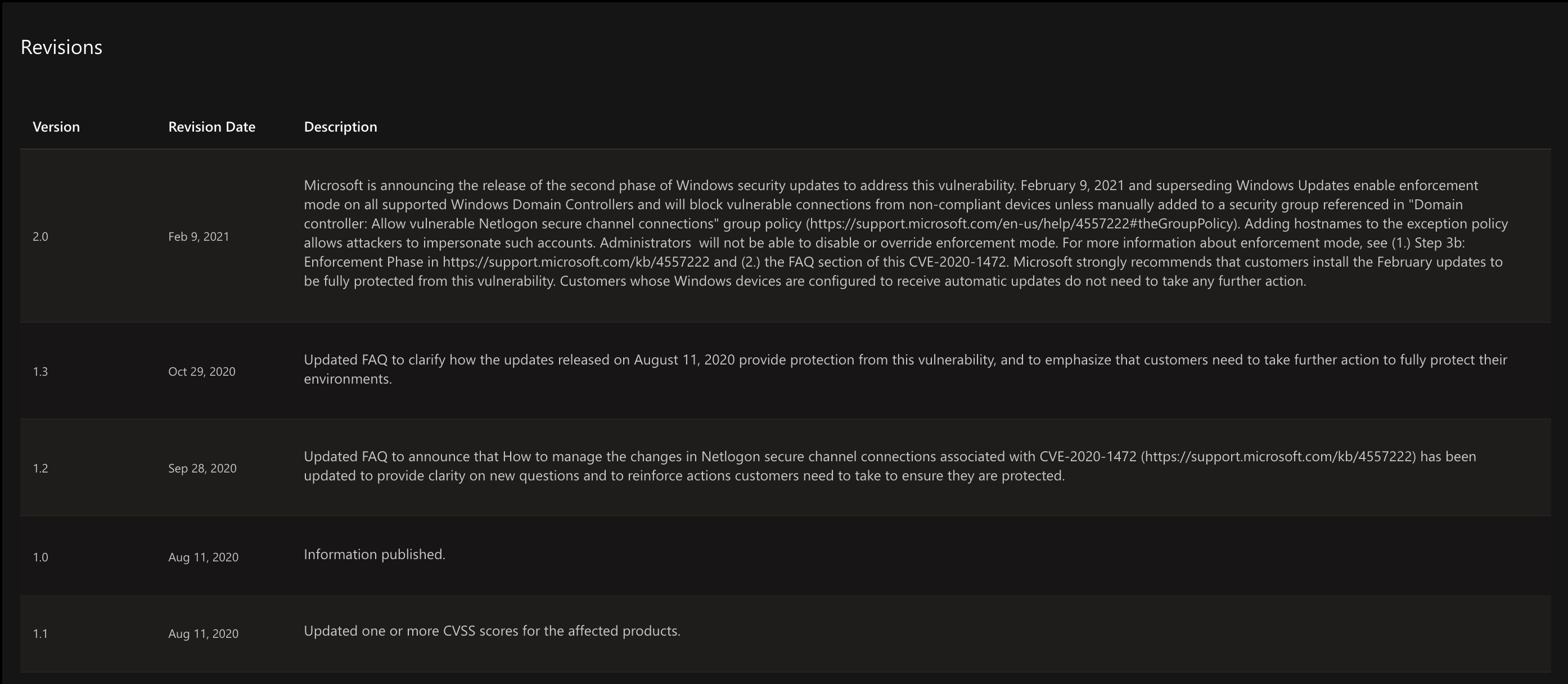
Source: Microsoft, retrieved August 2021
It wasn’t until September, when researchers at Secura published more details about the vulnerability and gave it a name, Zerologon, that the community at large took notice. The additional information from Secura allowed analysts and researchers to understand the full scope and impact of the vulnerability. This is also where we began to see the 10.0 CVSSv3 score included in coverage. Several proofs-of-concept (PoC) were published for Zerologon that improved upon the initial test tool released by Secura. By October, news broke that advanced persistent threat actors and ransomware groups were leveraging Zerologon in attack chains.
Tom Tervoot of Secura recently spoke at Black Hat USA 2021 about his discovery of Zerologon and Microsoft’s patch. In this presentation, he alluded to the fact that the one month delay in publishing his whitepaper and testing tool was decided in agreement with Microsoft and implied it was intended to give defenders time to patch.
Coverage of CVE-2020-1472
Overall, CVE-2020-1472 wasn’t prominently featured in Patch Tuesday coverage by vendors and the media. It was mostly included as an “also patched” later in analyses. It appears much of the initial coverage for CVE-2020-1472 was driven by commentary from Trend Micro Zero Day Initiative.
Based on the information available at the time, it’s reasonable that most of us focused attention on CVE-2020-1464 and CVE-2020-1380 while basically putting a pin in CVE-2020-1472 until more information became available.
