CVE-2021-41773: Path Traversal Zero-Day in Apache HTTP Server Exploited

The Apache HTTP Server Project patched a path traversal vulnerability introduced less than a month ago that has been exploited in the wild.
Update October 7: The Solution section has been updated to reflect the secondary fix the Apache HTTP Server Project released.
Background
On October 5, the Apache HTTP Server Project patched CVE-2021-41773, a path traversal and file disclosure vulnerability in Apache HTTP Server, an open-source web server for Unix and Windows that is among the most widely used web servers. According to the security advisory, CVE-2021-41773 has been exploited in the wild as a zero-day. The vulnerability was disclosed to the Apache HTTP Server Project on September 29 by Ash Daulton and the cPanel Security Team. However, the advisory does not indicate when exploitation of CVE-2021-41773 was detected, but it stands to reason that the exploitation drove the expedited release of a patch.
If you use Apache HTTP Server 2.4.49 (only that version), you should update to 2.4.50 now due to CVE-2021-41773, a nasty 0-day path traversal vulnerability https://t.co/2QiV4h77B4
— Mark J Cox (@iamamoose) October 5, 2021
Analysis
CVE-2021-41773 was introduced into Apache HTTP Server by a change made to path normalization in version 2.4.49, which was released on September 15. This vulnerability only impacts Apache HTTP Server version 2.4.49 with the “require all denied” access control configuration disabled.
In a default install of 2.4.49 you'll only be able to access things in the document root or cgi-bin directories
— Mark J Cox (@iamamoose) October 5, 2021
