Microsoft’s December 2023 Patch Tuesday Addresses 33 CVEs (CVE-2023-36019)

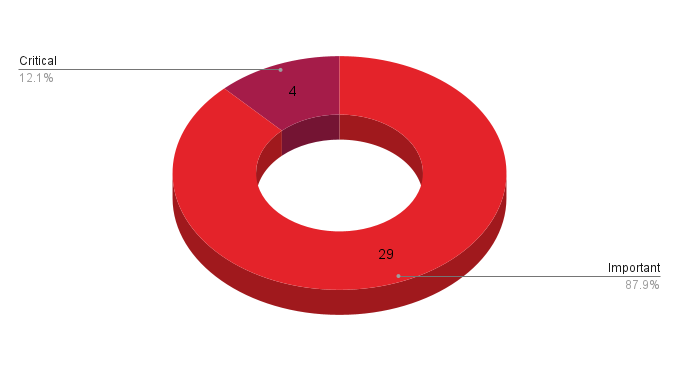
- 4Critical
- 29Important
- 0Moderate
- 0Low
Microsoft addresses 33 CVEs in its December 2023 Patch Tuesday release, with no zero-day vulnerabilities disclosed this month.
Microsoft patched 33 CVEs in its December 2023 Patch Tuesday release, with four rated critical and 29 rated as important. Our count omitted CVE-2023-20588, a CVE assigned by AMD to address speculative leaks in some AMD processors. A separate advisory from AMD is available with more information on the vulnerability.
This month’s update includes patches for:
- Azure Connected Machine Agent
- Azure Machine Learning
- Microsoft Bluetooth Driver
- Microsoft Dynamics
- Microsoft Office Outlook
- Microsoft Office Word
- Microsoft Power Platform Connector
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows DNS
- Windows Cloud Files Mini Filter Driver
- Windows Defender
- Windows DHCP Server
- Windows DPAPI (Data Protection Application Programming Interface)
- Windows Internet Connection Sharing (ICS)
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Media
- Windows MSHTML Platform
- Windows ODBC Driver
- Windows Telephony Server
- Windows USB Mass Storage Class Driver
- Windows Win32K
- XAML Diagnostics
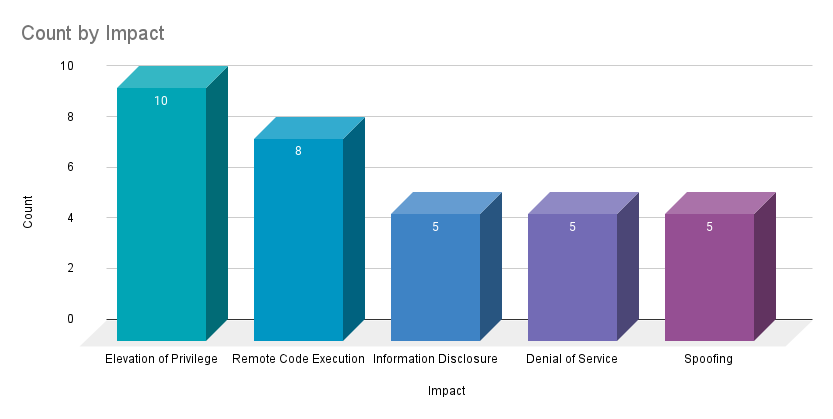
Elevation of privilege (EoP) vulnerabilities accounted for 30.3% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 24.2%.
CVE-2023-36019 | Microsoft Power Platform Connector Spoofing Vulnerability
CVE-2023-36019 is a spoofing vulnerability in the Microsoft Power Platform Connector. It was assigned a CVSSv3 score of 9.6 and is rated “Exploitation Less Likely” according to Microsoft’s Exploitability Index. This vulnerability relates to custom connectors, specifically the per-connector redirect URI. Microsoft says that an attacker could exploit this vulnerability to spoof a legitimate link or file to direct a victim to a malicious link or application.
This vulnerability has been mitigated as of November 17, as Microsoft has required that any new custom connectors using OAuth 2.0 authentication will be assigned a per-connector redirect URI automatically. However, existing connectors will need to be updated to use per-connector redirect URIs before February 17th, 2024.
CVE-2023-36019 shares some similarities in areas of research into Microsoft Power Platform conducted by researchers here at Tenable. In July, Tenable Research disclosed a vulnerability allowing unauthorized access to cross-tenant applications in Microsoft Power Platform. The issue was reported to Microsoft, who implemented solutions to address the issue. Additional vulnerabilities affecting Microsoft Power Apps were also reported to Microsoft earlier this year, including stored cross-site scripting (XSS) and multiple input-validation vulnerabilities. For more information on vulnerabilities discovered by Tenable, please review our Tenable Research Advisories.
CVE-2023-35641 and CVE-2023-35630 | Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
CVE-2023-35641 and CVE-2023-35630 are RCE vulnerabilities affecting the Internet Connection Sharing service in Windows, a service that allows an internet connected device to share its connection with other devices on a local area network. Both vulnerabilities were assigned CVSSv3 scores of 8.8 and a maximum severity rating of critical.
Exploitation of CVE-2023-35641, which Microsoft rated as “Exploitation More Likely,” can be achieved by sending a specially crafted DHCP message to a server running the ICS service. Exploitation of CVE-2023-35630, which Microsoft rated as “Exploitation Less Likely,” requires an attacker to modify the length field in a DHCPv6 message. Both of these vulnerabilities are credited to researchers at Kunlun Lab and an anonymous researcher.
CVE-2023-36696 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
CVE-2023-36696 is an EoP vulnerability in the Microsoft Windows Cloud Files Mini Filter Driver (cldflt.sys). It was assigned a CVSSv3 score of 7.8 and is rated as important and “Exploitation More Likely.” An attacker could exploit this vulnerability as part of post-compromise activity to elevate privileges to SYSTEM.
This flaw was reported to Microsoft by security researcher Rancho Ice. This is Ice’s second EoP vulnerability in the Cloud Files Mini Filter Driver disclosed to Microsoft in 2023 and is the sixth EoP vulnerability in the Cloud Files Mini Filter Driver disclosed in 2023 and the eight in the last two years.
Last month, Microsoft patched another EoP in the Cloud Files Mini Filter Driver (CVE-2023-36036), which was the first Windows Cloud Files Mini Filter Driver vulnerability to be exploited in the wild as a zero-day in 2023.
CVE-2023-35628 | Windows MSHTML Platform Remote Code Execution Vulnerability
CVE-2023-35628 is a RCE vulnerability affecting the Windows MSHTML platform. The vulnerability was assigned a CVSSv3 score of 8.1 and is rated as “Exploitation More Likely.” According to Microsoft, an attacker could exploit this vulnerability by sending a specifically crafted email which will automatically be processed when it is retrieved by Microsoft Outlook. Exploitation occurs before the email is viewed in the Preview Pane. While this is a critical vulnerability, Microsoft does note that successful exploitation would require the attacker to use “complex memory shaping techniques,” which may limit the successful use of this vulnerability to very skilled attackers.
Tenable Solutions
A list of all the plugins released for Tenable’s December 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's December 2023 Security Updates
- Tenable plugins for Microsoft December 2023 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management