Secura didn’t offer any rationale for its delayed publication date until last week and Microsoft made no mention of the CVSS score change beyond the somewhat confusing version history of the Security Update Guide. Had accurate and complete information about Zerologon been available from the beginning, the industry would have likely sounded a louder alarm much earlier.
Takeaways
What can we learn from this situation? Can we extract useful actions to take in the future to avoid an apparent oversight?
I'd love to offer a magic, quantitative solution based on this vulnerability: if [list of factors], then exploit. Unfortunately that is not possible; this all as much an art as it is a science. Without accurate information, it's nearly impossible to predict exactly which vulnerabilities out of the thousands disclosed every year will be widely, or even narrowly exploited. Attackers are often creatures of habit but they have so many vulnerabilities from which to choose.
Publicly available PoCs are a strong indicator that a given vulnerability will be adopted by attackers because attackers are opportunistic and will happily gain value off someone else’s work. However, we've seen lately that some won't hesitate to develop zero-days if the price is right. PoCs can arrive significantly after a patch, as we've seen, and defenders waiting for a public PoC is the opposite of ideal.
One thing that we can derive from this, though it’s not groundbreaking, is the value EoP vulnerabilities may have, and a consideration for which vulnerabilities can be chained to elevate privileges or move laterally within target networks. This is not new, we’ve written about it before. Based on sources like government alerts on threat actor activity, we know that remote code execution (RCE) vulnerabilities still dominate, but Zerologon was specifically called out for being used in several campaigns, regardless of initial access methods.
From this incident we know to look out for:
- Unpatched vulnerabilities with widely publicized PoCs
- Ubiquitous programs/functions (a la Print Spooler)
- Microsoft dominates the vulnerabilities used by threat groups because it is so widely deployed.
- Elevation and lateral movement
Nothing cutting-edge here.
Unfortunately, the main action I can see here isn’t for defenders, it’s for the vendors. The primary reason for this situation was the scoring discrepancy of CVE-2020-1472 when it was initially disclosed. Had Microsoft been more communicative about the score change, defenders would have had accurate information with which to perform initial prioritization. At first analysis, based on the information provided initially by Microsoft, this appeared to be a fairly average EoP vulnerability. The surreptitious update meant that most people didn’t reexamine the advisory until a month later. The early birds got inaccurate information, unfortunately, thereby missing the metaphorical worm.
This case illustrates another side of the “coordinated disclosure” coin. Researcher blog posts, white papers, and even tweets, can provide helpful context missing from vendor advisories. They may even point out where a vendor advisory was inaccurate.
We saw a similar issue with the Print Spooler vulnerabilities this summer.
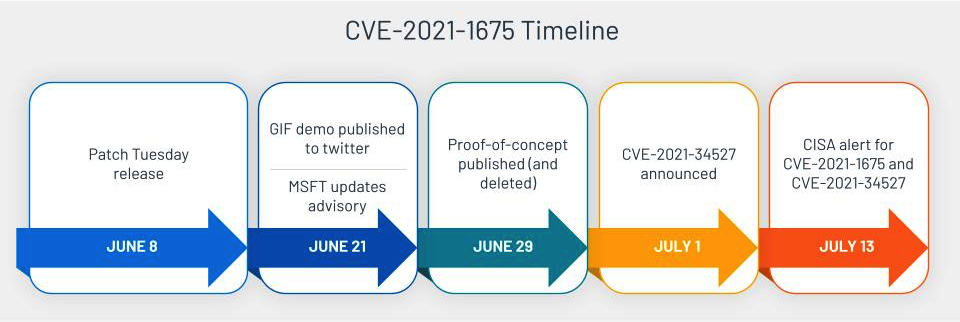
Source: Tenable, August 2021
Microsoft’s initial advisory for CVE-2021-1675 didn’t accurately describe the vulnerability, listing just an EoP when it was actually RCE. It even followed the same delayed PoC to wide scale exploitation to government alert timeline pretty closely. There were other complicating factors, but those aren’t as relevant here.
Conclusion
The lack of transparency from Microsoft in these situations is an ongoing issue, we can only speculate about how and why things transpired as they did. Confusion like this may only be more likely now that Microsoft has removed Executive Summaries from the Security Update Guides. Defenders rely on accurate, timely information from vendors in order to make effective prioritization decisions. The less information they receive or the more inaccurate it is, the harder it gets for the industry to defend from attackers.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability can be found here. Tenable released a remote check plugin for Zerologon that can be used against DCs to test whether or not they’re exploitable. Please note that this plugin requires disabling the “Only use credentials provided by the user” option under Assessment Settings.
Get more information
- Tenable Blog: Microsoft Finalizes Patch for Zerologon to Enable Enforcement Mode by Default
- Tenable Blog: 'Zerologon' Vulnerability in Netlogon Could Allow Attackers to Hijack Windows Domain Controller
- Tenable Blog: Microsoft’s August 2020 Patch Tuesday Addresses 120 CVEs (CVE-2020-1337)
- Secura Whitepaper
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