Successful exploitation would give a remote attacker access to arbitrary files outside of the document root on the vulnerable web server. According to the advisory, this flaw could also leak “the source of interpreted files like CGI scripts” which may contain sensitive information attackers can exploit for further attacks.
According to a Shodan search, just under 112,000 Apache HTTP Servers are running the vulnerable version. However, other vulnerable web servers might be configured to not display version information.
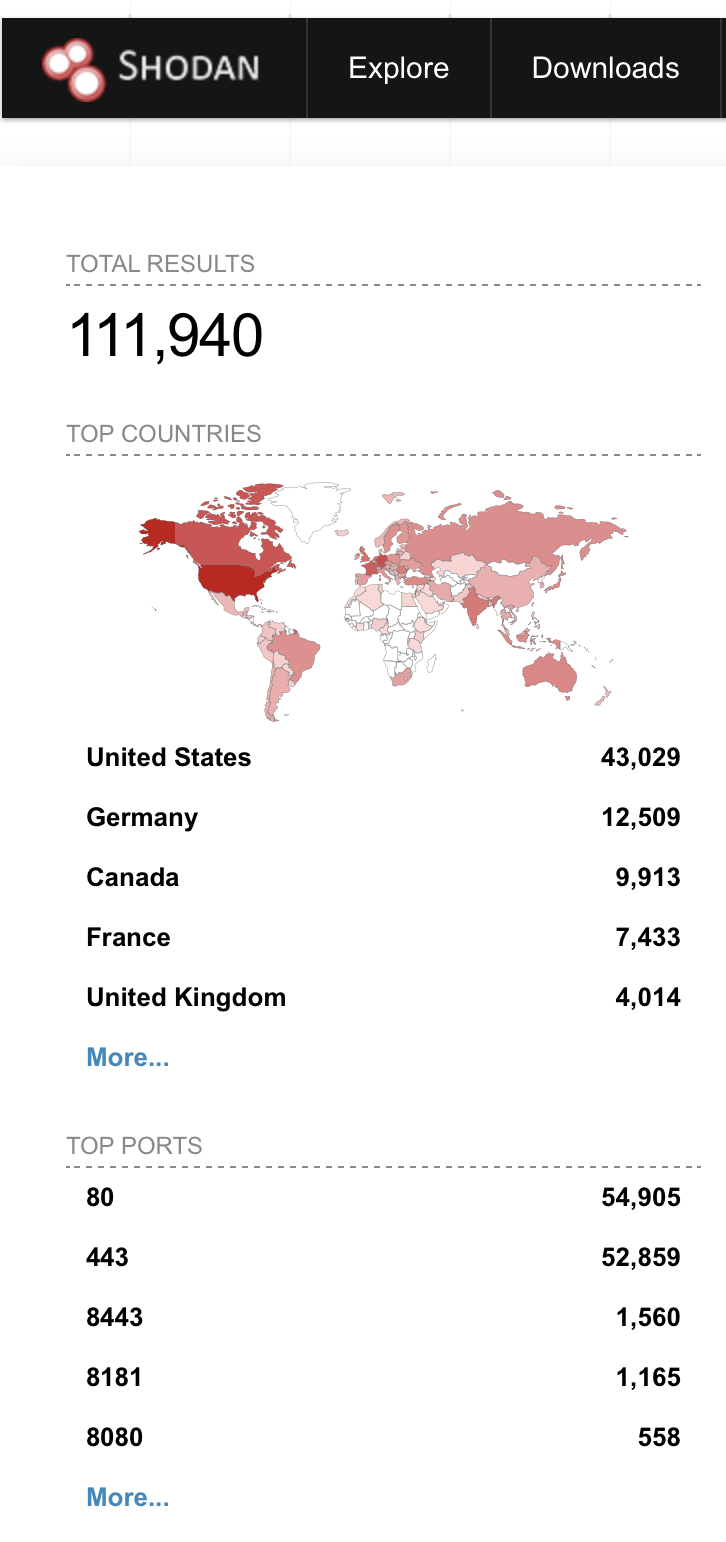
Source: Shodan, October 2021
In the same release, the Apache Server HTTP Project addressed CVE-2021-41524, a null pointer dereference vulnerability which could lead to a denial-of-service condition that also only impacts version 2.4.49.
Proof of concept
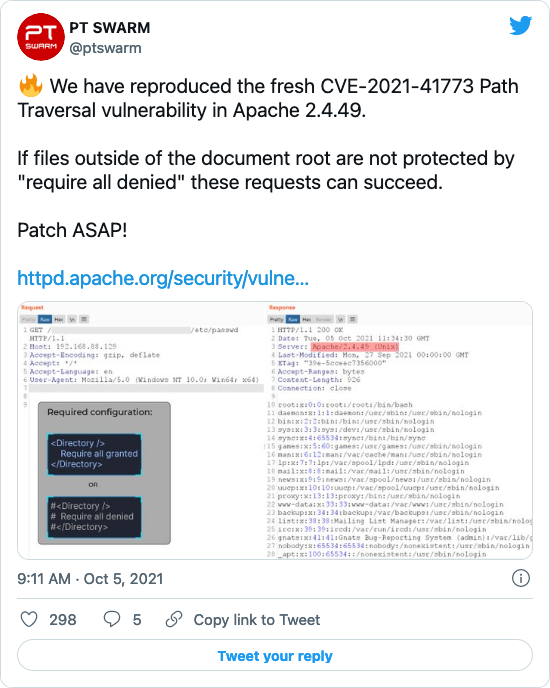
Positive Technologies Offensive Team, PT Swarm, announced on Twitter that they had reproduced the vulnerability. Shortly after, another user replied with the proof-of-concept (PoC) payload. Other PoCs have been shared on Twitter and we expect working exploit scripts will be published shortly.
Solution
All users should ensure that they update to the latest version of Apache HTTP Server. On October 7, the Apache HTTP Server Project released version 2.4.51 because the original release (2.4.50) didn’t fully address CVE-2021-41773. Because Apache HTTP Server 2.4.49 was released on September 15, 2021, there is a chance some users have not yet updated to the vulnerable versions.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
Get more information
- Apache HTTP Server Project Advisory
- Open Web Application Security Project (OWASP) guide on Path Traversal
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


