CVE-2023-20269: Zero-Day Vulnerability in Cisco Adaptive Security Appliance and Firepower Threat Defense Reportedly Exploited by Ransomware Groups

Ransomware groups including LockBit and Akira are reportedly exploiting a zero-day vulnerability in Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) appliances with VPN functionality enabled.
Background
On September 6, Cisco published an advisory for a zero-day vulnerability in the software for its Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) appliances that has been reportedly exploited in the wild:
| CVE | Description | CVSSv3 | VPR* |
|---|---|---|---|
| CVE-2023-20269 | Cisco ASA and FTD Software Remote Access VPN Unauthorized Access Vulnerability | 5.0 | 3.2 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on September 11 and reflects VPR at that time.
Analysis
CVE-2023-20269 is an unauthorized access vulnerability in the remote access VPN feature of the Cisco ASA and FTD software. According to Cisco, the vulnerability exists due to the “improper separation of authentication, authorization, and accounting (AAA) between the remote access VPN feature and the HTTPS management and site-to-site VPN features.”
Exploitation is not considered straightforward, as there are prerequisites required in each scenario for an attack to be successful.
Scenario #1: Brute force attack
A remote, unauthenticated attacker can attempt to brute-force username and passwords for the vulnerable system. In order for exploitation to occur, the vulnerable system needs to contain one user with a password in the local database or the HTTPS management authentication points back to a valid AAA server. In addition, either SSL VPN or IKEv2 VPN must be enabled on at least one interface. Scenario #2: Clientless SSL VPN Session
A remote, authenticated attacker using valid credentials establishes a “clientless SSL VPN session with an unauthorized user.”
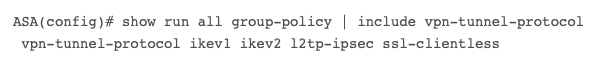
As noted in the scenario, the attacker must first possess valid credentials found in the local database or AAA server used for HTTPS management authentication, either through a brute force attack or using stolen credentials purchased from the dark web. The targeted system must be running a vulnerable version of Cisco ASA software, which includes versions 9.16 and below. The SSL VPN feature must be enabled on at least one interface and the DfltGrpPolicy group policy must include the clientless SSL VPN protocol.
LockBit and Akira ransomware groups have been targeting Cisco ASA systems
On August 24, Cisco’s Product Security Incident Response Team (PSIRT) published a blog post noting that the Akira ransomware group and its affiliates have been targeting Cisco VPNs as far back as March 2023, especially those systems that have not been configured with multi-factor authentication (MFA). Additionally, the LockBit ransomware group has also been linked to attacks against Cisco ASA systems not protected with MFA.
Ransomware groups and their affiliates utilize a myriad of ways to breach organizations, including through the exploitation of both known and zero-day vulnerabilities. For more insights into ransomware and the various players involved, please read our report called “The Ransomware Ecosystem.”
SSL VPNs continue to provide a reliable doorway for attacks
For the last few years, the Tenable Security Response Team (SRT) has been warning that SSL VPNs are an ideal and reliable doorway for attackers to breach organizations. There have been several notable vulnerabilities in a variety of SSL VPN systems including Citrix, Pulse Secure and Fortinet. The discovery of attacks against Cisco ASA and FTD systems reportedly using CVE-2023-20269 serves as an important reminder of the importance of safeguarding SSL VPNs from attacks conducted by ransomware groups and other cybercriminals.
Proof of concept
At the time this blog post was published, there was no public proof-of-concept (PoC) for CVE-2023-20269.
Solution
As of September 11, there were no fixed versions of Cisco ASA or FTD software that address this vulnerability. Instead, Cisco has shared a variety of workarounds to help thwart exploitation attempts.
The following Cisco products are not affected by CVE-2023-20269:
- Firepower Management Center (FMC) Software
- FXOS Software
- IOS Software
- IOS XE Software
- IOS XR Software
- NX-OS Software
Additionally, Cisco has shared indicators of compromise that can be used to determine if attempts to exploit the device have been observed or have been successful.
Identifying affected systems
A list of Tenable plugins to identify can be located on the individual CVE page for CVE-2023-20269 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
Presently, Plugin ID 181183 is available for CVE-2023-20269 and can be used to help identify vulnerable systems based on the configuration requirements outlined in Cisco’s advisory.
Additionally, the following detection plugins can be used to identify ASA and FTD devices in your environment including those with SSL VPN enabled:
Get more information
- Cisco Security Advisory for CVE-2023-20269
- Cisco PSIRT Blog Post on Akira Ransomware Targeting VPNs without MFA
- TechTarget: Cisco VPNs under attack via Akira, LockBit ransomware
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management



